In today’s digital landscape, businesses and individuals face ever-increasing threats to their network security. Malware, data breaches, and hacking incidents are becoming more sophisticated and frequent, exploiting vulnerabilities in networks and systems. To defend against these attacks, organizations must implement robust cybersecurity measures and technologies, one of which is ESP (Encapsulating Security Payload).
ESP is a security protocol used in network communication to ensure the confidentiality, integrity, and authentication of data. It acts as a defense mechanism, protecting the network from unauthorized access, intrusion, and phishing attempts. By encrypting the data packets, ESP makes it difficult for attackers to intercept and decipher sensitive information, preserving privacy and preventing potential breaches.
One of the key components of ESP technology is the firewall, which acts as a barrier between the internal network and external threats. It monitors incoming and outgoing traffic, filtering out malicious activities and unauthorized access attempts. The firewall also plays a crucial role in detecting and mitigating ongoing cyber attacks, providing early warning systems and incident response capabilities.
ESP technology enhances network security by implementing robust authentication mechanisms. This ensures that only authorized individuals can access the network and its resources. By utilizing encryption and authentication techniques, ESP technology safeguards sensitive data from unauthorized modifications and protects against data tampering and impersonation.
By deploying ESP technology, organizations can significantly enhance their cyber defenses and ensure the safety and protection of their networks. It provides a solid foundation for preventing cyber attacks, mitigating vulnerabilities, and safeguarding critical data. In an ever-evolving cyber landscape, ESP technology is a crucial component in the fight against cyber threats and maintaining network security.
In conclusion, the use of ESP technology plays a vital role in safeguarding networks from cyber attacks. With its encryption, authentication, and defense mechanisms, it provides an effective shield against potential vulnerabilities. As cyber threats continue to evolve, organizations must prioritize the implementation of technologies like ESP to maintain a robust cybersecurity posture and protect their networks and data from potential breaches.
Contents
- 1 Enhancing Cyber Security with ESP Technology
- 2 Ensuring Network Safety and Protection
- 3 Advancements in ESP Technology
- 4 Challenges in Implementing ESP Technology
- 5 FAQ about topic “Enhancing Cyber Security with ESP Technology: Ensuring Network Safety and Protection”
- 6 What is ESP technology and how does it enhance cyber security?
- 7 Can ESP technology protect against all types of cyber attacks?
- 8 Is ESP technology suitable for small businesses?
- 9 What are the potential drawbacks of using ESP technology?
- 10 Can ESP technology protect against insider threats?
Enhancing Cyber Security with ESP Technology
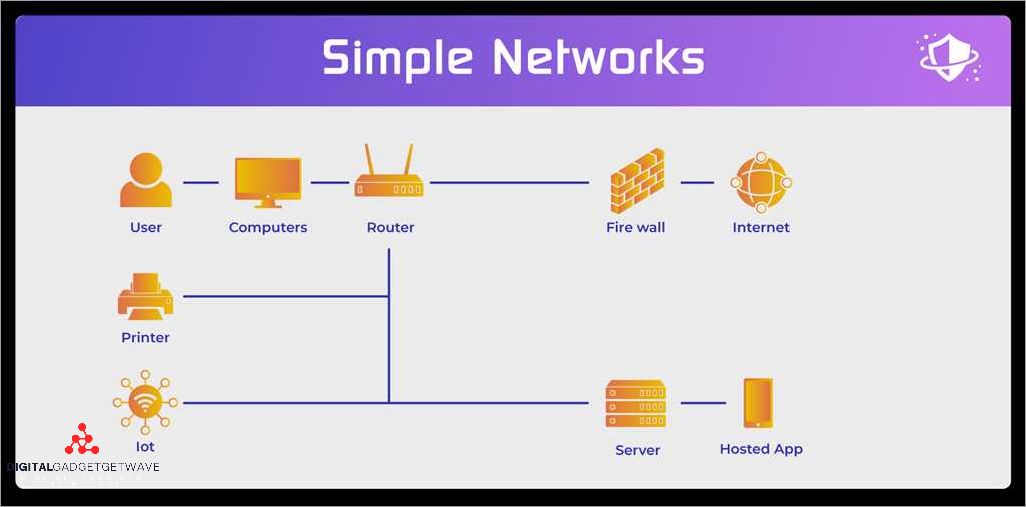
In today’s increasingly digitized world, cyber security has become a paramount concern for individuals, organizations, and governments. Protecting sensitive data and ensuring network safety are crucial in safeguarding against various cyber threats such as malware attacks, intrusions, hacking, and phishing attempts.
One technology that has proven to be effective in enhancing cyber security is ESP (Encapsulating Security Payload). ESP provides a layer of protection by encrypting data packets, preventing unauthorized access and maintaining the privacy of information transmitted over the network.
With ESP technology, organizations can defend against a wide range of threats and incidents. By implementing strong encryption algorithms, ESP renders data unreadable to anyone who does not possess the necessary decryption keys. This helps in safeguarding sensitive information from potential breaches and unauthorized access.
In addition to encryption, ESP also facilitates authentication, ensuring that only legitimate users are granted access to the network. This helps prevent malicious actors from infiltrating the system and carrying out cyber attacks or unauthorized activities.
Furthermore, ESP technology can be integrated with firewall systems to create a robust defense mechanism against cyber threats. Firewalls equipped with ESP can analyze network traffic, identify suspicious activities, and block potential threats in real-time, thereby minimizing the risk of successful cyber attacks.
By utilizing ESP technology, organizations can enhance their cyber security posture and mitigate the risks associated with data breaches and privacy violations. Implementing ESP as part of a comprehensive security strategy strengthens the overall resilience of the network, enabling proactive detection and effective response to cyber threats.
In conclusion, ESP technology plays a crucial role in enhancing cyber security by providing protection, encryption, authentication, and defense against various cyber threats. As the digital landscape continues to evolve, organizations must prioritize the implementation of advanced security measures, including ESP, to ensure the safety and integrity of their networks and data.
Ensuring Network Safety and Protection
In the digital age, ensuring network safety and protection is of paramount importance. With the increasing reliance on data and information exchange, networks are constantly at risk of cyber threats and attacks. To safeguard against these risks, it is essential to implement strong security measures and utilize advanced technologies such as ESP (Enhanced Security Protocol).
One crucial aspect of network safety is the use of firewalls. Firewalls act as a barrier between a trusted internal network and an external network, monitoring and filtering incoming and outgoing network traffic. By analyzing data packets and checking for vulnerabilities or suspicious activity, firewalls provide a line of defense against potential attacks.
To further enhance network protection, the identification and mitigation of vulnerabilities is essential. This can be achieved through regular security audits and vulnerability assessments. By identifying weaknesses or security flaws in the network infrastructure, organizations can take proactive measures to address and patch these vulnerabilities, ensuring a more secure network environment.
Another critical aspect of network safety is incident response and defense. Organizations should have a well-defined incident response plan in place to effectively handle and mitigate any cyber threats or breaches. This includes rapid detection and containment of incidents, as well as proper authentication and authorization procedures to prevent unauthorized access to the network.
Cyber threats such as malware, phishing, and hacking are constantly evolving. Therefore, it is crucial to employ advanced encryption technologies to protect sensitive data and maintain privacy. By encrypting data transmission and storage, organizations can ensure that even if an intrusion occurs, the data remains inaccessible and secure.
Education and awareness are also vital in ensuring network safety and protection. Organizations should provide regular training and workshops to employees, educating them about common cyber threats and best practices for maintaining network security. This includes raising awareness about phishing attacks, social engineering tactics, and the importance of strong passwords and authentication protocols.
In conclusion, network safety and protection are crucial in the modern digital landscape. By implementing advanced technologies like ESP, utilizing firewalls, identifying vulnerabilities, and having a comprehensive incident response plan, organizations can strengthen their defense against cyber threats, ensuring a safe and secure network environment.
Benefits of Enhancing Cyber Security with ESP Technology
Enhancing cyber security with ESP (Encapsulating Security Payload) technology offers numerous benefits in protecting networks and ensuring data safety. ESP provides a layer of secure communication between network devices, preventing unauthorized access and defending against potential attacks.
Authentication: ESP technology utilizes authentication methods to verify the identity of network devices and users, ensuring that only authorized entities can access the system. This helps to prevent hacking attempts and unauthorized intrusions.
Vulnerability Protection: With the use of ESP technology, networks are protected from potential vulnerabilities and weaknesses. ESP can detect and address vulnerabilities in the network infrastructure, minimizing the risks of cyber attacks and data breaches.
Data Defense: ESP technology safeguards sensitive data by encrypting it, making it unreadable and inaccessible to unauthorized users. This ensures the privacy and integrity of data, protecting against potential incidents of data leakage or theft.
Malware and Phishing Prevention: ESP technology can identify and block malware and phishing attacks, providing an additional layer of defense against malicious software and fraudulent activities. This helps to maintain the integrity of the network and ensure the safety of users’ personal information.
Intrusion Detection and Incident Response: ESP technology enables real-time monitoring of network traffic, allowing for the detection of any suspicious activities or attempted intrusions. This facilitates quick incident response, minimizing potential damages and mitigating the impact of cyber attacks.
Enhanced Firewall and Encryption: ESP technology reinforces the existing network firewall and encryption measures, providing additional protection against unauthorized access and data breaches. This helps to fortify the network’s defense system and ensures the confidentiality of sensitive information.
Threat Detection and Prevention: ESP technology can analyze network traffic patterns and detect potential threats and attacks, allowing for the implementation of proactive measures to prevent cyber incidents. This helps organizations stay ahead of emerging cyber threats and protect their networks from potential damages.
Overall Network Safety and Protection: By enhancing cyber security with ESP technology, organizations can achieve a higher level of network safety and protection. ESP provides robust security features that help to mitigate the risks associated with cyber attacks, ensuring the continuity of operations and safeguarding the organization’s reputation.
Implementing ESP Technology for Network Safety
With the increasing number of cyber threats and attacks, implementing Enhanced Security Protocol (ESP) technology is crucial for ensuring network safety and protection. ESP technology acts as a firewall against potential breaches and unauthorized access to valuable data.
One of the key features of ESP technology is its ability to provide encryption, which helps secure sensitive information from interception and unauthorized access. By encrypting data packets, ESP technology ensures that even if they are intercepted during transmission, they cannot be deciphered without the proper decryption key.
Furthermore, ESP technology helps identify and patch vulnerabilities that can be exploited by hackers and malware. By actively monitoring network traffic, it can detect and block potential intrusion attempts, preventing incidents before they occur. This proactive defense against threats helps organizations maintain the integrity and privacy of their data.
Implementing ESP technology also enhances network authentication processes, strengthening overall security measures. By verifying the identity of users and devices accessing the network, organizations can ensure that only authorized personnel can access sensitive information. This reduces the risk of unauthorized access and potential data breaches.
Overall, the implementation of ESP technology is crucial in the face of increasing cyber threats and attacks. It provides enhanced protection against hacking attempts, malware, and unauthorized access to data. By encrypting data, identifying vulnerabilities, and strengthening authentication processes, ESP technology helps organizations maintain network safety and safeguard valuable information.
Advancements in ESP Technology
In today’s cyber landscape, organizations face an ever-increasing number of security threats and incidents. Cyber attacks, including intrusions, data breaches, malware, and hacking attempts, continue to pose a significant risk to the privacy and data security of businesses. As a result, the need for robust defense mechanisms to protect networks and systems has become crucial.
ESP (Encapsulating Security Payload) technology has emerged as a vital tool in the fight against cyber threats. ESP provides a secure and encrypted channel for data transmission, ensuring that sensitive information remains protected from unauthorized access or interception. This protocol enhances network security by implementing authentication and cryptographic algorithms that prevent tampering and interception of data packets.
One of the key advantages of ESP technology is its ability to safeguard against various types of attacks, including hacking, phishing, and malware. By encrypting data, ESP mitigates the risk of unauthorized access, making it significantly harder for cybercriminals to extract sensitive information from the network. Additionally, ESP technology complements other security measures such as firewalls and intrusion detection systems, providing an additional layer of protection against potential vulnerabilities.
With the advancement of ESP technology, organizations can now optimize their network security measures further. This includes the implementation of encryption algorithms that are resistant to brute-force attacks, ensuring the confidentiality and integrity of data. ESP also enables organizations to define customized security policies, ensuring that only authorized users can access certain resources or perform specific actions within the network.
Overall, advancements in ESP technology have empowered organizations in their efforts to enhance cyber security. By implementing robust encryption and authentication techniques, ESP technology has proven to be a valuable asset in the protection of networks, data, and privacy. As cyber threats continue to evolve, organizations can rely on ESP as a reliable defense mechanism against the ever-changing landscape of cyber attacks.
Emerging Trends in Cyber Security
With the increasingly interconnected world, cyber security has become a critical concern for individuals, organizations, and governments. As technology continues to advance, new cyber threats and attack vectors are constantly emerging, making it essential for cyber security professionals to stay updated on the latest trends.
One of the key trends in cyber security is the focus on defense and protection. As cyber attacks become more sophisticated, organizations are investing in robust defense mechanisms to safeguard their networks and data. This includes implementing firewalls, intrusion detection systems, and intrusion prevention systems to detect and prevent unauthorized access.
Encryption is another important trend in cyber security. By encrypting data, organizations can ensure that even if it falls into the wrong hands, it remains unreadable and useless. Encryption helps protect sensitive information, such as customer data or financial records, from unauthorized access and ensures privacy.
Cyber security incidents, such as hacking and malware attacks, are on the rise. This has led to a greater focus on threat intelligence and proactive monitoring. Organizations are investing in advanced tools and technologies to identify and mitigate potential threats before they can cause significant damage or data breaches.
Authentication and access control are crucial aspects of cyber security. With the increasing number of devices and users connected to networks, ensuring that only authorized individuals gain access to sensitive data has become a challenge. As a result, multi-factor authentication and biometrics are emerging as popular authentication methods to enhance security.
Lastly, the identification and patching of vulnerabilities are essential in preventing cyber attacks. Organizations are increasingly conducting regular vulnerability assessments and penetration testing to identify weaknesses in their networks. These tests help organizations understand their level of risk and take necessary measures to strengthen their security defenses.
In conclusion, as the cyber threat landscape evolves, the field of cyber security must adapt and innovate. By staying abreast of emerging trends and adopting advanced technologies, organizations can effectively protect their networks, data, and privacy from cyber threats and breaches.
The Role of ESP Technology in Cyber Security
With the ever-increasing threats in the cyber world, ensuring the security of networks and protecting privacy has become a top priority. ESP (Encapsulating Security Payload) technology plays a crucial role in strengthening the defense against cyber attacks and breaches.
One of the key features of ESP technology is its ability to provide a secure and encrypted communication channel between two endpoints in a network. By encrypting data, ESP ensures that even if an intrusion occurs, the attackers will be unable to access sensitive information. This encryption helps in protecting against various types of cyber threats, such as malware, hacking, phishing, and data breaches.
In addition to encryption, ESP also provides authentication, which verifies the identity of any device or user attempting to access the network. This authentication process helps in identifying potential vulnerabilities and defending against unauthorized access. It ensures that only authorized entities can access the network, reducing the risk of intrusion and ensuring the overall security of the network.
ESP technology works in conjunction with other security measures, such as firewalls, to provide robust protection against cyber attacks. Firewalls actively monitor and filter incoming and outgoing network traffic, preventing unauthorized access and blocking potential threats. When combined with ESP technology, firewalls can create a strong line of defense to safeguard against intrusion attempts and malicious activities.
Furthermore, ESP technology enables the implementation of secure virtual private networks (VPNs) that allow users to securely connect to a network from any location. These VPNs ensure that data transmitted over the network remains encrypted and protected, even when accessed from remote or untrusted locations. This capability is particularly important for organizations that have a distributed workforce or need to provide secure remote access to their networks.
In conclusion, ESP technology plays a vital role in enhancing cyber security by providing encryption, authentication, and secure communication channels. With the increasing sophistication of cyber threats, the use of ESP technology is essential to protect sensitive data, defend against attacks, and secure network infrastructure. By incorporating ESP into their security strategies, organizations can strengthen their defenses and ensure the privacy and safety of their networks.
Future of Cyber Security with ESP Technology
As technology continues to evolve, the future of cyber security is being shaped by the emergence of ESP (Enhanced Security Protocol) technology. ESP technology provides advanced measures to enhance network safety and protection against hacking, intrusion, and other cyber threats.
One of the key components of ESP technology is the implementation of a robust firewall system. This firewall acts as a barrier between the internal network and the external world, monitoring and controlling incoming and outgoing network traffic. It helps to prevent unauthorized access and defends against attacks by blocking suspicious or malicious activities.
Encryption plays a crucial role in the future of cyber security with ESP technology. By encrypting sensitive data, ESP ensures that even if an attacker manages to intercept the data, it is meaningless without the decryption key. This helps to protect confidential information and prevent unauthorized access.
ESP technology focuses on addressing vulnerabilities and enhancing the overall defense of a network. It constantly monitors network traffic and conducts real-time threat analysis to identify any potential breaches or incidents. By proactively detecting and responding to threats, ESP technology ensures that networks are well-protected from cyber attacks.
Phishing attacks, one of the most common cyber threats, are also tackled by ESP technology. By implementing strong authentication mechanisms, such as two-factor authentication, ESP technology helps to prevent phishing attempts and ensures that only authorized users can access sensitive data and systems.
In addition to protecting against external threats, ESP technology also addresses internal risks such as malware. With its advanced malware detection and prevention capabilities, ESP technology helps to identify and eliminate potential malware infections, safeguarding the network and data from harmful viruses and malicious software.
In conclusion, the future of cyber security with ESP technology is promising. With its focus on network protection, encryption, threat detection, and vulnerability management, ESP technology provides a comprehensive approach to ensure the security and protection of network systems and data, safeguarding it against cyber attacks and unauthorized access.
Challenges in Implementing ESP Technology
Implementing ESP technology faces several challenges due to the ever-evolving nature of cyber threats and the complexity of network systems. One of the main challenges is the constant emergence of new malware and intrusion techniques that can bypass traditional security measures. These threats can compromise the integrity and confidentiality of data, making it essential for organizations to deploy ESP technology for enhanced protection.
Another challenge in implementing ESP technology is the need to effectively manage firewalls and incident response mechanisms. ESP technology relies on firewalls to monitor and control network traffic, ensuring only authorized access. However, managing firewalls can be challenging due to the constant updates required to address new vulnerabilities and protect against potential breaches.
Encryption is a crucial aspect of ESP technology, providing secure communication channels and protecting data from unauthorized access. However, implementing encryption mechanisms can be complex, particularly when it comes to establishing secure authentication protocols and key management systems.
Moreover, organizations must be vigilant in identifying and addressing potential weaknesses and vulnerabilities in their networks. Cyber attacks and hacking attempts constantly evolve, making it essential for organizations to regularly update their ESP technology and defense mechanisms to protect against emerging threats.
Phishing attacks pose a significant challenge in implementing ESP technology. These attacks involve tricking individuals into revealing sensitive information through fraudulent means, compromising network security and privacy. Organizations must educate their employees about phishing threats and implement robust authentication measures to prevent unauthorized access.
In summary, implementing ESP technology faces challenges related to the constant evolution of cyber threats, the management of firewalls and incidents, the complexity of encryption mechanisms, the identification and addressing of vulnerabilities, and the prevention of phishing attacks. Overcoming these challenges is crucial to ensuring network safety and protection in the face of ever-growing cyber threats.
Overcoming Obstacles to ESP Technology Implementation
The implementation of ESP (Enhanced Security Protocol) technology plays a crucial role in ensuring network safety and protecting against cyber threats. However, there are several obstacles that organizations may face when adopting ESP technology.
One of the main obstacles is the constant evolution of hacking techniques and cyber threats. As hackers become more sophisticated, they are constantly finding new ways to exploit vulnerabilities in network systems. ESP technology needs to keep up with these evolving threats to provide effective data protection and defense against intrusion.
Another challenge is ensuring the privacy of data in the event of an incident. With the increasing frequency and severity of cyber attacks, organizations need to have proper measures in place to protect sensitive information. ESP technology can provide a strong defense against unauthorized access and help mitigate the risks associated with data breaches.
Implementing ESP technology may also face resistance from existing network security infrastructure, such as firewalls and intrusion detection systems. These traditional security measures may not integrate well with ESP technology and could result in compatibility issues. Organizations need to carefully evaluate their current security defenses and ensure they are optimized to work effectively with ESP technology.
Furthermore, the implementation of ESP technology requires proper training and authentication protocols for employees. Without proper training, employees may unknowingly fall victim to phishing attacks or unknowingly introduce malware into the network. It is essential to educate employees about the importance of cybersecurity and provide them with the necessary tools to identify and report potential threats.
To overcome these obstacles, organizations should invest in robust encryption mechanisms and regularly update their security protocols. Collaboration with security vendors and experts can also help in identifying and addressing vulnerabilities in the network. Implementing a comprehensive cybersecurity strategy that includes ESP technology as a part of the defense system will provide an added layer of protection against cyber attacks.
In conclusion, while the implementation of ESP technology may face obstacles, organizations can overcome these challenges by staying updated with evolving threats, ensuring data privacy, addressing compatibility issues, and providing proper training and authentication protocols. By overcoming these obstacles, organizations can enhance their cyber resilience and strengthen their overall network security.
Addressing the Limitations of ESP Technology
In today’s interconnected world, network protection against hacking threats and cyber attacks is of utmost importance. ESP technology, which stands for Encapsulating Security Payload, provides a secure communication channel by encrypting data packets. This encryption plays a crucial role in ensuring the privacy and security of data, but ESP technology also has its limitations.
One limitation is that ESP technology focuses primarily on encryption and does not provide a comprehensive defense against all types of network breaches. While encryption is important for securing data during transmission, it does not address other vulnerabilities such as intrusion detection, malware protection, and authentication.
Another limitation is that ESP technology is vulnerable to attacks that target the encryption algorithm itself. As technology evolves, so do the methods used by hackers to exploit vulnerabilities. This means that ESP technology needs to be regularly updated and strengthened to protect against emerging threats.
To overcome these limitations, it is essential to implement additional security measures alongside ESP technology. This includes having a robust firewall that monitors and filters incoming and outgoing network traffic. It also involves using advanced malware detection tools to identify and eradicate any potential threats.
Furthermore, a multi-layered approach to network security is crucial for addressing the limitations of ESP technology. This involves using a combination of encryption, authentication, intrusion detection systems, and incident response plans. By implementing a comprehensive defense strategy, organizations can enhance their network security and mitigate the risks of cyber attacks and data breaches.
In conclusion, while ESP technology provides an important layer of encryption for network security, it is essential to address its limitations. By implementing additional security measures and adopting a multi-layered defense approach, organizations can ensure comprehensive protection against cyber threats and enhance network security.
FAQ about topic “Enhancing Cyber Security with ESP Technology: Ensuring Network Safety and Protection”
What is ESP technology and how does it enhance cyber security?
ESP technology, also known as Encapsulating Security Payload, is a protocol used to provide confidentiality, integrity, and authentication for data packets transmitted over a network. It enhances cyber security by encrypting the data, ensuring that only authorized recipients can access and understand it. It also verifies the integrity of the data, detecting any modifications or tampering attempts. Additionally, ESP technology provides authentication, allowing the recipient to verify the identity of the sender. Overall, ESP technology helps ensure network safety and protection by safeguarding the transmission of sensitive information.
Can ESP technology protect against all types of cyber attacks?
While ESP technology is a powerful tool for enhancing cyber security, it cannot protect against all types of cyber attacks. It primarily focuses on securing data transmission by encrypting and authenticating the packets. However, it does not protect against attacks such as Distributed Denial of Service (DDoS) attacks, social engineering, or software vulnerabilities. To ensure comprehensive protection, organizations should implement a multi-layered approach that includes not only ESP technology but also other security measures such as firewalls, intrusion detection systems, and regular software updates.
Is ESP technology suitable for small businesses?
Yes, ESP technology is suitable for small businesses. In fact, it can be particularly beneficial for small businesses that may have limited resources for cybersecurity. By implementing ESP technology, small businesses can encrypt their data transmission, making it more difficult for potential attackers to intercept and access sensitive information. ESP technology also helps verify the authenticity of the sender, ensuring that small businesses are communicating with trusted entities. While small businesses may need to invest in the necessary infrastructure and expertise to implement ESP technology, the enhanced cyber security it provides can be invaluable in protecting their network.
What are the potential drawbacks of using ESP technology?
While ESP technology offers many benefits, there are some potential drawbacks to consider. One drawback is the computational overhead of encryption and decryption, which can slow down network performance, especially in high-traffic environments. This may require organizations to invest in more powerful hardware to ensure smooth network operation. Additionally, ESP technology relies on encryption keys, which need to be securely managed and updated regularly to maintain the integrity of the system. Failure to do so could compromise the security of the network. Lastly, the implementation of ESP technology requires expertise, which may require additional training or hiring of IT professionals.
Can ESP technology protect against insider threats?
ESP technology alone may not be sufficient to protect against insider threats. Insider threats involve malicious actions or negligence from individuals who have authorized access to an organization’s network. While ESP technology can encrypt data transmission, it cannot prevent authorized insiders from intentionally or unintentionally compromising the security of the network. To mitigate the risk of insider threats, organizations should implement additional measures such as access controls, employee training, and monitoring systems that can detect suspicious behavior. By combining these measures with ESP technology, organizations can enhance their overall cyber security posture and better protect against insider threats.


