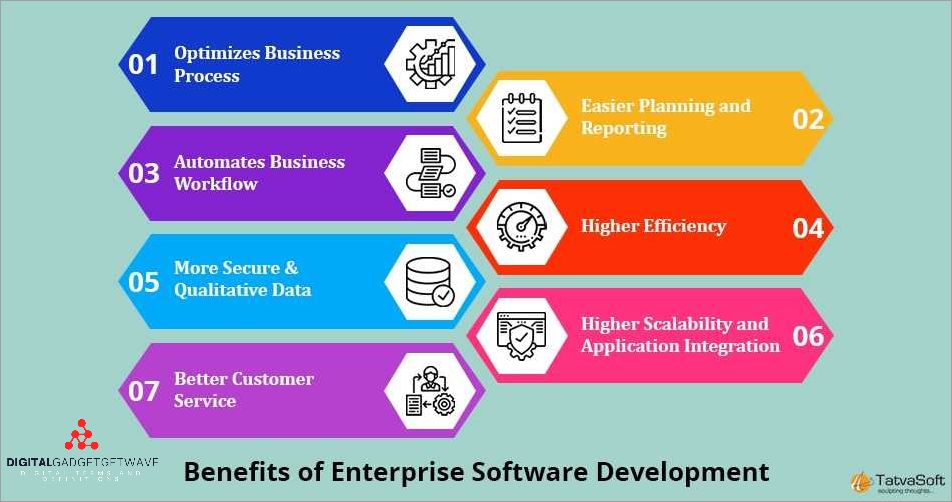
Understanding Enterprise-level Solutions: A Path to Business Success
Enterprise-level refers to a high level of integration, analytics, performance, and architecture in the management of an organization’s infrastructure, platforms, and software solutions. It provides a comprehensive and scalable approach to meet the complex needs of businesses. At the core of enterprise-level solutions is the integration of various components across an organization’s systems and services. ...