In today’s digital age, security is a top concern for businesses and individuals alike. As technology continues to advance, so do the methods of exploitation and attack. One particular threat that has gained attention is the rogue access point – an unauthorized and unsecured wireless access point that poses a significant vulnerability to network security.
A rogue access point is a device that is set up within a network without proper authorization or oversight. These malicious devices are often hidden or disguised as legitimate access points, making them difficult to detect. Once connected to the network, they can establish a backdoor for attackers to gain unauthorized access to sensitive data or launch other malicious activities.
Prevention and mitigation of rogue access points require a multi-layered approach. First and foremost, organizations must educate employees about the risks associated with connecting to unauthorized wireless networks. Additionally, implementing strong security protocols, such as password protection and encryption, can help safeguard against unauthorized access.
Another countermeasure is the implementation of advanced detection systems that can identify and locate rogue access points. These systems use different methods, including wireless signal analysis, to identify unauthorized devices within the network. Regular monitoring and auditing of network traffic can also help identify any suspicious activities and provide an opportunity for swift action to be taken.
In conclusion, the threat posed by rogue access points is real and can have severe consequences for the security of a network. It is essential for organizations and individuals to be proactive in their approach to network security, implementing robust prevention measures and staying vigilant for any signs of unauthorized access. By taking these precautions, the risk of falling victim to a rogue access point attack can be significantly reduced.
Contents
Understanding Rogue Access Points

A rogue access point is an unsecured wireless access point that is connected to a network without authorization. It poses a significant threat to the security of a network as it can be used by attackers to gain unauthorized access to sensitive information.
Rogue access points can be set up by individuals with malicious intent or by employees who are unaware of the security risks. These access points can often go undetected, as they are designed to be stealthy and blend in with legitimate network devices.
Detection and mitigation of rogue access points is crucial for network security. Organizations need to have effective countermeasures in place to prevent the creation and exploitation of such vulnerabilities. This includes regularly monitoring the network for any signs of unauthorized access points and implementing strong wireless network security protocols.
There are several ways in which a rogue access point can be used as an attack vector. Attackers can use these access points to launch man-in-the-middle attacks, intercept sensitive data, or gain unauthorized access to the network. They can also be used as an entry point for further intrusion into the network.
To prevent the malicious use of rogue access points, organizations should implement wireless intrusion detection systems (WIDS) and intrusion prevention systems (IPS) that can detect and block any unauthorized activity on the wireless network. Regular security audits and vulnerability assessments can also help identify and address any potential weaknesses in the network.
In conclusion, understanding rogue access points and the threats they pose to network security is essential for implementing effective prevention and detection measures. By being proactive in securing wireless networks and regularly monitoring for any signs of unauthorized access, organizations can mitigate the risk of exploitation and protect sensitive information from falling into the wrong hands.
What is a Rogue Access Point?
A rogue access point is an unauthorized wireless access point that is connected to a network without proper authorization. It poses a serious security threat as it can be used by malicious actors to exploit vulnerabilities in the network and gain unauthorized access to sensitive information.
These rogue access points are created by attackers with the intention of bypassing security measures and gaining access to the network. They are often unsecured and can be easily disguised as legitimate access points, making them difficult to detect. Once connected to the network, they can be used as a stealthy point of intrusion or as a launching pad for further attacks.
The vulnerability of a network to rogue access points can be mitigated through various prevention and countermeasure techniques. Organizations must implement strong security measures to prevent the creation of unauthorized access points. This includes the use of intrusion detection systems, regular network monitoring, and the enforcement of strict access control policies.
To prevent the exploitation of rogue access points, it is important for organizations to educate their employees about the risks and provide them with guidelines on how to detect and report any suspicious wireless networks. Regular security audits and vulnerability assessments can also help identify and address any potential weaknesses in the network infrastructure.
Overall, the detection and mitigation of rogue access points is essential for maintaining the security of a network. By implementing proper security measures and keeping employees informed, organizations can minimize the risk of unauthorized access and protect sensitive information from potential attackers.
Risks Posed by Rogue Access Points
A rogue access point is a wireless access point that is unauthorized and not under the control of the network administrator. These rogue access points pose significant risks to network security, as they can be used by malicious individuals to gain unauthorized access to the network and exploit vulnerabilities.
One of the main risks posed by rogue access points is the potential for unauthorized intrusion into the network. By connecting to a rogue access point, an attacker can bypass established security measures and gain access to sensitive information. This can lead to data breaches, identity theft, and other malicious activities.
Rogue access points also create a threat to the overall network security by providing an entry point for attackers to launch attacks. Once connected to a rogue access point, an attacker can easily exploit vulnerabilities in the network or launch targeted attacks against other devices connected to the network.
Detection and mitigation of rogue access points are crucial for network security. Regularly scanning for unauthorized devices and implementing strong access control measures can help identify and address rogue access points. Additionally, implementing wireless intrusion detection systems and using encryption technologies can help prevent rogue access points from being used to compromise network security.
It is important to note that rogue access points are not limited to wireless networks. They can also occur in wired networks, where an attacker may connect an unauthorized device to gain access to the network or launch attacks. Network administrators should implement security measures to prevent unauthorized devices from being connected to the network.
In conclusion, rogue access points pose a significant threat to network security. To protect against these risks, network administrators must be vigilant in detecting and mitigating rogue access points, implementing strong access control measures, and regularly updating and patching network devices to address vulnerabilities.
Detecting Rogue Access Points
A rogue access point refers to an unauthorized wireless access point that has been installed on a network without the network administrator’s knowledge. This can pose a significant threat to the security of the network as it provides a potential entry point for malicious individuals or devices. Detecting these rogue access points is crucial for network security.
There are several methods for detecting rogue access points. One common approach is to use a wireless intrusion detection system (WIDS) or a wireless intrusion prevention system (WIPS). These systems monitor the wireless network for any unauthorized devices or access points, and can provide alerts or take automatic mitigation measures to protect the network.
Another method for detecting rogue access points is by using wireless scanning tools. These tools scan the surrounding area for wireless networks and devices, and can identify any unauthorized access points that may be present. By analyzing the signal strength, MAC addresses, or other parameters of the detected access points, network administrators can determine whether they are rogue or legitimate.
Network administrators can also conduct regular network audits to detect rogue access points. This involves manually inspecting the physical environment to look for any unauthorized devices or access points. Additionally, network traffic analysis can be used to identify suspicious or anomalous network behavior that may indicate the presence of rogue access points.
In order to prevent rogue access point threats, it is important to implement strong security measures. This includes securing the wireless network with strong encryption, enforcing strong passwords for authorized devices, and regularly updating firmware and security patches. Additionally, network segmentation and isolation can limit the potential impact of rogue access points on the overall network.
Wireless Site Surveys and Spectrum Analysis
A wireless site survey is a crucial step in securing a wireless network against rogue access points and other wireless threats. By conducting a site survey, administrators can identify potential vulnerabilities and unauthorized devices that may pose a security risk to the network.
During a wireless site survey, specialized tools are used to detect and analyze the wireless spectrum. This allows administrators to identify potential sources of interference and determine the best placement for access points to ensure optimal coverage and performance.
By conducting a wireless site survey, administrators can proactively identify and mitigate any unauthorized or rogue access points that may have been set up by malicious individuals. These rogue access points can be used to exploit vulnerabilities in the network and launch various wireless attacks.
Spectrum analysis is an important aspect of wireless site surveys, as it helps identify any interference or noise sources that may negatively impact the wireless network. By analyzing the spectrum, administrators can detect any malicious devices or signals that may pose a threat to the security of the network.
Once potential threats and vulnerabilities are identified through the site survey and spectrum analysis, administrators can take appropriate countermeasures to prevent unauthorized access and secure the network. This may include implementing strong encryption, authentication mechanisms, and intrusion detection and prevention systems.
Overall, conducting wireless site surveys and spectrum analysis plays a crucial role in the security of a wireless network. It helps administrators identify and address potential security risks, mitigate unauthorized access, and ensure the overall security and performance of the network.
Monitoring Network Traffic
Monitoring network traffic is a crucial aspect of ensuring network security. It involves closely observing the flow of data within a network to identify any potential vulnerabilities or threats. By monitoring network traffic, security professionals can detect any unsecured devices, rogue access points, or unauthorized intrusions.
One common vulnerability is the presence of rogue access points, which are unauthorized wireless devices that can provide an entry point for malicious attacks. By monitoring network traffic, security teams can quickly identify and detect any rogue access points and take appropriate countermeasures to mitigate the threat they pose.
Monitoring network traffic also helps in the early detection of any stealthy and malicious activities, such as unauthorized data access or exploits. With constant monitoring, security professionals can identify any abnormal patterns or suspicious behavior, enabling them to take immediate action to prevent any potential attacks.
Another important aspect of monitoring network traffic is the prevention and mitigation of any potential wireless threats. By closely monitoring network traffic, security teams can identify any weak points in the wireless network and implement necessary countermeasures to ensure the network’s integrity and confidentiality.
The use of network traffic monitoring tools and technologies is essential for effective monitoring. These tools provide real-time visibility into the network, allowing security professionals to analyze and interpret the data flow, identify any abnormalities, and respond appropriately. Additionally, they can generate reports and alerts for potential security issues, helping to streamline the security process.
In conclusion, monitoring network traffic is a critical step towards ensuring network security. It helps in detecting and preventing potential vulnerabilities, rogue access points, and unauthorized intrusions. By continuously monitoring network traffic, security teams can stay proactive in identifying and mitigating any potential threats, thereby maintaining the security and integrity of the network.
Preventing Rogue Access Points
In order to protect your network from unauthorized access and potential malicious attacks, it is crucial to implement robust countermeasures to prevent rogue access points from infiltrating your network. Detection and mitigation of these stealthy devices should be a top priority in any security strategy.
First and foremost, regular scanning and monitoring of the wireless spectrum is essential for the early detection of any unauthorized access points. This can be achieved by using specialized devices or software tools that can identify and analyze wireless signals, helping to pinpoint any potential vulnerabilities or suspicious activity.
Another important prevention measure is to enforce strict security policies for all devices connected to the network. This includes implementing strong and unique passwords, configuring devices to use the latest encryption protocols, and regularly updating firmware and software to patch any known vulnerabilities.
In addition, it is crucial to educate employees and users about the dangers of connecting to unsecured or unknown wireless networks. Creating awareness about the potential risks of using rogue access points can help prevent employees from accidentally connecting to malicious networks and inadvertently exposing sensitive information.
Furthermore, implementing intrusion detection and prevention systems (IDPS) can help identify and mitigate any potential threats or attacks. These systems can monitor network traffic, detect suspicious patterns, and automatically block any malicious activity, providing an additional layer of security against rogue access points.
Lastly, establishing a strong access control policy and implementing strong authentication methods, such as two-factor authentication, can further enhance the security of your network. By restricting access to authorized personnel only and requiring multiple authentication factors, the risk of unauthorized access through rogue access points can be significantly reduced.
In summary, preventing rogue access points is essential for maintaining the security and integrity of your network. By implementing detection and mitigation strategies, enforcing strict security policies, educating users, and implementing advanced security measures, you can effectively mitigate the risk of unauthorized access and potential malicious attacks through rogue access points.
Implementing Strong Network Access Controls
Network access controls play a crucial role in protecting against malicious intruders attempting to gain unauthorized access to a network. A rogue access point can be a major vulnerability, providing an entry point for attackers to exploit and compromise the security of the entire network.
To prevent such unauthorized access, it is essential to implement strong network access controls. One of the most effective countermeasures is the use of authentication and encryption protocols. By requiring users to provide credentials and encrypting data transmissions, the risk of unauthorized access is mitigated.
Another important security measure is the use of intrusion detection and prevention systems (IDPS). These systems can detect and alert network administrators to any suspicious or malicious activity, providing an early warning system that allows for immediate action to be taken.
Wireless networks are particularly vulnerable to rogue access points due to their stealth nature. To combat this, network administrators should regularly scan for unauthorized wireless devices and rogue access points. This can be done using specialized tools that detect and locate any unsecured wireless devices within the network.
In addition, network segmentation can also enhance network security by dividing the network into separate subnets, each with its own access controls. This limits the impact of a potential breach, as attackers will have limited access to other segments of the network.
Regular security audits and vulnerability assessments are crucial for identifying and addressing any weaknesses in network access controls. These assessments can highlight areas of improvement and help prioritize security measures to ensure the network remains protected against potential threats.
In conclusion, implementing strong network access controls is vital to prevent unauthorized access and mitigate the risk of rogue access points. By utilizing authentication protocols, IDPS, regular scanning, network segmentation, and security assessments, organizations can enhance their overall network security and protect against potential vulnerabilities and exploits.
Regularly Updating and Patching Network Devices
Prevention is key when it comes to securing your network against malicious attacks, especially those stemming from rogue access points. Regularly updating and patching your network devices is an essential countermeasure to mitigate the risk of intrusion and unauthorized access.
Wireless rogue access points present a significant threat to the security of your network. These unauthorized devices can exploit vulnerabilities in your network devices, allowing attackers to gain access to your network and potentially compromise sensitive information. By regularly updating and patching your network devices, you can stay one step ahead of these stealthy threats.
Detection of rogue access points can be challenging, as they often mimic legitimate network devices. However, by keeping your network devices up to date, you can close off known vulnerabilities that these rogue devices may attempt to exploit. Regular updates and patches ensure that your network devices have the latest security enhancements, making it harder for attackers to find points of weakness.
Regularly updating and patching your network devices is a proactive approach to network security. It helps to identify and address any potential vulnerabilities before they can be exploited by unauthorized users. By consistently monitoring for updates and applying patches promptly, you can strengthen the overall security of your network and reduce the risk of a rogue access point compromising your data.
Additionally, deploying intrusion detection systems and implementing strong authentication protocols can further enhance the security of your network. These countermeasures work hand in hand with regular updates and patches, creating a robust defense against rogue access points and other security threats.
Responding to Rogue Access Points
Responding to rogue access points is crucial for network security. Rogue access points are unauthorized devices that have been added to a network without proper authentication. These devices pose a significant threat to the network’s security, as they can be used to launch malicious attacks or exploit vulnerabilities.
To detect and respond to rogue access points, organizations should implement effective countermeasures. One important countermeasure is to regularly scan the network for unauthorized devices. This can be done through wireless intrusion detection systems (WIDS) or wireless intrusion prevention systems (WIPS). These systems can monitor the network for any unsecured or suspicious wireless access points.
Once a rogue access point is detected, it is crucial to take immediate action to mitigate the threat. The first step is to disable or disconnect the unauthorized device from the network. This can help prevent any potential intrusion or unauthorized access to the network. Additionally, organizations should investigate the origin of the rogue access point to identify possible security breaches or vulnerabilities.
After the rogue access point has been removed, organizations should also strengthen their network security measures to prevent future incidents. This can include implementing strong authentication protocols, encrypting wireless communications, and regularly updating network security software. By taking these proactive steps, organizations can better protect their network from rogue access points and other wireless security threats.
Isolating and Disconnecting Rogue Devices
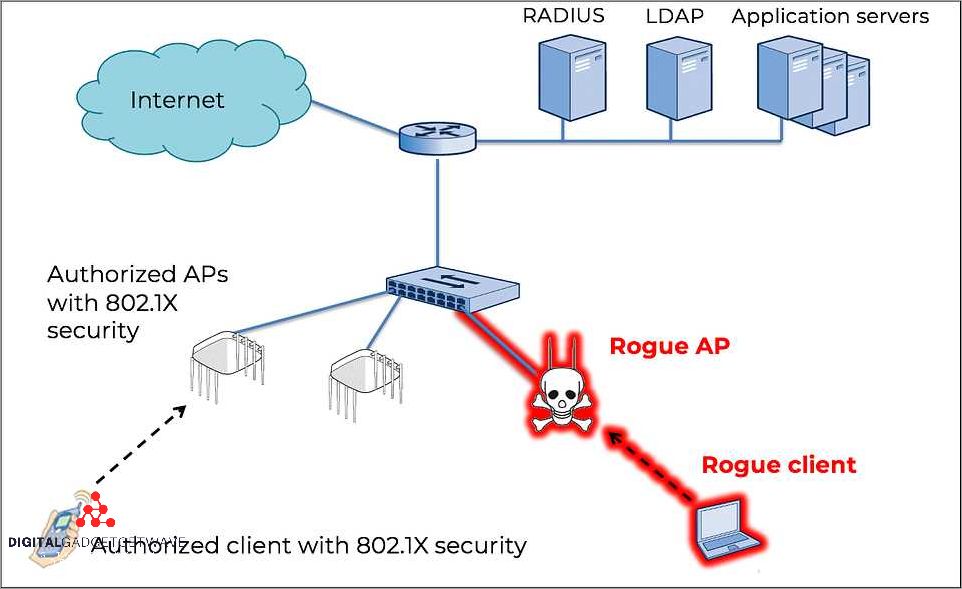
When it comes to the security of a network, isolating and disconnecting rogue devices is an essential countermeasure. Rogue access points are unsecured wireless access points that are set up without proper authorization and can potentially pose a significant threat to the network security. These devices can be intentionally set up by malicious individuals to gain unauthorized access to the network or used as a point of entry for an intrusion. Therefore, it is crucial to take active measures to mitigate this vulnerability and prevent any potential attacks.
One important method for isolating and disconnecting rogue devices is through wireless intrusion detection and prevention systems (WIDPS). These systems can help identify unauthorized or rogue access points within the network by actively scanning for any suspicious wireless signals. The WIDPS can detect the presence of rogue devices and initiate a mitigation response to remove them from the network.
Another approach to isolating and disconnecting rogue devices is through proactive monitoring and regular network audits. This involves regularly scanning the network for any unauthorized access points or devices. By keeping an up-to-date inventory of all authorized devices on the network, it becomes easier to identify and remove any rogue devices that may be attempting to infiltrate the network.
In addition, network administrators can also implement strict security protocols and policies regarding the connection of devices to the network. This includes requiring strong authentication and encryption for wireless connections, as well as implementing access controls to restrict unauthorized devices from connecting to the network. By enforcing these security measures, the risk of rogue access points exploiting vulnerabilities and gaining access to the network can be significantly reduced.
Overall, isolating and disconnecting rogue devices is a critical step in ensuring the security of a network. By implementing measures such as wireless intrusion detection and prevention systems, regular network audits, and strict security protocols, organizations can effectively detect and mitigate the threat of rogue access points and protect their network from malicious attacks.
Investigating and Remediating Security Breaches
When a security breach occurs, it is crucial to conduct a thorough investigation in order to identify the intrusion and mitigate any potential damage. The first step in the investigation process is to gather information about the breach, including the access points, devices, and networks that were compromised. This information will help in understanding the scope and severity of the breach.
A common cause of security breaches is the presence of rogue access points, which are unauthorized devices that connect to a network and provide unsecured access to attackers. These rogue access points often operate in stealth mode, making it difficult to detect them. It is important to perform a comprehensive scan of the network to identify any rogue access points and take appropriate countermeasures to remove them.
Once the intrusion has been identified and the rogue access points have been removed, it is essential to investigate the attack vector and determine the method used to exploit the network’s vulnerabilities. This information will help in implementing effective security measures to prevent future attacks.
During the investigation, it is important to consider all possible sources of compromise, including both internal and external threats. Internal threats may originate from disgruntled employees or compromised devices, while external threats can come from hackers or malicious software. By analyzing the different sources of threat, it is possible to develop a comprehensive security strategy that addresses vulnerabilities from all angles.
In addition to investigating the breach, it is crucial to implement immediate countermeasures to remediate the security issues. This may include patching vulnerabilities, updating security software, changing passwords, or isolating compromised devices from the network. These mitigation measures will help in minimizing the impact of the breach and preventing further unauthorized access.
FAQ about topic “Rogue Access Point: How to Safeguard Your Network”
What is a rogue access point?
A rogue access point is an unauthorized wireless access point that is connected to a network without the knowledge or consent of the network administrator. It can be set up by an attacker to gain unauthorized access to a network or to intercept and compromise network traffic.
How can a rogue access point be harmful to my network?
A rogue access point can be harmful to your network in multiple ways. It can be used by attackers to gain unauthorized access to sensitive information, steal data, or launch attacks on other devices on the network. It can also create a potential security hole, as it may not have the same level of security as the authorized access points on the network, making it easier for attackers to exploit.


