Key Networking Diagram Symbols and Their Meanings – Essential Guide
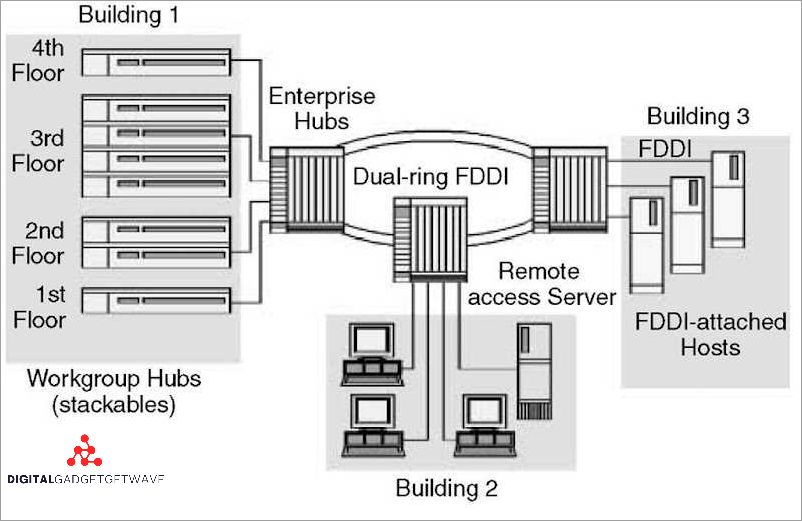
Networking diagrams are essential tools for visualizing and designing complex networks, whether they are wired or wireless. These diagrams use symbols to represent different network equipment and connections, making it easier for network administrators and technicians to understand and manage the network. There are various symbols used in networking diagrams that represent different devices and ...