Public vs Private Network: Understanding the Key Differences
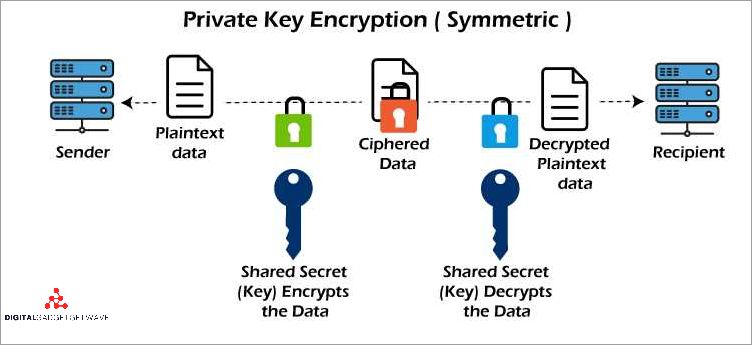
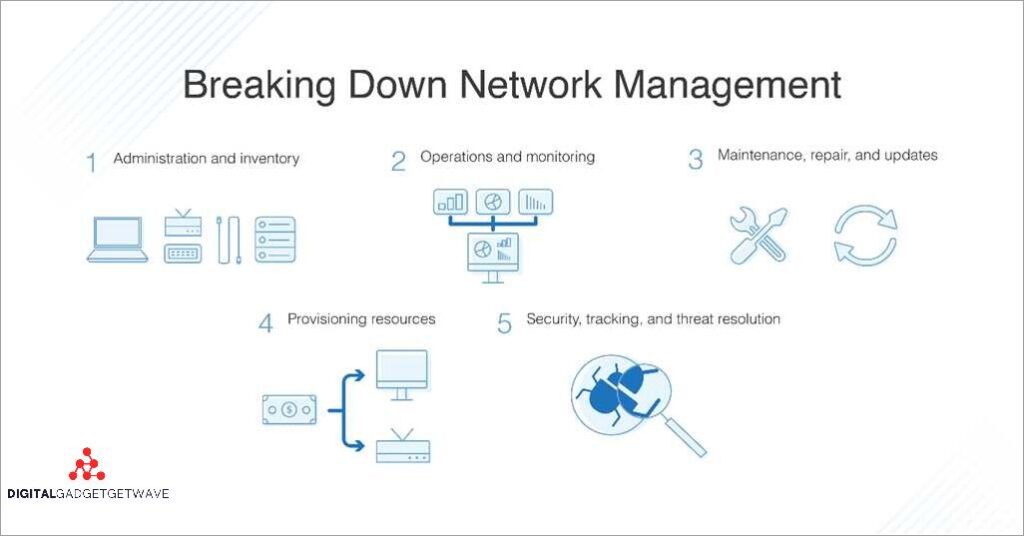
In today’s digital age, network security is of paramount importance. As individuals and businesses become increasingly reliant on the internet for communication and data storage, it is crucial to understand the key differences between public and private networks to ensure the safety and protection of sensitive information. A public network refers to a network that ...