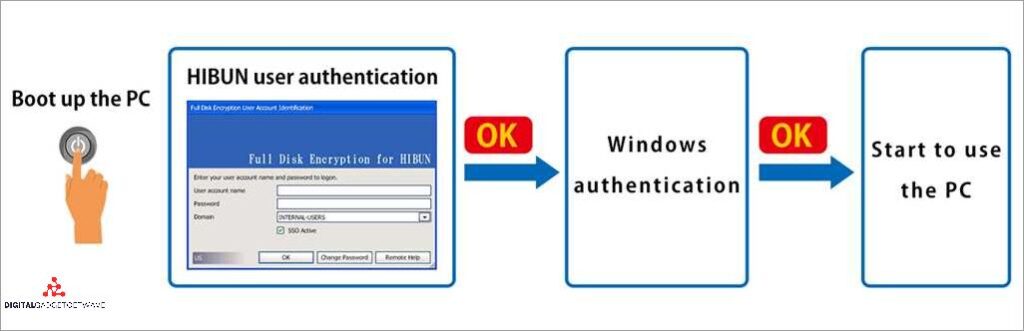
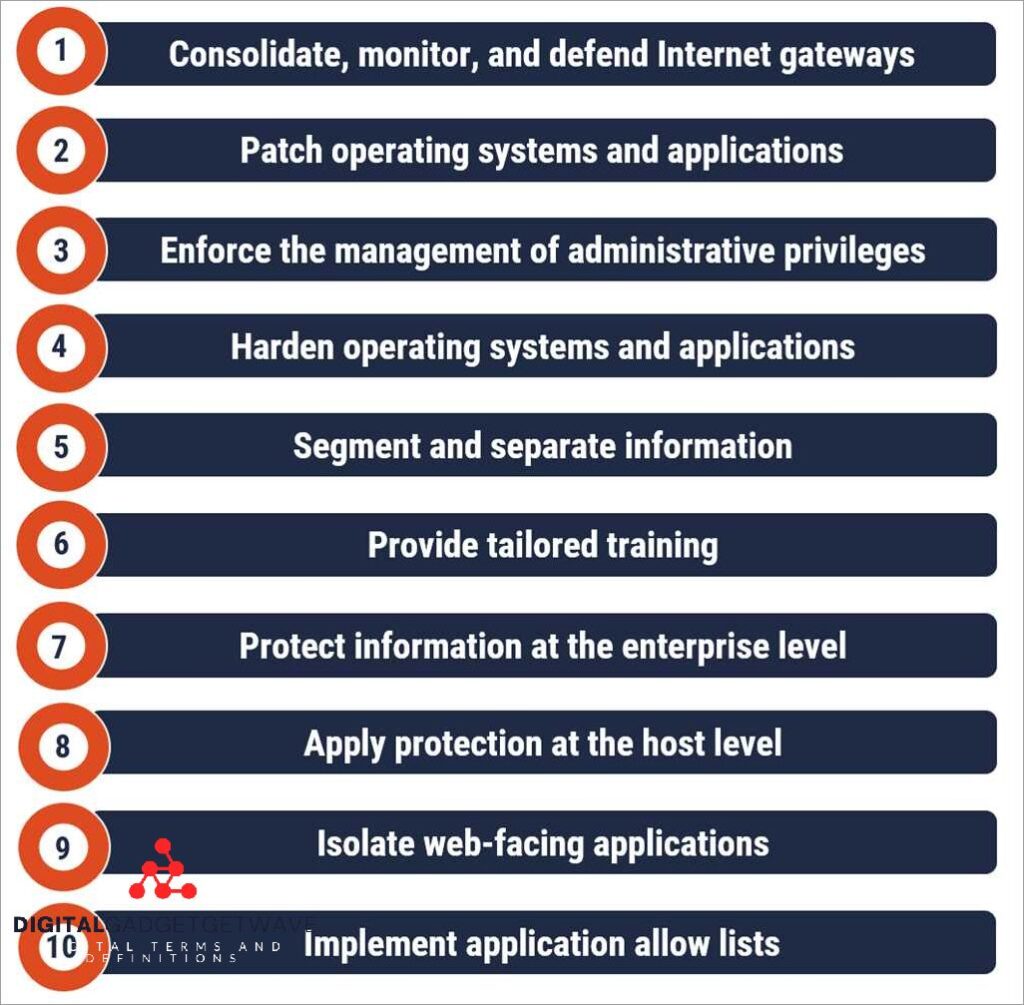
Secure Web Service: How to Protect Your Online Activities
In today’s digital age, it is more important than ever to ensure the security of our online activities. With the increasing prevalence of cyberattacks and data breaches, safeguarding our information has become a top priority. This article will explore some essential strategies and technologies that can help in protecting our online presence. One of the ...