
A host-based firewall system is an essential component of any network’s security infrastructure. It acts as a policy-based traffic filter, allowing or blocking access to and from a host based on predefined rules. Unlike a network-based firewall that protects an entire network, a host-based firewall is installed on individual devices, providing a higher level of protection at the host level.
The host-based firewall system monitors incoming and outgoing network traffic, including services, to ensure that only authorized communication is allowed. It examines each packet of data and applies security rules to determine if it should be permitted or rejected. By logging and auditing the firewall activities, organizations can have a better understanding of potential security threats and take necessary measures to enhance their security posture.
One of the main advantages of a host-based firewall system is its ability to provide protection against both external and internal threats. It protects the host from unauthorized access attempts, intrusion attempts, and malware infections that may originate from both internal and external sources. Additionally, a host-based firewall can be configured to allow or restrict access to specific network resources, such as files or applications, based on the user’s role or the device’s location.
Effective management and monitoring of the host-based firewall system are critical for maintaining network security. Organizations should regularly update and review the firewall rules to ensure they align with the organization’s security policies and compliance requirements. Continuous monitoring of the firewall logs and alerts can help detect any suspicious activities or potential intrusion attempts.
Furthermore, a host-based firewall system can be integrated with other security technologies, such as virtual private networks (VPNs), to enhance network security. By combining the protection provided by the host-based firewall with the encryption and authentication capabilities of a VPN, organizations can secure their network communications and ensure confidentiality, integrity, and authenticity.
In conclusion, a host-based firewall system is an integral part of a comprehensive network security strategy. Its configuration, management, and monitoring are crucial for protecting network resources, preventing unauthorized access, and detecting potential security threats. Organizations should consider implementing a host-based firewall system to strengthen their overall security posture and safeguard their sensitive data.
Contents
- 1 Understanding the basics
- 2 Key features of host-based firewall system
- 3 Benefits of using a host-based firewall system
- 4 Implementing a host-based firewall system
- 5 Best practices for managing a host-based firewall system
- 6 FAQ about topic “Understanding the Basics of Host-based Firewall Systems”
- 7 What is a host-based firewall system?
- 8 How does a host-based firewall system work?
- 9 What are the benefits of using a host-based firewall system?
- 10 Can a host-based firewall system protect against all types of cyber threats?
- 11 How can I configure a host-based firewall system?
Understanding the basics
A host-based firewall is a device that is used for management, monitoring, and configuration of network security. It provides protection against intrusion by controlling access to ports and services on a host or network. The firewall is typically installed on an individual host or server, hence the term “host-based” firewall.
One of the key features of a host-based firewall is its ability to create and enforce rules that determine which traffic is allowed to pass through the firewall and which traffic is blocked. These rules can be based on various criteria such as IP addresses, ports, and protocols. By configuring these rules, administrators can define the level of access and security for their network.
In addition to enforcing access rules, a host-based firewall also performs logging and monitoring functions. This means that it keeps track of all the traffic that passes through the firewall and logs any suspicious or unauthorized activity. This logging feature is important for security audits and troubleshooting purposes.
A host-based firewall can also be used in conjunction with a Virtual Private Network (VPN) to enhance network security. A VPN creates a secure connection over a public network, such as the internet, and encrypts all data that is sent between the host and the network. By combining a host-based firewall with a VPN, organizations can ensure that all data passing through the firewall is encrypted and secure.
Overall, a host-based firewall is a crucial component of a network security system. It provides an additional layer of protection by controlling access to a host or network, enforcing access rules, monitoring traffic, and logging suspicious activity. By implementing a host-based firewall, organizations can enhance the security of their network and protect against unauthorized access and attacks.
Key features of host-based firewall system

A host-based firewall system is a device or software that provides security and access control to a host or individual computer. It operates on specific rules and policies to protect the host from unauthorized access and potential threats.
The key features of a host-based firewall system include:
- Rule-based protection: The firewall system uses a set of predefined rules to determine which network traffic is allowed or blocked. These rules can be configured based on specific requirements and can be adjusted to provide customized protection.
- Audit and logging: The firewall system maintains an audit log of all network traffic and events. This helps in identifying any intrusion attempts or suspicious activities. The log can be reviewed for analysis and investigation purposes.
- Management and configuration: The firewall system provides a user interface or command-line interface for managing and configuring the firewall policies. It allows administrators to define access control rules, enable/disable services, and configure other security settings.
- Intrusion detection and prevention: The host-based firewall system includes intrusion detection and prevention capabilities to detect and block malicious activities and attacks. It can monitor network traffic, analyze patterns, and take appropriate actions to prevent intrusion attempts.
- Protection for specific ports and services: The firewall system can be configured to provide protection for specific ports and services running on the host. It allows administrators to define access rules for individual ports and services, ensuring that only authorized traffic is allowed.
- VPN support: The firewall system can support virtual private network (VPN) connections, allowing secure remote access to the host. It can provide authentication and encryption mechanisms to ensure the privacy and integrity of the communication.
- Host monitoring: The firewall system can monitor the activities and behavior of the host, including network connections, file access, and system processes. This helps in detecting any suspicious or unauthorized activities and provides additional layers of protection.
In conclusion, a host-based firewall system offers a range of features to ensure the security and protection of individual hosts. By implementing rule-based access control, audit and logging mechanisms, intrusion detection and prevention capabilities, and supporting VPN connections, it provides a comprehensive security solution for host-based environments.
Benefits of using a host-based firewall system
A host-based firewall system provides several benefits for enhancing the security of a host or device. Here are some of the key advantages:
- Granular control: A host-based firewall allows for fine-grained control over the incoming and outgoing network traffic on a specific host. This enables administrators to define specific rules and policies tailored to the unique security requirements of the host.
- Improved audit and compliance: By implementing a host-based firewall, organizations can easily monitor and log network activity on individual hosts. This enables better audit and compliance practices, as administrators can track and review any suspicious or unauthorized access attempts.
- Enhanced security: A host-based firewall acts as an additional layer of defense against unauthorized access and attacks. It can block malicious traffic, protect against intrusion attempts, and prevent unauthorized access to sensitive data and services.
- Control of services and ports: With a host-based firewall, administrators can control which services and ports are accessible from the network. This helps minimize the attack surface and reduces the risk of exploitation of vulnerable services.
- Flexible configuration: A host-based firewall allows for easy configuration and customization of security rules based on the specific needs of the host. This flexibility ensures that the firewall settings align with the host’s security requirements.
- VPN support: Host-based firewalls often include support for Virtual Private Networks (VPNs), enabling secure remote access to the host and ensuring encrypted communication between the host and external networks.
- Device management: Host-based firewalls can be centrally managed, providing administrators with a single interface to monitor and configure firewall settings for multiple hosts. This centralized management simplifies the administration and maintenance of firewall policies.
- Intrusion detection and prevention: Many host-based firewalls include intrusion detection and prevention capabilities, which can detect and block known attack patterns and prevent unauthorized activities from compromising the host’s security.
- Logging and monitoring: A host-based firewall typically generates logs and alerts for network events and activities. These logs can be invaluable for troubleshooting, investigating security incidents, and monitoring the overall security status of the host.
In conclusion, a host-based firewall system provides numerous benefits for enhancing the security of individual hosts or devices. It offers granular control, improved audit and compliance capabilities, enhanced security, control over services and ports, flexible configuration, VPN support, centralized device management, intrusion detection and prevention features, as well as logging and monitoring capabilities.
Enhanced security measures
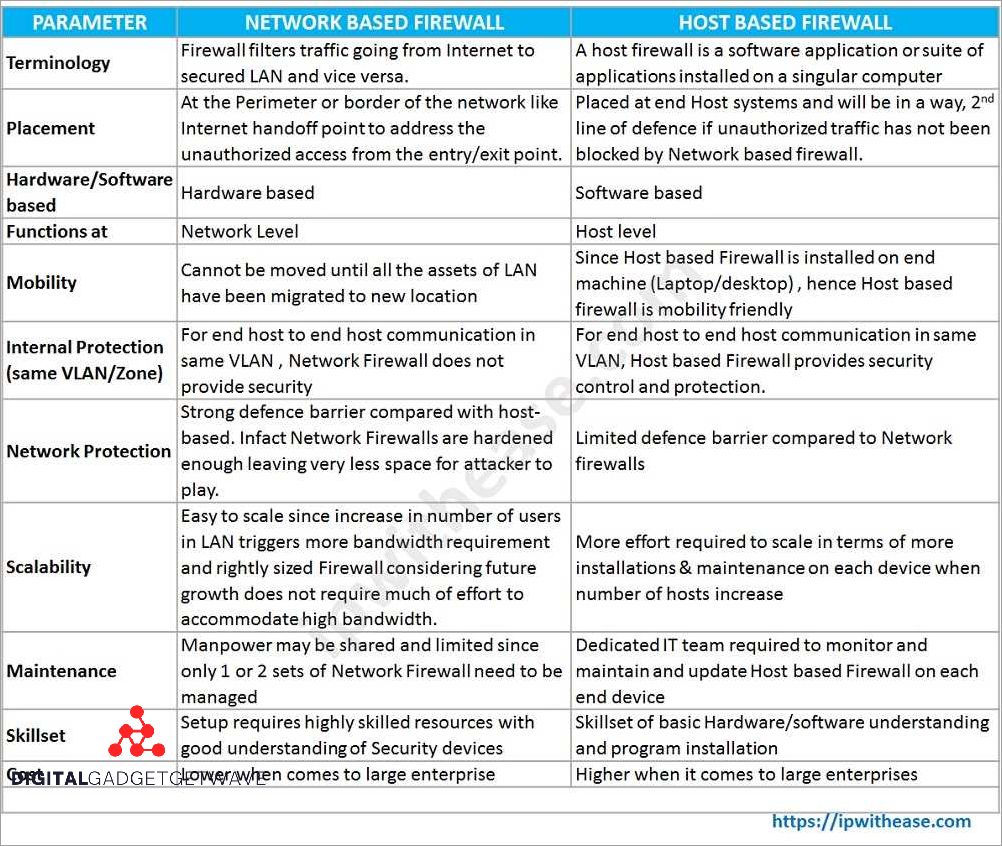
In order to enhance the security of the host-based firewall system, several measures can be taken. These measures include:
- Traffic filtering: The host-based firewall system can filter incoming and outgoing network traffic based on predefined rules and policies. This helps to prevent unauthorized access to the network and protects sensitive data.
- Service configuration: By configuring the firewall to allow only necessary services and ports, the host-based firewall system can reduce the attack surface and minimize the risk of intrusion.
- VPN access: Implementing a VPN (Virtual Private Network) can provide an additional layer of security by encrypting network traffic and allowing secure remote access to the host-based firewall system.
- Logging and monitoring: The host-based firewall system should be configured to log and monitor network traffic, firewall events, and intrusion attempts. This allows for timely detection and response to security incidents.
- Centralized management: A centralized management system can be used to configure, monitor, and update the host-based firewall system. This simplifies management and ensures consistent security policies across multiple devices.
By implementing these enhanced security measures, the host-based firewall system provides a robust protection for the host and the network it is connected to. It helps to prevent unauthorized access, detect and respond to intrusions, and ensure the overall security of the network environment.
Securing individual host systems
Securing individual host systems is a critical aspect of maintaining overall network security. Host-based firewalls play a vital role in providing protection for individual hosts by filtering and controlling the traffic that enters and exits the system. By configuring firewall rules, administrators can customize the level of access and establish a security base for the host.
One of the key components of securing host systems is conducting regular audits and monitoring activities. This helps in identifying any potential vulnerabilities or unauthorized access attempts, allowing for timely detection and mitigation. Host-based firewall systems offer logging and auditing capabilities, ensuring that administrators can track and analyze network traffic and system activity to detect any suspicious or malicious activities.
In addition to firewall protection, host systems should also have intrusion detection and prevention systems in place. These systems actively monitor network traffic and identify any potential signs of intrusion or unauthorized access. By implementing intrusion detection and prevention systems, administrators can quickly respond to and mitigate potential security breaches.
Another important aspect of securing host systems is setting up virtual private networks (VPNs). VPNs provide secure access to network resources by encrypting the data transmission between the host and the network. By utilizing VPNs, administrators can ensure that all data transmitted between the host and the network remains confidential and protected from unauthorized access.
Furthermore, access control policies should be established to regulate network access for individual host systems. This includes defining user roles and permissions, restricting access to specific services, and enforcing strong authentication mechanisms. By implementing access control policies, administrators can effectively manage network access and prevent unauthorized individuals from gaining access to sensitive resources.
Implementing a host-based firewall system
A host-based firewall system plays a crucial role in ensuring the security of a network by controlling and monitoring the access to and from a host. It enables organizations to enforce strict access policies, limit the traffic that enters or leaves a host, and provide real-time logging and monitoring of network activity.
Configuring a host-based firewall system involves defining access rules and policies that determine which network services and ports are allowed or blocked. These rules are based on the organization’s security requirements and can be customized to provide granular control over the network traffic.
One of the key features of a host-based firewall system is its ability to protect the host against unauthorized access and intrusion attempts. It acts as a barrier between the host and the outside world, preventing malicious actors from exploiting vulnerabilities in the host’s security. By implementing a host-based firewall system, organizations can significantly reduce the risk of unauthorized access and protect sensitive data.
In addition to access control and protection, a host-based firewall system also provides extensive logging and monitoring capabilities. It enables organizations to track and analyze network traffic, detect any suspicious activity, and take immediate action to mitigate potential security threats. The system logs all network events, including successful and failed connection attempts, traffic patterns, and security policy violations.
Furthermore, a host-based firewall system can integrate with other security tools and services, such as intrusion detection and prevention systems. This integration enhances the overall network security by allowing the firewall to automatically block any traffic that is identified as malicious or anomalous. It provides an additional layer of protection against advanced threats and ensures that the network is constantly monitored and protected.
Implementing a host-based firewall system also facilitates secure remote access through the use of Virtual Private Networks (VPNs). VPNs encrypt traffic between remote users and the network, ensuring that sensitive data transmitted over the internet remains secure. The host-based firewall system can enforce strict access controls for VPN connections, ensuring that only authorized users and devices can establish a secure connection to the network.
In conclusion, implementing a host-based firewall system is essential for effective network management and security. It provides access control, logging, traffic monitoring, and protection against unauthorized access and intrusion attempts. By enforcing security policies and integrating with other security tools, a host-based firewall system enhances the overall security posture of an organization and helps prevent potential security breaches.
Choosing the right firewall software
When it comes to selecting the right firewall software for your network, there are several key factors to consider. The first step is to determine your security policy and requirements. You need to have a clear understanding of the level of protection you need and the specific threats you want to safeguard against.
Next, consider the auditing and monitoring capabilities of the firewall software. It should provide detailed logs and reports on network traffic, intrusion attempts, and any policy violations. This will help you stay informed about potential security breaches and take appropriate actions.
The firewall software should also offer a flexible configuration that allows you to define and manage firewall rules easily. You should be able to control access to network resources, configure ports and services, and set up virtual private network (VPN) connections. The ability to adapt the firewall settings to your specific network environment is crucial for effective security.
Additionally, the firewall software should provide robust intrusion prevention capabilities. It should be able to detect and block unauthorized access attempts, as well as detect and prevent various types of attacks, such as DoS (Denial-of-Service) and DDoS (Distributed Denial-of-Service) attacks.
Another important aspect to consider is the management and ease of use of the firewall software. It should have a user-friendly interface that allows you to easily configure and monitor the firewall settings. Centralized management capabilities are also desirable, especially for large networks or multi-location deployments.
Lastly, ensure that the firewall software is regularly updated and supported by the vendor. This will ensure that you have access to the latest security patches and features, as well as prompt technical support in case of any issues or questions.
By considering these factors and evaluating different firewall software options, you can choose the right solution that provides the necessary protection and meets your specific network security requirements.
Configuring firewall rules and policies
Configuring firewall rules and policies is an essential aspect of managing a host-based firewall system. These rules and policies determine how the firewall handles incoming and outgoing network traffic and play a crucial role in securing the device and network.
One of the first steps in configuring firewall rules and policies is identifying the services and ports that need to be allowed or blocked. This can be done by conducting an audit of the network and analyzing the security requirements of the device. By understanding the network’s needs and potential vulnerabilities, appropriate rules can be established to protect against unauthorized access, intrusion, and potential threats.
Firewall logging and monitoring are important components of configuring rules and policies. By enabling logging, administrators can track and review firewall events, allowing them to identify any suspicious activities or potential security breaches. This information can be used to fine-tune the firewall configuration and enhance the overall security of the device and network.
Another important consideration when configuring firewall rules and policies is the support for virtual private networks (VPNs). VPNs provide a secure tunnel for remote access to the network, and the firewall must be properly configured to allow VPN traffic while maintaining the necessary security measures. This includes the proper configuration of encryption protocols, authentication methods, and access control policies.
The configuration of firewall rules and policies should be based on the principle of least privilege. This means that only necessary services, devices, and ports should be allowed, reducing the attack surface and minimizing potential vulnerabilities. The rules should be regularly reviewed and updated to match the evolving security requirements of the network.
To facilitate the management of firewall rules and policies, many firewall systems provide centralized management consoles. These consoles allow administrators to define and deploy firewall rules across multiple hosts, simplifying the configuration process and ensuring consistency in security settings.
In summary, configuring firewall rules and policies is an integral part of managing a host-based firewall system. By carefully designing and implementing these rules, administrators can effectively control network traffic, protect against potential threats, and ensure the overall security and stability of the network.
Best practices for managing a host-based firewall system
A host-based firewall is an essential security component for protecting your network from unauthorized access and potential threats. To ensure the effective management of your host-based firewall system, it is important to follow some best practices:
- Define a clear security policy: Develop a comprehensive security policy that outlines the rules and guidelines for managing the firewall. This policy should define the allowed and blocked traffic, as well as the access rights and restrictions.
- Regularly update and maintain firewall rules: Keep your firewall rules up to date by regularly reviewing and modifying them as necessary. Ensure that there are no unnecessary rules and remove any obsolete entries. Regular maintenance will help optimize the firewall’s performance and enhance security.
- Enable logging and monitoring: Enable logging and monitoring features on the firewall to track and analyze network traffic. This will help you identify any suspicious activities, detect potential intrusion attempts, and respond to security incidents effectively.
- Implement secure VPN access: Use a virtual private network (VPN) to provide secure remote access to your network. This will ensure that only authorized users can access your network resources, and their traffic is encrypted, protecting sensitive data from interception.
- Regularly update firewall software and firmware: Keep your firewall software and firmware up to date to ensure that you have the latest security patches and features. Regular updates are crucial for addressing vulnerabilities and protecting your network from potential threats.
- Implement intrusion detection and prevention: Use intrusion detection and prevention systems (IDPS) in conjunction with your firewall to enhance network security. IDPS can detect and block various types of attacks and provide additional layers of protection.
- Perform regular security audits: Conduct regular security audits to evaluate the effectiveness of your firewall configuration and rules. Identify any security gaps or weaknesses and take appropriate measures to address them.
- Limit access to management interfaces: Restrict access to the firewall’s management interfaces to authorized personnel only. Implement strong authentication mechanisms, like multi-factor authentication, to prevent unauthorized access and ensure the security of the firewall configuration.
By following these best practices, you can effectively manage your host-based firewall system and enhance the security of your network and connected devices. Remember to stay proactive in monitoring and updating your firewall to stay ahead of emerging threats and protect your network from potential vulnerabilities.
Regularly updating firewall software
Regularly updating firewall software is a crucial aspect of maintaining a secure network environment. Firewall software acts as a barrier between your host or device and potential threats from the network. Keeping your firewall software up to date ensures that it has the latest security patches and updates, allowing it to effectively protect your network.
Updating firewall software involves making changes to its configuration, which includes modifying rules and policies. By updating the firewall software, you can implement new rules that offer enhanced protection against emerging threats. It is important to conduct regular audits of your firewall configuration to ensure that all rules and policies are up to date and aligned with the security requirements of your network.
Frequent updates also enable firewall software to detect and prevent intrusion attempts. By monitoring network traffic, the firewall can identify suspicious activities and block unauthorized access attempts. Updating the firewall software helps it stay ahead of new threats and provides an additional layer of security to your network.
Another benefit of regularly updating firewall software is that it allows you to take advantage of new features and improvements. Firewall vendors often release updates that offer enhanced management capabilities, such as easier rule management, better logging and reporting, and improved VPN services. By updating the firewall software, you can ensure that you are benefiting from the latest advancements in network security.
In conclusion, regularly updating firewall software is essential for maintaining a secure network environment. It helps protect your devices and network from potential threats by keeping the firewall software up to date with the latest security patches and updates. Updating the firewall software also allows you to implement new rules and policies, detect and prevent intrusion attempts, and take advantage of new features and improvements. By prioritizing regular updates, you can enhance the overall security and protection of your network.
Monitoring and analyzing firewall logs
Monitoring and analyzing firewall logs is a critical aspect of firewall management. Firewall logs provide important insights into the overall security of a network and help identify potential threats and breaches.
Firewall logs capture information about various events, such as intrusion attempts, access requests, and VPN connections. By regularly reviewing these logs, network administrators can identify patterns and anomalies that may indicate unauthorized access or suspicious activity.
One important aspect of monitoring firewall logs is analyzing the logged events in relation to firewall rules and policies. By correlating the logged events with the configured firewall rules, administrators can ensure that the firewall is providing the intended level of protection and that the rules are properly configured.
Firewall logs also provide valuable information about network traffic. By examining the logged data, administrators can identify trends and patterns, such as unusual spikes in traffic or frequent connections to specific ports. This information can help in identifying potential network vulnerabilities and developing strategies for mitigating them.
In addition to monitoring firewall logs for security purposes, they can also be used for auditing and compliance purposes. Organizations often have specific security standards and regulatory requirements that need to be met. Firewall logs can be used to demonstrate compliance and provide evidence of adherence to security policies and procedures.
Overall, monitoring and analyzing firewall logs is essential for maintaining the security and integrity of a network. It enables network administrators to detect and respond to potential threats in a timely manner, and also provides valuable insights for improving the configuration and management of firewall devices and services.
FAQ about topic “Understanding the Basics of Host-based Firewall Systems”
What is a host-based firewall system?
A host-based firewall system is a security mechanism that is installed directly on a computer or host and is responsible for monitoring and controlling incoming and outgoing network traffic. It acts as a barrier between the host and the network, allowing only authorized traffic to pass through.
How does a host-based firewall system work?
A host-based firewall system works by inspecting the packets of data that are sent and received by a computer or host. It analyzes the source and destination of the packets, as well as the type of traffic, and determines whether to allow or block the packets based on a set of predetermined rules. These rules can be customized by the user to meet their specific security needs.
What are the benefits of using a host-based firewall system?
A host-based firewall system offers several benefits. Firstly, it provides an additional layer of security by blocking unauthorized network traffic. This helps prevent malicious attacks and can help keep sensitive data safe. Additionally, a host-based firewall system allows users to have more control over their network connections, as they can customize the rules and settings to meet their specific needs. It also provides visibility into network traffic, allowing users to monitor and analyze network activity.
Can a host-based firewall system protect against all types of cyber threats?
No, a host-based firewall system cannot protect against all types of cyber threats. While it is an important security measure, it is not a comprehensive solution. A host-based firewall system is primarily designed to protect against unauthorized network traffic and can help prevent certain types of attacks, such as network-based attacks. However, it cannot protect against other types of threats, such as malware that may be downloaded onto a computer through social engineering or phishing attacks. It is important to have multiple layers of security in place to ensure comprehensive protection against cyber threats.
How can I configure a host-based firewall system?
Configuring a host-based firewall system typically involves setting up rules and settings to determine which network traffic is allowed and which is blocked. This can be done through a graphical user interface provided by the firewall software, where users can specify source and destination IP addresses, ports, and protocols for incoming and outgoing traffic. Additionally, users can also define exceptions and exclusions for certain types of traffic. It is important to carefully configure the firewall to strike the right balance between security and usability.


