
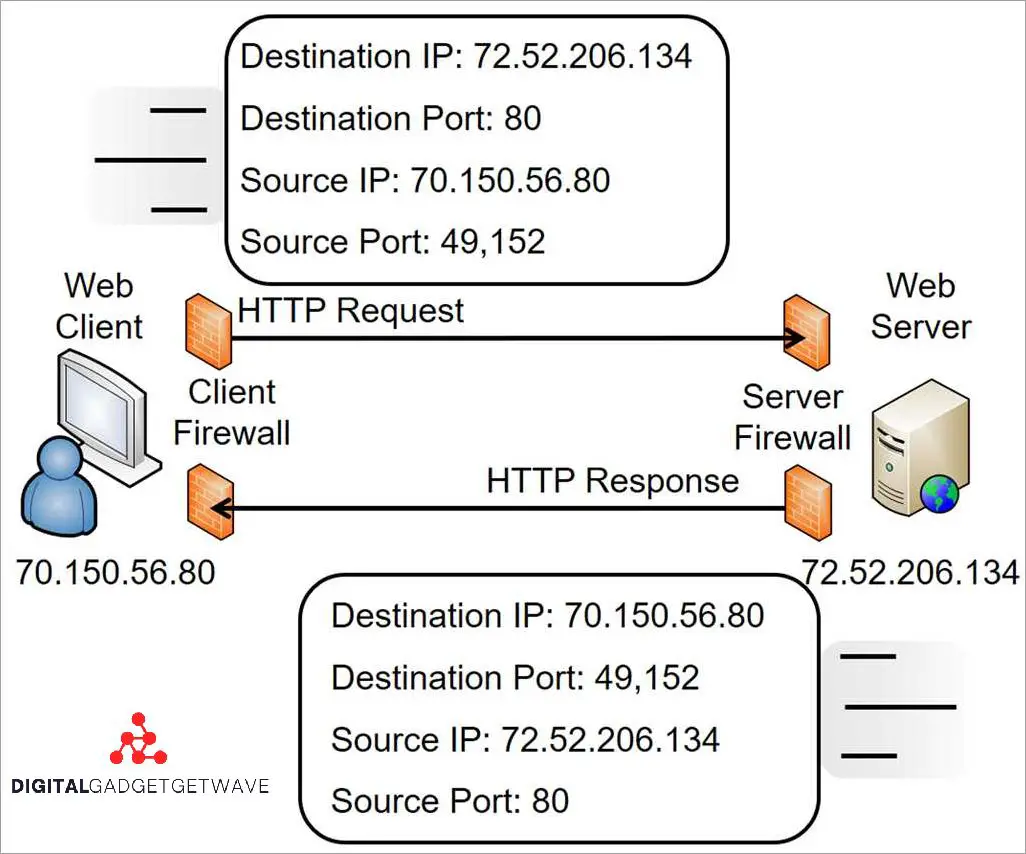
Port 80 blocking is a common security measure used by servers and firewalls to restrict access to certain ports and protocols. Port 80 is the port used for HTTP traffic, which is the protocol used to access websites and communicate over the internet. By blocking port 80, a server or firewall can deny access to websites and restrict the flow of traffic to and from the network.
The main reason for port 80 blocking is to enhance the security of a server or network. By restricting access to port 80, an administrator can prevent unauthorized users from accessing sensitive information or conducting malicious activities. Port 80 blocking is especially important for servers hosting sensitive data or e-commerce websites that handle financial transactions.
Port 80 blocking is typically implemented using a firewall or network filtering mechanism. When a request is made to access a website on port 80, the firewall checks the source IP address and the destination port. If the firewall determines that the source IP is not allowed to access port 80, it will block the request and deny access. This filtering process is crucial for maintaining the security and integrity of a network.
However, port 80 blocking can sometimes cause issues for legitimate users. For example, if a user is trying to access a website using the HTTPS protocol, which typically uses port 443, but port 80 is blocked, they may encounter connectivity issues. In these cases, troubleshooting port 80 blocking involves identifying the firewall or network filter responsible for the block and adjusting the settings to allow the necessary traffic.
In conclusion, port 80 blocking is an important security measure used to restrict access to websites and control the flow of traffic on a server or network. While it helps protect against unauthorized access and malicious activities, it can occasionally cause issues for legitimate users. Understanding the effects of port 80 blocking and knowing how to troubleshoot can help maintain a secure and functional network environment.
Contents
- 1 Potential Effects of Port 80 Blocking
- 2 Reasons for Port 80 Blocking
- 3 Troubleshooting Port 80 Blocking
- 4 Alternatives to Port 80
- 5 FAQ about topic “Port 80 Blocking: Understanding the Effects and How to Troubleshoot”
- 6 What is port 80 blocking and why is it important to understand its effects?
- 7 How does port 80 blocking affect web browsing?
- 8 What are the potential reasons for port 80 blocking?
- 9 How can I troubleshoot port 80 blocking issues?
- 10 Are there any alternatives to port 80 for web services?
Potential Effects of Port 80 Blocking
The blocking of port 80 can have several potential effects on the network and overall internet access. Port 80 is commonly used for HTTP (Hypertext Transfer Protocol) traffic, which is the protocol used for accessing websites and transferring web content.
Blocking port 80 can restrict or block access to websites hosted on servers using the HTTP protocol. This can affect both incoming and outgoing traffic, as users may be unable to access websites hosted on servers using port 80, and servers using port 80 may be unable to receive incoming requests.
Port 80 blocking can also impact the security of the network. HTTP traffic is unencrypted, which means that sensitive information such as usernames, passwords, and personal data can be intercepted and read by malicious actors. Without the ability to block port 80, network administrators may find it more difficult to enforce security measures and protect user data.
In addition to blocking regular HTTP traffic, port 80 blocking can also impact other protocols and services that rely on this port. For example, port 80 is commonly used for HTTPS (HTTP Secure) traffic, which encrypts data to provide a higher level of security. Without access to port 80, users may be unable to access websites that use HTTPS, further restricting internet access and hindering browsing capabilities.
Firewalls and network filtering can be used to deny or allow access to port 80, providing better control over the type of traffic allowed on the network. However, network administrators must carefully configure these security measures to ensure that legitimate traffic is not unintentionally blocked or restricted.
In summary, port 80 blocking can have various effects on network traffic, security, and internet access. It can restrict or block access to websites, affect the security of data transmitted over the network, and impact services that rely on this port, such as HTTPS. Proper configuration and management of network security measures are important to balance security with accessibility and usability.
Impact on Web Browsing
When port 80 is blocked, it has a significant impact on web browsing. Port 80 is the default port for HTTP (Hypertext Transfer Protocol), which is the protocol used for transferring data between a web server and a client on the internet.
By blocking port 80, internet service providers (ISPs), network administrators, or firewalls can restrict or deny access to websites that are hosted on servers using this port. This filtering can be used for security reasons, to prevent access to malicious or inappropriate content, or to control or limit the amount of traffic on a network.
When port 80 is blocked, it prevents users from accessing websites that use the HTTP protocol. However, this does not mean that all web browsing is completely blocked. Many websites now use HTTPS (Hypertext Transfer Protocol Secure), which uses port 443, for secure browsing. Blocking port 80 does not block access to websites that use HTTPS.
In addition to blocking access to certain websites, blocking port 80 can also impact other aspects of web browsing. For example, it may prevent the establishment of TCP/IP connections on port 80, which can affect the functionality of certain web applications or services.
To troubleshoot the impact of a blocked port 80, network administrators can check the firewall or network settings to see if port 80 is explicitly blocked. They can also check the logs or use network monitoring tools to identify any restrictions or blocking of HTTP traffic. Additionally, they may need to review the configuration of any filtering or security devices that are in place to see if they are blocking port 80.
In conclusion, the blocking of port 80 can have a significant impact on web browsing, as it restricts access to websites that use the HTTP protocol. It is important for network administrators to understand the effects of this blocking and to troubleshoot any issues that may arise.
Limitations for Web Servers

Web servers are an integral part of the internet infrastructure, hosting websites and serving web content to users. However, they have certain limitations that need to be considered when setting up and configuring a web server.
Protocol and Port Limitations: Web servers primarily use the HTTP protocol to transmit data over the internet. The default port for HTTP is 80. However, some restrictions may apply depending on the network configuration. For example, a firewall may block port 80 to restrict access to the web server.
Deny List and Filtering: Web servers can be configured to have deny lists or filtering rules to block specific IP addresses or ranges. This can be an effective way to enhance security and prevent unauthorized access. However, it can also lead to limitations for legitimate users who may be mistakenly blocked or restricted.
HTTPS and Security: While HTTP is the default protocol for web servers, it is not secure for transmitting sensitive information. To address this limitation, web servers should also support HTTPS, which encrypts the data transmitted between the server and the client. This helps protect against eavesdropping and tampering of the data, enhancing the security of the web server.
Network Restrictions: Web servers may face network restrictions that could limit their functionality. For example, an organization may implement proxy servers or content filtering systems that restrict certain types of traffic, including HTTP. This can affect the accessibility and performance of the web server.
Overall, web servers have several limitations due to protocol and port restrictions, deny lists and filtering rules, the need for HTTPS security, and network restrictions. It’s important to understand these limitations and properly configure the web server to ensure optimal performance, accessibility, and security.
Issues with Web Services
The availability and proper functioning of web services can be affected by various issues related to server configuration, network restrictions, and access control policies. These issues can arise due to several factors, such as the use of restrictive firewalls or blocking of specific ports.
One of the common issues encountered with web services is the blocking of port 80. Port 80 is the default port for HTTP (Hypertext Transfer Protocol) traffic, which is used for communication over the internet. When this port is blocked, it restricts the ability of users to access websites and web services hosted on the server.
In some cases, port 80 blocking may be intentional as a security measure. Organizations may choose to block port 80 to mitigate potential vulnerabilities associated with the HTTP protocol. However, this can also affect the availability and accessibility of web services, especially if users are unable to access the services through alternative secure protocols like HTTPS.
Another issue related to web services is the filtering of HTTP traffic. Filtering can be implemented at different levels, such as at the network level or on the server itself. This filtering can be based on various criteria, including IP addresses, specific URLs, or content filtering based on keywords or patterns.
When filtering is applied to HTTP traffic, it can lead to the denial of access for certain users or the modification of content being sent or received. This can have a significant impact on the functionality and usability of web services, as it may prevent users from accessing certain resources or alter the behavior of the service.
To troubleshoot issues with web services, it is essential to identify the specific factors causing the problems. This may involve analyzing firewall configurations, network logs, and server settings related to port blocking, filtering, and security measures. By understanding the underlying causes, appropriate adjustments can be made to ensure the smooth functioning and accessibility of web services.
Reasons for Port 80 Blocking
There are several reasons why port 80 may be blocked. One of the main reasons is to improve security. Port 80 is commonly used for HTTP traffic, which can pose security risks as it is not encrypted. By blocking port 80, organizations can restrict access to unsecured internet traffic, reducing the potential for attacks and data breaches.
Another reason for blocking port 80 is to prioritize or limit internet access. By blocking this port, organizations can enforce policies that prioritize specific protocols or services, such as HTTPS. This allows for a more controlled and efficient use of network resources.
Blocking port 80 can also be done to deny access to specific IP addresses or servers. Organizations may want to block certain IP addresses or servers that pose a threat or are known sources of malicious traffic. By denying access to port 80, these organizations can effectively block traffic from these sources.
Firewalls and filtering systems often block port 80 as part of their default settings. These systems monitor network traffic and block certain ports, including port 80, to protect against potential threats. In addition to port 80, other TCP ports may also be blocked to strengthen network security.
Furthermore, the increasing use of HTTPS as the default protocol for secure communication has led to the blocking of port 80 in favor of port 443. Port 443 is used for HTTPS traffic, which is encrypted and provides a higher level of security compared to plain HTTP. Many organizations now choose to block port 80 and only allow port 443 to ensure that all web traffic is encrypted and secure.
Firewall Restrictions
A firewall is a network security device that monitors and filters incoming and outgoing traffic based on predetermined security rules. It acts as a barrier between an internal network and the larger internet, allowing or denying access to specific ports, IP addresses, and protocols. One common restriction that a firewall can impose is the blocking of certain ports, including port 80.
Port blocking is a technique used by firewalls to deny access to specific ports. When a firewall blocks port 80, it prevents any incoming or outgoing traffic on that port. Port 80 is commonly used for HTTP (Hypertext Transfer Protocol) connections, which are used for accessing websites. By blocking port 80, the firewall restricts access to web servers running on the network.
In addition to port blocking, firewalls can also restrict access based on IP addresses. For example, an administrator can configure a firewall to deny access to a specific IP address or range of IP addresses. This can be useful in preventing unauthorized access or blocking known malicious IP addresses.
Firewalls can also implement filtering rules to control the type of traffic allowed through. For example, a firewall can be configured to only allow HTTP traffic (port 80) and deny other protocols such as TCP or UDP. This level of filtering helps to ensure that only desired network traffic is allowed through, enhancing security.
Another common restriction imposed by firewalls is the blocking of specific websites or internet domains. By maintaining a list of blocked domains, a firewall can prevent access to certain websites or restrict internet browsing to a predefined set of allowed websites. This can be achieved through a combination of port blocking, IP address blocking, and domain name filtering.
Overall, firewall restrictions play a crucial role in network security by controlling access to ports, IP addresses, and protocols. By implementing proper firewall rules to block or allow specific traffic, organizations can ensure the security and integrity of their network and server infrastructure.
ISP Policies
In order to maintain network security and prevent unauthorized access, Internet Service Providers (ISPs) may implement blocking measures through their ISP policies. ISPs have the ability to block or restrict certain IP addresses, ports, and protocols to protect their users and network from potential security threats.
One common practice that ISPs employ is port blocking. This involves denying access to specific ports on a user’s internet connection. For example, port 80 is commonly used for HTTP traffic, while port 443 is used for HTTPS traffic. By blocking certain ports, ISPs can prevent unwanted or potentially harmful traffic from entering their network.
ISPs may also implement filtering mechanisms to block certain types of traffic based on protocols. For instance, they may block the TCP protocol on certain ports to restrict access to specific services. This can be done using firewall rules that deny or drop incoming or outgoing traffic on those ports.
To enforce their blocking policies, ISPs may use various techniques such as deep packet inspection (DPI) to inspect the content of network packets and determine if they should be allowed or blocked. This allows them to identify and block specific types of traffic that may pose a security risk or violate their policies.
It is important to note that while ISP blocking measures aim to improve network security, they can also have unintended consequences. For example, if an ISP blocks a certain port or protocol that is necessary for a user’s legitimate internet activities, it can lead to disruptions in their online experience.
In summary, ISP policies regarding blocking and restricting internet traffic play an important role in maintaining network security. By implementing measures such as port blocking, protocol filtering, and deep packet inspection, ISPs can protect their users and network from potential threats. However, it is necessary to strike a balance between security and ensuring that legitimate user activities are not unnecessarily restricted.
Security Concerns
Security is a top priority for any online operation, and concerns regarding port 80 blocking are no exception. The use of the https protocol has become increasingly important in recent years due to the rise in internet threats and the need to protect sensitive data. With port 80 being the default port for HTTP traffic, it is essential to ensure that any blocked or restricted access to this port does not compromise the security of your server or network.
When a port, such as port 80, is blocked or filtered, it prevents incoming and outgoing TCP/IP traffic on that port. This blocking can be done at the network level, using a firewall or other security devices, or at the server level, restricting access to the port. By blocking port 80, organizations can control access to HTTP traffic and reduce the risk of unauthorized access to their servers.
By denying access to port 80, organizations can effectively control the flow of internet traffic and safeguard against common security threats. Blocking port 80 can help prevent unauthorized access to web servers and protect against malicious attacks, such as Denial of Service (DoS) or Distributed Denial of Service (DDoS). It also denies external users the ability to establish a connection with the server, reducing the risk of data breaches or other security incidents.
However, it is important to note that blocking port 80 should be done with caution. While it can enhance security, it may also restrict legitimate access to websites and services that rely on the HTTP protocol. Organizations need to carefully assess the impact and consider alternative measures, such as using strong firewall policies, filtering traffic based on specific criteria, or using alternative port numbers for HTTP traffic.
Troubleshooting Port 80 Blocking
If you are experiencing issues with accessing websites or services that use the HTTP protocol, it’s possible that port 80 is being blocked. Port blocking is a security measure implemented by firewalls and network devices to deny or restrict traffic on specific ports.
Port 80 is commonly used for HTTP (Hypertext Transfer Protocol) traffic, which is the protocol that allows web servers to communicate with client devices. By blocking port 80, the firewall or network device prevents any HTTP traffic from passing through, effectively restricting access to web servers and websites.
To troubleshoot port 80 blocking, you can start by checking the firewall configuration. Ensure that the firewall rules are not set to block incoming or outgoing traffic on port 80. Additionally, check if any IP filtering rules are in place that might be blocking access to the HTTP port.
If the firewall configuration appears to be correct, it’s possible that another device on the network is blocking port 80 traffic. In this case, you can try bypassing or disabling any additional network devices or routers to see if the issue persists.
It’s also important to note that some ISPs (Internet Service Providers) may block port 80 as a part of their security measures. In such cases, you may need to contact your ISP to request the unblocking of port 80 or explore alternative solutions, such as using a different port for HTTP traffic (e.g., port 8080) or switching to HTTPS (Hypertext Transfer Protocol Secure) which uses port 443.
Checking Firewall Settings
Firewalls play a crucial role in maintaining the security of a network by monitoring and controlling incoming and outgoing network traffic. When dealing with port 80 blocking, it is essential to check the firewall settings to identify any restrictions on the HTTP protocol.
Port 80 is the default port for HTTP traffic, which is used for accessing websites over the internet. If a firewall is set to restrict or block access to this port, it can prevent users from accessing websites hosted on a web server.
Firewalls can be configured to allow or deny traffic based on various criteria, such as the IP address, protocol, or port number. In the case of port 80 blocking, the firewall may be configured to deny any incoming TCP/IP traffic on port 80, effectively blocking access to web servers.
It’s also important to consider that port 80 is used for unencrypted HTTP traffic. In cases where websites use encrypted connections (HTTPS), which use port 443, the firewall settings may need to be modified to allow this traffic as well.
When troubleshooting port 80 blocking, it’s recommended to check the firewall rules and policies to ensure that they are not preventing access to the HTTP protocol. Additionally, checking the firewall logs can provide valuable information on any denied traffic attempts and help identify potential issues.
A comprehensive approach to troubleshooting port 80 blocking involves checking both the server-side and client-side firewall settings to ensure that the traffic is allowed through at all points in the network. Properly configuring the firewall settings for port 80 can help ensure the secure and uninterrupted access to web services.
Contacting ISP for Clarifications

If you suspect that your ISP (Internet Service Provider) is blocking or filtering port 80 on your network, it is important to contact them to get clarification on the issue.
First, check if other ports or protocols are being blocked as well. Sometimes ISPs implement firewall rules or restrict certain IP addresses, which can affect access to your server or websites.
When contacting your ISP, it is crucial to provide specific information about the issue you are facing. Include details such as the specific error messages you are encountering when trying to access websites or servers on port 80.
If your ISP confirms that they are indeed blocking port 80, inquire about the reasons behind this restriction. They may have implemented this measure for security purposes or for controlling bandwidth usage on their network.
You can also ask your ISP if there are any alternative ports or protocols you can use to access your server or websites. For example, HTTPS connections on port 443 are typically not blocked, so you may consider using this protocol instead.
Additionally, request your ISP to provide guidance on any necessary changes you need to make to your network settings or firewall configurations to ensure proper access and security.
Keep in mind that some ISPs may have specific policies or guidelines that determine their port blocking practices. Understanding these policies and complying with them can help you troubleshoot the port 80 blocking issue more effectively.
Implementing HTTPS
HTTPS (Hypertext Transfer Protocol Secure) is a secure version of the HTTP protocol, which is often used to access websites over the internet. Implementing HTTPS is an important step towards enhancing the security of a website and protecting the sensitive information of its users.
To implement HTTPS, a secure socket layer (SSL) or transport layer security (TLS) certificate is required. This certificate is used to encrypt the communication between the client’s browser and the server, ensuring that the data transmitted is secure and cannot be intercepted by malicious third parties.
When HTTPS is enforced, any attempt to access the website over an unsecured HTTP connection will be denied. This means that users will only be able to access the website via a secure HTTPS connection.
To access a website using HTTPS, a client’s browser connects to the server on port 443 using the TCP (Transmission Control Protocol) protocol. This secure connection is established by following a series of handshakes between the client and the server.
When HTTPS is implemented, it adds an additional layer of security to the network traffic by encrypting the data being transmitted. This makes it more difficult for attackers to intercept or tamper with the data, ensuring that sensitive information remains protected.
Implementing HTTPS also helps to improve the overall security of a website. It can help prevent unauthorized access to the website’s server, as well as protect against potential attacks such as man-in-the-middle attacks. Furthermore, it can help verify the authenticity of the server by validating its certificate.
In conclusion, implementing HTTPS is essential for enhancing the security of a website and protecting the privacy of its users. By encrypting the network traffic and restricting access to secure connections only, websites can ensure that sensitive information remains safe from potential threats.
Alternatives to Port 80
If you are experiencing issues with port 80 being blocked on your network, there are several alternatives you can consider to maintain network security and restrict access to specific IP addresses.
1. Using a Firewall: A firewall is a network security device that can block or allow specific types of traffic based on predefined rules. By configuring your firewall, you can easily block or allow traffic on different ports, including port 80.
2. Changing the Port: If you want to avoid blocking port 80 altogether, you can consider changing the port that your web server listens on. This can be done by reconfiguring your server settings or using a specific port forwarding rule on your router. However, keep in mind that clients will need to append the port number to the URL when accessing the website (e.g., http://example.com:8080).
3. Using HTTPS: HTTPS (HyperText Transfer Protocol Secure) is a protocol that uses encryption to secure the data being transmitted between a client and a server. By using HTTPS on port 443, you can ensure that your website’s traffic is encrypted and secure, even if port 80 is blocked.
4. Implementing TCP Filtering: TCP (Transmission Control Protocol) filtering is a feature available on many firewalls and routers. It allows you to block or allow specific types of TCP traffic based on various criteria, such as IP address, port number, or protocol. By configuring TCP filtering, you can specifically deny or allow traffic on port 80.
5. Using a Proxy Server: A proxy server acts as an intermediary between clients and servers, allowing you to redirect and filter network traffic. By configuring a proxy server, you can route HTTP traffic from port 80 to another port that is not blocked on your network.
Overall, when port 80 is blocked, it is important to consider these alternatives to ensure that your internet services remain accessible while maintaining network security.
Using Alternate Ports
When the default port 80 is blocked, it can greatly impact the accessibility of websites and online services. However, one way to overcome this issue is by using alternate ports.
By default, the standard HTTP protocol uses port 80 to transmit data over a TCP/IP network. When this port is blocked, it means that the network is configured to deny access or restrict traffic on this specific port. In such cases, accessing websites or online services through the standard HTTP protocol becomes impossible.
However, using alternate ports can help bypass this blocking or filtering. Instead of connecting to a server through port 80, users can specify a different port number to establish a connection. For example, using port 8080 or 8000 for web traffic instead of port 80.
It is important to note that when using alternate ports, both the client and the server need to agree on the port number to be used. The server must be configured to listen on the specified port, and the client must specify the same port number when making the request.
In addition, when using secure connections, such as HTTPS, the default port is 443. If this port is blocked, using an alternate port for HTTPS traffic, such as port 8443, can help ensure secure communication between the client and the server.
However, it’s worth noting that using alternate ports may introduce some challenges. For example, firewalls or network devices may still block or restrict traffic on non-standard ports. Additionally, some internet service providers may also block specific ports, regardless of their numbering. Therefore, it is important to ensure that the alternate port being used is open and accessible to both the client and the server.
Transition to IPv6
With the continuous growth of the internet and the increasing number of devices connected to it, the need for more IP addresses became evident. IPv4, the current version of the Internet Protocol, has limited availability of addresses, which led to the development of IPv6. The transition to IPv6 aims to address this limitation by providing a much larger address space.
One of the key challenges in the transition to IPv6 is ensuring access to IPv6-enabled resources without disrupting the existing IPv4 infrastructure. This is particularly important for services running on port 80, such as HTTP. Network administrators often implement blocking or filtering mechanisms on their firewalls to restrict or deny access to certain IP addresses or ports.
IPv6 introduces new protocols and mechanisms to enable coexistence and smooth transition between IPv4 and IPv6 networks. For example, the TCP/IP protocol stack, which is widely used for internet communication, has been extended to support both IPv4 and IPv6. This allows traffic to be routed and exchanged between IPv4 and IPv6 networks.
However, due to the differences in addressing and routing between IPv4 and IPv6, network administrators may need to update their firewall rules, access control lists, or security policies to accommodate IPv6 traffic. In some cases, they may need to configure additional rules or allow specific port numbers to pass through the firewall.
As the transition to IPv6 progresses, it is important for organizations to stay updated with the latest developments and best practices to ensure a smooth and secure transition. This may involve conducting network assessments, implementing IPv6-enabled network devices, and educating network administrators on IPv6-specific configurations and troubleshooting techniques.
In summary, the transition to IPv6 is necessary to accommodate the growing number of devices and ensure continued access to internet resources. Network administrators need to understand the implications of IPv6 on their existing infrastructure and take appropriate measures to eliminate any blocking or filtering issues that may restrict or deny access to IPv6-enabled services.
FAQ about topic “Port 80 Blocking: Understanding the Effects and How to Troubleshoot”
What is port 80 blocking and why is it important to understand its effects?
Port 80 blocking refers to the practice of blocking incoming and/or outgoing traffic on port 80, which is the default port for HTTP traffic. It is important to understand its effects because port 80 is commonly used for web browsing, and blocking it can prevent users from accessing websites or running web services.
How does port 80 blocking affect web browsing?
When port 80 is blocked, users may experience difficulties in accessing websites, as most websites use this port for HTTP traffic. The blocking can result in slow loading times, error messages, or complete inability to connect to websites.
What are the potential reasons for port 80 blocking?
The potential reasons for port 80 blocking can vary. It could be due to security measures implemented by network administrators or ISPs to prevent unauthorized access or to protect against certain types of web-based attacks, such as DDoS attacks. It could also be a result of misconfigurations or technical issues.
How can I troubleshoot port 80 blocking issues?
Troubleshooting port 80 blocking issues can involve several steps. Firstly, you can check if port 80 is being blocked by using tools like port scanners or network monitoring software. If it’s blocked, you can try disabling any firewall or security software temporarily to see if that resolves the issue. If not, you may need to contact your network administrator or ISP to investigate further.
Are there any alternatives to port 80 for web services?
Yes, there are alternative ports that can be used for web services. Some commonly used alternatives include port 8080, port 443 (for HTTPS traffic), and port 8000. However, it’s important to note that these alternative ports may also be subject to blocking or restricted access in certain network environments.


