What is a data spill and how to prevent it: A comprehensive guide
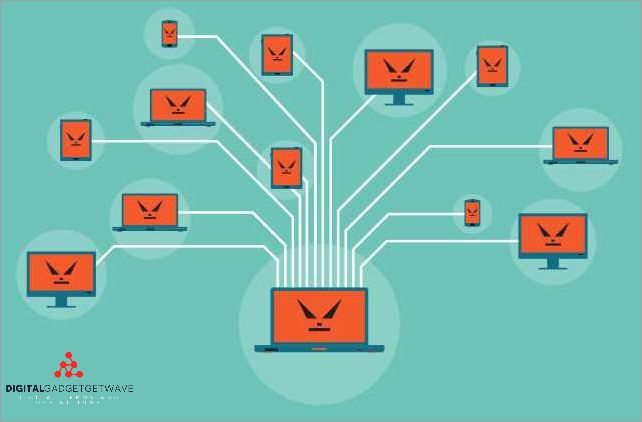
Data spills, also known as unauthorized data leaks or data exposures, occur when sensitive information is released or disclosed without proper authorization. It is a violation of security protocols and can lead to severe consequences for individuals and organizations alike. Data spills can range from accidental incidents to deliberate compromises, but regardless of the cause, ...