As the threat landscape continues to evolve, businesses are turning to Security-as-a-Service (SaaS) providers for comprehensive cybersecurity solutions. These providers offer a range of services to protect a company’s network, data, and identity from potential threats.
Managed security services offered by SaaS providers include real-time monitoring and incident response to quickly identify and mitigate any potential security breaches. This proactive approach ensures that businesses have the necessary protection to safeguard their sensitive information.
One of the key advantages of SaaS providers is their ability to offer cloud-based security solutions. This allows businesses to access security services remotely, eliminating the need for expensive on-premises infrastructure. The cloud-based model also provides scalability, ensuring that businesses can easily expand or decrease their security measures as needed.
SaaS providers offer a wide range of services, including vulnerability assessments, threat intelligence, and data encryption. These services help businesses identify and address potential vulnerabilities in their systems, as well as stay informed about the latest cybersecurity threats.
In addition to proactive security measures, SaaS providers also offer incident response management. This includes the ability to quickly detect and respond to security incidents, minimizing the potential impact on a business’s operations.
Overall, Security-as-a-Service providers offer comprehensive and managed cybersecurity solutions that businesses can rely on to protect their valuable assets. From real-time monitoring to incident response management, these providers play a crucial role in safeguarding businesses from the ever-increasing cybersecurity threats.
Contents
- 1 What is Security-as-a-Service?
- 2 Benefits of Security-as-a-Service providers
- 3 Choosing the right Security-as-a-Service provider
- 4 Implementing Security-as-a-Service in your organization
- 5 FAQ about topic “All you need to know about Security-as-a-Service providers”
- 6 What is Security-as-a-Service?
- 7 What are the benefits of using Security-as-a-Service providers?
- 8 How does Security-as-a-Service differ from traditional security solutions?
- 9 What are some important factors to consider when choosing a Security-as-a-Service provider?
- 10 What are some potential challenges of implementing Security-as-a-Service?
What is Security-as-a-Service?
Security-as-a-Service (SaaS) is a cybersecurity service provided by third-party providers that offer a range of security solutions to protect organizations’ data and systems from cyber threats. These providers use cloud technology to deliver their services, allowing organizations to access and benefit from their expertise and resources without the need for on-site deployment.
Managed security services offered by SaaS providers typically include the monitoring and management of various security aspects, such as network security, access controls, vulnerability assessments, and incident response. This comprehensive approach ensures that organizations have a robust and proactive strategy in place to protect their sensitive data.
One of the key advantages of Security-as-a-Service is that it provides organizations with access to highly specialized security expertise that may be challenging to develop in-house. SaaS providers have dedicated teams of cybersecurity professionals who continuously monitor and analyze potential threats and take appropriate measures to prevent security breaches.
By outsourcing their security needs to SaaS providers, organizations can focus on their core business activities while benefiting from advanced security solutions and constant monitoring. This arrangement allows for a more cost-effective use of resources and ensures that organizations can effectively respond to ever-evolving cyber threats.
Overall, Security-as-a-Service providers play a crucial role in safeguarding organizations’ data and infrastructure by offering managed security solutions that include continuous monitoring, incident response, and threat management. With the rise of cyber threats, partnering with a reliable SaaS provider has become an essential component of an effective cybersecurity strategy.
Benefits of Security-as-a-Service providers
In today’s increasingly digitized world, cybersecurity has become a top priority for businesses of all sizes. As cyber threats continue to evolve and become more complex, organizations are turning to Security-as-a-Service providers to ensure the protection of their data, networks, and identities.
One of the key benefits of Security-as-a-Service providers is their expertise in managing cybersecurity. These providers have dedicated teams of security professionals who are trained to identify and respond to various types of threats. They have in-depth knowledge of the latest cybersecurity solutions and can provide managed security services tailored to the specific needs of each client.
Security-as-a-Service providers offer a range of services, including network security, access management, incident response, and data protection. They utilize advanced monitoring tools and technologies to detect and mitigate cyber threats in real-time, providing businesses with round-the-clock protection.
By outsourcing their security needs to a Security-as-a-Service provider, businesses can offload the burden of managing complex security systems and technologies. This allows them to focus on their core competencies while leaving the cybersecurity to the experts.
Another advantage of Security-as-a-Service providers is their ability to leverage the benefits of cloud computing. By delivering security services through the cloud, these providers can offer scalable and flexible solutions that can easily adapt to changing business needs. This eliminates the need for businesses to invest in expensive hardware and software, while still ensuring a high level of security.
In conclusion, Security-as-a-Service providers offer businesses comprehensive cybersecurity solutions, expert management, and the flexibility of cloud-based services. By partnering with these providers, organizations can enhance their security posture, proactively detect and respond to threats, and focus on their core objectives.
Enhanced Security
Security-as-a-Service providers offer enhanced security solutions to protect organizations from cyber threats. With the increasing number of data breaches and cyber attacks, it is essential for businesses to have robust security measures in place to safeguard their data and network.
One area where Security-as-a-Service providers excel is in identity and access management. They offer solutions that ensure only authorized individuals have access to sensitive information, preventing unauthorized access and potential data breaches.
Another key aspect of enhanced security provided by Security-as-a-Service providers is threat monitoring and response. They have advanced tools and technologies to constantly monitor network activity and detect any suspicious or malicious behavior. In the event of a security incident, they have a rapid response system in place to mitigate the threat and minimize any potential damage.
Managed security services are an integral part of enhanced security offered by Security-as-a-Service providers. These services include the management and maintenance of security infrastructure, such as firewalls, intrusion detection systems, and antivirus software. By outsourcing these tasks to a reputable provider, organizations can ensure that their security measures are up to date and effectively protect against evolving threats.
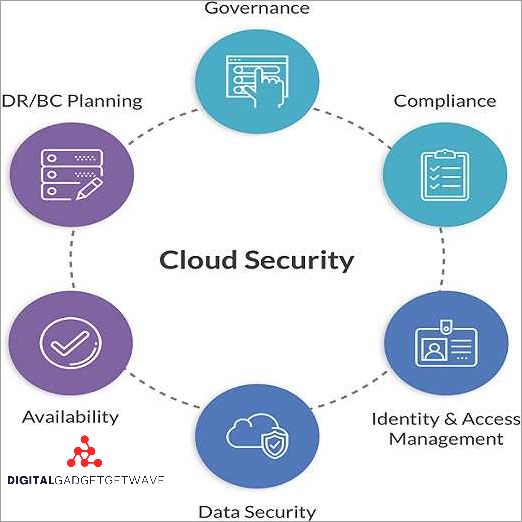
Cloud security is another crucial aspect of enhanced security. As more businesses adopt cloud computing, it is essential to have robust security measures in place to protect sensitive data stored in the cloud. Security-as-a-Service providers offer specialized solutions for cloud security, ensuring that data is encrypted, access is controlled, and there are measures in place to detect and respond to any potential threats.
In conclusion, Security-as-a-Service providers offer enhanced security solutions that encompass various aspects of cybersecurity. From identity and access management to threat monitoring and response, these providers play a critical role in ensuring the protection of data, networks, and systems against cyber threats. Their expertise, advanced tools, and managed services provide businesses with the peace of mind that their security measures are up to date and effective.
Cost-effectiveness

One of the main advantages of using Security-as-a-Service (SECaaS) providers is the cost-effectiveness they offer. By outsourcing security management and monitoring responsibilities to a third-party provider, companies can save significant costs compared to building and maintaining their own in-house security infrastructure.
SECaaS providers offer a range of network security solutions, such as threat protection, incident response, and identity and access management. These providers have specialized expertise in cybersecurity and can offer a level of protection that may be difficult and expensive for companies to achieve on their own.
Cloud-based SECaaS solutions also offer cost savings in terms of hardware and software expenses. Instead of purchasing and maintaining expensive security equipment, companies can rely on the provider’s infrastructure. Additionally, companies can save on licensing fees for security software, as SECaaS providers often include these costs in their service packages.
Furthermore, SECaaS providers often offer flexible pricing plans, allowing companies to scale their security services according to their needs. This means that businesses can adjust their security spending as they grow or in response to changing threat landscapes.
Overall, by leveraging the expertise and resources of a managed security service provider, companies can achieve a higher level of security at a lower cost compared to in-house solutions. This cost-effectiveness makes SECaaS an attractive option for businesses looking to enhance their cybersecurity while optimizing their budget allocation.
Scalability
Scalability is a critical factor to consider when choosing a Security-as-a-Service provider. As cyber threats continue to evolve and increase in complexity, organizations need a provider that can scale their security solutions to meet these changing demands. Scalability refers to the ability of a security service provider to adjust their resources and capabilities to accommodate growing needs, whether it’s a larger network, more incident response capabilities, or increased threat monitoring and management.
With the rapid growth of cloud-based solutions and the increasing adoption of managed security services, scalability has become a key requirement for organizations looking to outsource their cybersecurity needs. A scalable security service provider can easily adapt to the changing security landscape, ensuring that they have the necessary resources and expertise to protect their clients’ networks and data.
One area where scalability is especially crucial is in incident response. An effective security service provider should have the ability to quickly respond to and mitigate security incidents, regardless of their scale or complexity. This means having a robust incident response team that can handle multiple incidents simultaneously, as well as the necessary tools and technologies to identify and contain threats.
In addition to incident response, scalability is also important in identity and access management (IAM). As organizations grow and their workforce expands, they need a security provider that can scale their IAM solutions to accommodate the increased number of users and their access rights. This includes managing privileges, enforcing strong authentication measures, and providing comprehensive identity protection.
Overall, scalability is a critical attribute of a security service provider. It ensures that organizations can effectively protect their networks, data, and users, even as their needs evolve and grow. By choosing a provider with scalable solutions, organizations can future-proof their cybersecurity strategy and have the confidence that their security needs will be met in the long term.
Choosing the right Security-as-a-Service provider
When it comes to cybersecurity, choosing the right Security-as-a-Service (SECaaS) provider is crucial for businesses of all sizes. With the increasing number of cyber threats and the complexity of managing security, organizations are turning to SECaaS providers for their expertise and solutions.
One of the first factors to consider when selecting a SECaaS provider is their expertise in identity and access management. A provider should have strong capabilities in managing user identities and controlling access to systems and data. This is essential for protecting against unauthorized access and ensuring the security of sensitive information.
Another important aspect to consider is the provider’s monitoring capabilities. They should offer real-time monitoring of network and data activities to detect any abnormal behavior or potential security breaches. This allows for quick incident response and minimizing the impact of cyber threats.
A SECaaS provider should also have robust incident response and management capabilities. This includes having a well-defined process for identifying and responding to security incidents, as well as providing ongoing support and guidance for mitigating future risks. Their incident response team should be skilled in handling various types of threats and have a proven track record of successfully managing security incidents.
In addition to incident response, a good SECaaS provider should offer a range of proactive cybersecurity solutions. This may include vulnerability assessments, penetration testing, and threat hunting, among others. By actively identifying and addressing potential vulnerabilities, businesses can better protect their networks and data from cyber attacks.
Lastly, businesses should consider the provider’s cloud security solutions. With the increasing adoption of cloud services, it is important to ensure that the SECaaS provider has the necessary expertise in securing cloud environments. They should offer cloud-specific security controls and monitoring, as well as provide guidance on best practices for securing cloud-based data.
In summary, when choosing a SECaaS provider, organizations should consider their expertise in identity and access management, monitoring capabilities, incident response and management, proactive cybersecurity solutions, and cloud security. By selecting the right provider, businesses can effectively protect their networks, data, and systems from cyber threats.
Reputation and Experience
When choosing a Security-as-a-Service (SECaaS) provider, reputation and experience are crucial factors to consider. A reputable provider will have a proven track record in offering effective cybersecurity solutions and protecting organizations from various cyber threats.
Experience is also important as it demonstrates the provider’s ability to handle different security scenarios and adapt to evolving cyber threats. An experienced SECaaS provider will have a deep understanding of the complex nature of cyber risks and will be equipped to provide tailored solutions to address specific needs.
Managing cybersecurity requires expertise in various areas, such as incident response, threat monitoring, network protection, and data and identity management. A reputable SECaaS provider will excel in these areas, employing advanced monitoring and detection tools to identify and respond to potential threats in real time.
Furthermore, a provider with a strong reputation and extensive experience will have a proven track record in delivering high-quality managed security services. This includes proactive monitoring, rapid incident response, and ongoing security enhancements to ensure continuous protection. Their expertise in managing cloud security will provide organizations with peace of mind, knowing that their sensitive data is safeguarded.
In summary, reputation and experience are key considerations when selecting a Security-as-a-Service provider. By partnering with a reputable and experienced provider, organizations can benefit from advanced cybersecurity solutions, proactive threat monitoring, and expert incident response management.
Service Offerings
Security-as-a-Service providers offer a wide range of protection services to clients, allowing them to outsource their cybersecurity needs to experts in the field. These services can include managed incident response, data protection, access management, network security, and threat monitoring.
Managed incident response services involve providing immediate assistance and guidance in the event of a cyber incident. This can include investigating the incident, containing the threat, and recovering any compromised data. Response times are crucial in minimizing the impact of a cyber attack, and these service providers are equipped to handle such incidents efficiently.
Data protection is a critical aspect of cybersecurity, and Security-as-a-Service providers offer solutions to safeguard sensitive information. This can involve encryption, data backup and restoration, and secure storage options. By employing these measures, clients can ensure that their data remains protected from potential breaches.
Access management services help organizations control who has access to their systems and data. This includes managing user identities, enforcing strong authentication measures, and implementing authorization controls. These measures ensure that only authorized personnel can access sensitive information, reducing the risk of unauthorized access.
Network security services focus on securing the organization’s network infrastructure from cyber threats. This can involve implementing firewalls, intrusion detection systems, and vulnerability scanning tools. By continuously monitoring the network for potential vulnerabilities and threats, these service providers can help prevent and mitigate cyber attacks.
Threat monitoring is another important service offered by Security-as-a-Service providers. This involves monitoring the client’s systems and networks for any suspicious or malicious activities. By utilizing advanced threat intelligence tools and techniques, these service providers can detect and respond to potential threats in real-time, minimizing the damage caused by cyber attacks.
Customer Support
Cybersecurity is a critical aspect of any organization’s operations in the modern digital landscape. As businesses increasingly rely on cloud services and network infrastructure to store and access data, it becomes crucial for them to have robust security measures in place to mitigate potential threats and protect sensitive information.
Security-as-a-Service (SECaaS) providers offer a range of solutions to help businesses enhance their cybersecurity posture. Apart from providing managed security services, these providers also offer customer support to ensure effective incident response and threat management.
Customer support in the context of SECaaS involves multiple aspects. One crucial aspect is timely and efficient response to customer inquiries and issues. This includes addressing concerns related to identity and access management, data protection, and incident response.
SECaaS providers typically offer various channels for customer support, including phone, email, and live chat. These channels enable customers to seek guidance and assistance from experts who specialize in cybersecurity and network protection.
Furthermore, customer support may also include proactive measures such as regular communication and updates regarding emerging threats and security best practices. This can help businesses stay informed and ensure that their security measures align with industry standards.
Additionally, some SECaaS providers may offer training and educational resources to help customers better understand and navigate the complexities of cybersecurity. This can include webinars, workshops, and documentation that provide insights into effective security practices and threat management techniques.
In summary, customer support is a crucial component of Security-as-a-Service offerings. By providing timely and comprehensive assistance, SECaaS providers ensure that businesses can effectively leverage their cybersecurity solutions to protect their data and mitigate cyber threats.
Implementing Security-as-a-Service in your organization

In the digital age, organizations face increasing threats to their data and network security. Cyber attacks and incidents have become more sophisticated and frequent, making it crucial for businesses to have robust security measures in place. Security-as-a-Service (SECaaS) providers offer cloud-based solutions that can help organizations enhance their cybersecurity.
One of the key benefits of implementing Security-as-a-Service is the constant monitoring and threat detection provided by the service provider. They leverage advanced tools and technologies to track and analyze cyber threats, ensuring that any potential incidents are identified and addressed promptly. This proactive approach can help prevent data breaches and minimize the impact of security incidents on the organization.
SECaaS providers also offer identity and access management solutions, which are essential for protecting sensitive data from unauthorized access. These solutions enable organizations to set up strong authentication measures, manage user permissions, and track user activity. By implementing these measures through a Security-as-a-Service provider, organizations can enhance their data protection and reduce the risk of insider threats.
Another advantage of Security-as-a-Service is the ability to leverage the expertise and experience of the service provider. These providers have dedicated teams of cybersecurity professionals who are well-versed in the latest security best practices and industry standards. They can provide guidance and support to organizations in developing and implementing effective security strategies. This can be especially beneficial for small and medium-sized businesses that may not have the resources to maintain an in-house cybersecurity team.
When selecting a Security-as-a-Service provider, it is important to choose a reputable and reliable partner. Look for providers that have a proven track record in the industry and have experience working with organizations similar to yours. Additionally, consider the scalability and flexibility of the provider’s services, as your organization’s security needs may evolve over time.
In conclusion, implementing Security-as-a-Service in your organization can provide numerous benefits, including continuous monitoring, enhanced identity and access management, and access to cybersecurity expertise. By partnering with a trusted SECaaS provider, organizations can strengthen their security posture and better protect their valuable data and network infrastructure.
Assessing your security needs
When it comes to cybersecurity, every organization has unique needs and requirements. In order to effectively protect your network, data, and resources, it’s important to assess your specific security needs. This assessment will help you determine the level of protection required and the type of security-as-a-service provider that best fits your organization.
First and foremost, it’s essential to identify the potential threats that your organization may face. This can include both internal and external threats, such as unauthorized access to data or network, identity theft, or data breaches. By understanding the potential risks, you can better prioritize your security needs.
Next, you should evaluate your current security solutions and management processes. Are you currently using managed security services or do you have an in-house team? Assessing the effectiveness of your existing security measures can help you identify any gaps or areas that need improvement. This can include incident response capabilities, threat detection and mitigation, and access controls.
Additionally, consider the nature of your business and the types of data you handle. If you deal with sensitive customer information or financial data, you may require higher levels of protection. Assessing the data sensitivity and regulatory requirements can help you determine the necessary level of cybersecurity.
Lastly, consider the scalability and flexibility of the security-as-a-service provider. As your organization grows or adopts new technologies, your security needs may change. It’s important to choose a provider that can adapt and evolve with your business, providing ongoing support and updates to ensure your security remains robust.
- Identify potential threats
- Evaluate current security solutions and processes
- Assess the nature of your business and data sensitivity
- Consider scalability and flexibility
Selecting the right provider
When it comes to selecting a Security-as-a-Service (SecaaS) provider, there are several factors to consider. The provider you choose will be responsible for monitoring and managing your cybersecurity solutions, so it’s important to choose a provider that can meet your specific needs.
One of the first things to consider is the range of services offered by the provider. Do they offer a comprehensive suite of managed security solutions, including network protection, identity and access management, and incident response? It’s important to choose a provider that can offer a comprehensive range of services to ensure that all aspects of your cybersecurity are covered.
The provider’s level of expertise and experience is also important to consider. Look for a provider that has a proven track record in providing cybersecurity services. This can be demonstrated through certifications, industry awards, and client testimonials. A provider with a strong reputation in the industry is more likely to have the knowledge and experience to effectively protect your data and respond to threats.
Another key consideration is the provider’s approach to incident response. In the event of a security incident, it’s important to have a provider that can respond quickly and effectively. Look for a provider that has a well-defined incident response management process in place, with clear protocols and procedures for detecting, analyzing, and resolving security incidents. This will ensure that any potential threats or breaches are addressed promptly.
Finally, it’s important to consider the level of customer support provided by the provider. Cybersecurity is an ongoing process, and you’ll want a provider that is readily available to address any questions or concerns that may arise. Look for a provider that offers 24/7 customer support and has a dedicated team of experts available to assist you.
By considering these factors and conducting thorough research, you can choose the right Security-as-a-Service provider that will effectively protect your data and provide the support you need to maintain a strong cybersecurity posture.
Integration and deployment process

When integrating a Security-as-a-Service (SECaaS) provider into your organization’s infrastructure, it is essential to understand the integration and deployment process. This process involves various steps that ensure seamless integration and effective deployment of the security solutions provided by the SECaaS provider.
Firstly, the integration process begins with a thorough assessment of your organization’s data, access, and network infrastructure. This assessment helps identify potential vulnerabilities and determine the appropriate security solutions needed to protect your organization against cyber threats.
Once the assessment is complete, the SECaaS provider will work closely with your organization’s IT team to deploy the necessary security solutions. This deployment process involves configuring firewalls, setting up intrusion detection systems, implementing endpoint protection, and establishing secure access controls, among other measures.
During the integration and deployment process, it is crucial to ensure continuous monitoring of the network and systems. This monitoring enables real-time threat detection and response, allowing proactive incident management and mitigation of potential cybersecurity incidents.
Furthermore, the SECaaS provider should provide ongoing management and support for the deployed security solutions. This includes regular updates and patch management to address emerging threats and vulnerabilities. The provider should also offer timely incident response services to minimize the impact of any cybersecurity incidents.
Overall, the integration and deployment process with a Security-as-a-Service provider require close collaboration between the provider and your organization’s IT team. It is crucial to establish clear communication channels and define roles and responsibilities to ensure the successful implementation of effective security solutions.
FAQ about topic “All you need to know about Security-as-a-Service providers”
What is Security-as-a-Service?
Security-as-a-Service (SECaaS) is a cloud-based security solution that provides businesses with comprehensive protection against cyber threats. It offers a range of security services such as network security, endpoint security, and data protection, delivered as a subscription service.
What are the benefits of using Security-as-a-Service providers?
There are several benefits of using Security-as-a-Service providers. Firstly, it eliminates the need for businesses to invest in expensive hardware and software infrastructure. Secondly, it provides access to advanced security technologies and expertise that might not be available in-house. Thirdly, it offers scalability, allowing businesses to easily adjust their security needs as they grow. Lastly, it provides continuous monitoring and threat intelligence, ensuring proactive protection against emerging threats.
How does Security-as-a-Service differ from traditional security solutions?
Unlike traditional security solutions that require businesses to manage their own security infrastructure, Security-as-a-Service is provided and managed by a third-party provider. This means businesses don’t have to worry about hardware and software updates, system maintenance, or hiring specialized security personnel. Security-as-a-Service also offers greater scalability and flexibility, allowing businesses to easily adjust their security needs and add new services as required.
What are some important factors to consider when choosing a Security-as-a-Service provider?
When choosing a Security-as-a-Service provider, it is important to consider their reputation and track record in the industry. Look for providers with a proven ability to deliver reliable and effective security services. It is also crucial to assess their level of expertise and the range of security services they offer. Additionally, consider factors such as the availability of support services, pricing models, and the level of customization they can provide to meet your specific security requirements.
What are some potential challenges of implementing Security-as-a-Service?
While Security-as-a-Service offers many benefits, there can be challenges associated with implementation. One challenge is the potential reliance on internet connectivity for accessing security services, which can be a concern in areas with unreliable or slow internet connections. Another challenge is ensuring proper integration with existing IT infrastructure and systems. Additionally, businesses may need to address concerns around data privacy and compliance requirements when outsourcing security services to a third-party provider. It is important to carefully evaluate these challenges and find suitable solutions before implementing Security-as-a-Service.


