
Wardriving is the act of driving around in a car to detect and map wireless networks. This practice is motivated by the need for security and the growing concern about hacking and unauthorized access to personal and corporate networks. Wardriving allows individuals to scan for wireless networks and identify vulnerabilities in their security.
During a wardriving session, individuals drive around with specialized equipment, such as a laptop computer with wireless network capabilities and a GPS device. The laptop scans for wireless networks in the area, detecting access points and capturing information, such as network names (SSIDs), signal strength, and encryption types. The GPS device records the location of each detected network.
Wardriving can reveal the presence of insecure wireless networks, which can be easily hacked and exploited. It exposes the weaknesses in the security measures implemented by individuals and organizations, such as using weak or default passwords for their routers. By mapping the location of these vulnerable networks, wardrivers raise awareness about the importance of securing wireless networks and preventing unauthorized access.
Mapping wireless networks through wardriving helps individuals and organizations understand the distribution and coverage of wireless networks in different areas. It can also assist in visualizing the concentration of wireless networks, identifying potential sources of interference, and analyzing network traffic patterns. This information can be useful for planning and optimizing wireless network infrastructure and improving overall network performance.
Contents
- 1 What is Wardriving?
- 2 Understanding the practice
- 3 Legal and Ethical Considerations
- 4 Benefits and Risks
- 5 Protecting Your Network
- 6 FAQ about topic “Understanding Wardriving: Exploring the World of Wireless Network Search and Mapping”
- 7 What is wardriving?
- 8 Why do people engage in wardriving?
- 9 Is wardriving legal?
- 10 Can wardriving be used for malicious purposes?
- 11 Where can I find tools for wardriving?
What is Wardriving?
Wardriving is the practice of searching for and mapping wireless networks. It involves driving around a location with a device capable of detecting and scanning wireless networks, such as a laptop or smartphone. The term “wardriving” is derived from “war dialing,” which refers to the practice of dialing phone numbers in order to find open modems.
During a wardriving session, a person drives around in a car equipped with a wireless network detector and a GPS device. As the car moves, the detector scans for wireless networks and the GPS device records the coordinates of each detected network, creating a map of the wireless networks in the area.
Wardriving can be done for various reasons. Some people do it out of curiosity, while others may do it to identify weak points in wireless network security or as a way to gather information about the traffic on wireless networks. Unfortunately, wardriving can also be used for malicious purposes, such as hacking into unprotected Wi-Fi networks or attempting to gain unauthorized access to routers and stealing passwords.
By mapping out wireless networks, wardrivers can identify vulnerabilities in network security and raise awareness about the importance of securing wireless networks. It is crucial for individuals and businesses to protect their Wi-Fi networks with strong passwords and encryption methods to prevent unauthorized access and potential hacking.
Overall, wardriving serves as a reminder of the potential risks associated with wireless networks and highlights the need for improved network security measures to protect personal and sensitive data.
Understanding the practice
Wardriving is the practice of driving around in a vehicle equipped with wireless scanning tools to identify and map wireless networks. The goal of wardriving is not to hack into these networks or steal information, but rather to gather information on the location and characteristics of wireless access points.
Wireless networks, commonly known as Wi-Fi, rely on routers that transmit signals to allow devices to connect and access the internet. These routers are usually password protected to ensure only authorized users can connect. However, wardriving can help identify networks where the security measures are not properly set up, making them vulnerable to hacking attempts.
The process of wardriving involves driving around an area with a laptop or mobile device that has a wireless network card and GPS capabilities. This device scans for all wireless networks in the vicinity, including their network names (SSID) and signal strengths. The GPS allows the user to map the location of each network detected.
The collected data from wardriving can be used to identify potential vulnerabilities in wireless networks. For example, if a network has a weak password or no password at all, it is more susceptible to unauthorized access. By detecting these vulnerabilities, network administrators can take steps to improve the security of their networks and protect against potential hacking attempts.
It is important to note that wardriving itself is not illegal. However, using the collected data to gain unauthorized access to networks or engage in illegal activities is against the law. Wardriving is primarily used as a security measure to identify and address any weaknesses in wireless networks.
Definition and Origins
Wardriving, also known as wifi scanning, is the practice of driving around and scanning wireless networks using a device equipped with wifi capabilities. The main purpose of wardriving is to map out the location of wireless access points and identify any vulnerabilities that may exist within these networks. This information can then be used for various purposes, such as network security improvement or even hacking attempts.
Wardriving involves the use of a wifi-enabled device, such as a laptop, smartphone, or tablet, to detect and record wireless networks in the vicinity. The wardriver typically drives around in a car, equipped with a GPS receiver to accurately map the location of each detected network. The wardriving software scans for wifi signals, capturing information about the network, including its SSID (network name), signal strength, encryption type, and MAC address of the router.
While wardriving may be seen as a form of hacking, it is important to note that it is usually conducted with the intention of gathering data rather than gaining unauthorized access to networks. However, wardriving can be considered illegal if it is used to gain unauthorized access to networks or to conduct other malicious activities.
Wardriving has its origins in the early 2000s when the popularity of wireless networks started to rise. As more and more people began using wifi, it became crucial to identify potential vulnerabilities and secure these networks from unauthorized access. Wardriving emerged as a practice to help individuals and organizations understand the extent of their network’s vulnerability and take steps to address them.
Today, wardriving techniques have evolved, and there are even dedicated tools and software available that make the process more efficient. Network administrators and security professionals often use wardriving as a proactive measure to identify and mitigate potential security risks in wireless networks.
The Tools and Techniques Used
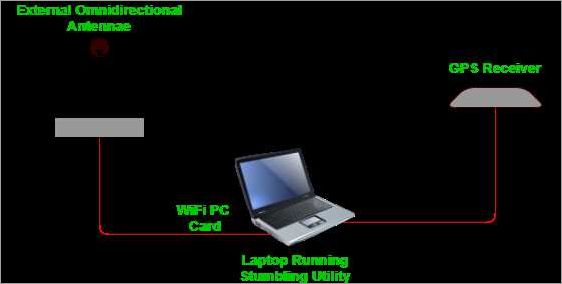
Wardriving is a practice that involves searching for and mapping wireless networks. It is commonly done using a variety of tools and techniques to detect and analyze wireless traffic.
One of the essential tools used in wardriving is a laptop or a computer equipped with a wireless network adapter. This device allows the wardriver to scan for available wireless networks in the surrounding area. Once detected, the wardriver can collect information about these networks, such as their SSIDs (Service Set Identifiers), signal strengths, and types of authentication and encryption used.
Another commonly used tool is a GPS receiver. By combining the GPS data with the information gathered about the wireless networks, wardrivers are able to create maps that show the location of these networks. These maps can be useful for various purposes, such as identifying the areas with the highest concentration of wireless networks or determining the coverage areas of specific networks.
In addition to the basic tools mentioned above, wardrivers may also utilize specialized software or hardware for more advanced purposes. For example, some wardrivers use hacking tools to exploit vulnerabilities in wireless networks, attempting to gain unauthorized access or intercept sensitive information. Such tools can include password-cracking software or devices capable of conducting more in-depth network analysis.
Overall, wardriving relies on a combination of scanning, mapping, and hacking techniques to explore and analyze wireless networks. While the practice can be performed using a car, hence the name wardriving, it is also possible to perform on foot or using other means of transportation. The ultimate goal is to gather information about wireless networks in a given area, with various intentions ranging from research and security testing to potentially malicious activities.
Legal and Ethical Considerations
When engaging in wardriving, it is important to understand and abide by legal and ethical considerations. While wardriving itself is not illegal, the actions one takes while driving and scanning for wireless networks can raise legal concerns. It is essential to be aware of the laws and regulations regarding wireless network access and hacking in the jurisdiction in which you are operating.
One of the key ethical considerations when wardriving is respecting the privacy and security of others. It is important to remember that connecting to someone else’s wireless network without permission is unauthorized access and can be considered hacking. Additionally, attempting to crack passwords or exploit vulnerabilities in wireless networks is also illegal and unethical.
While wardriving can be a useful tool for mapping wireless network locations and identifying potential security vulnerabilities, it should be done responsibly and with consent. It is important to obtain permission from the network owner before attempting to access or test their network security. This can be done by contacting the network owner directly or by using appropriate methods to anonymize the scan and protect the network owner’s privacy.
Furthermore, it is important to consider the potential impact of wardriving on network traffic and performance. Continuous scanning for wireless networks can create congestion and slow down network speeds for others. Therefore, it is crucial to drive responsibly and avoid excessive scanning in densely populated areas or during peak traffic times.
In summary, while wardriving can be a valuable practice for mapping and detecting wireless network security vulnerabilities, it is essential to approach it in a legal and ethical manner. Respecting privacy, obtaining consent, and avoiding excessive scanning are all important factors to consider when engaging in wardriving activities.
Laws and Regulations
When it comes to wardriving, there are laws and regulations that govern the practice to ensure that it is carried out ethically and legally. These regulations vary from country to country and even from state to state, so it is important to familiarize yourself with the laws in your specific location.
In many places, wardriving itself is not illegal, as it involves simply driving around to scan and map wireless networks. However, accessing these networks or attempting to hack into them without permission is a different matter entirely and is illegal in most jurisdictions. It is important to understand that wardriving should only be done for legitimate purposes, such as assessing network security vulnerabilities or conducting research.
Wardrivers must also be mindful of the traffic laws and regulations of the area they are driving in. It is crucial to prioritize safety at all times, as distracted driving poses a risk to both the wardriver and other road users. To ensure safe and legal wardriving, it is recommended to have a co-pilot operate the scanning equipment while the driver focuses on the road.
GPS technology plays a crucial role in wardriving, as it allows for accurate mapping of wireless network locations. However, it is important to be aware of any regulations regarding the use of GPS devices in the car. Some locations may have restrictions on the placement or use of GPS devices, so it is important to research and comply with these regulations to avoid legal issues.
Overall, while wardriving itself may not be illegal in many jurisdictions, it is crucial to adhere to local laws and regulations. This means refraining from attempting to access or hack into wireless networks without permission. By conducting wardriving ethically and responsibly, it can be a valuable tool for identifying and addressing security vulnerabilities in wireless networks.
Ethical Implications
Wardriving, a practice that involves searching for and mapping wireless networks, raises several ethical concerns. While it may seem harmless, wardriving can potentially provide unauthorized access to private networks, compromising the security and privacy of individuals and organizations.
Mapping networks and their locations through wardriving can be beneficial for researchers and network administrators. However, it can also be misused by hackers to identify vulnerable networks and exploit them for malicious purposes. This highlights the importance of securing wireless networks and regularly updating router firmware to patch any vulnerabilities.
Wardriving involves driving around with a device capable of scanning for and detecting wireless networks, usually equipped with a GPS. In some cases, this practice may inadvertently intercept network traffic, potentially exposing sensitive information, such as passwords or personal data, to unauthorized individuals.
Responsible wardriving practices should prioritize informing network owners about any identified security risks, so that they can take appropriate measures to protect their networks. It is also essential to raise awareness about the importance of securing Wi-Fi networks and regularly changing passwords.
In conclusion, wardriving can be both a beneficial and potentially harmful activity. While it can help identify security vulnerabilities, it is crucial to approach it ethically and responsibly. By maintaining the privacy and security of wireless networks, we can ensure a safer digital environment for all users.
Benefits and Risks
Benefits:
- Wardriving allows individuals to gather information about wireless networks in their vicinity. This can be useful for troubleshooting connectivity issues or finding open networks when in need of internet access.
- Scanning for Wi-Fi networks can help identify any vulnerabilities or security flaws in the networks, as well as any potential risks or threats.
- Mapping wireless networks can be beneficial for companies or individuals looking to analyze network coverage, signal strengths, or to plan the placement of routers or access points.
- Wardriving can also be used for monitoring and analyzing Wi-Fi traffic patterns, which can be useful for research or data analysis purposes.
- Using GPS technology, wardriving can detect the location of wireless networks and create maps that display the distribution of network access points.
Risks:
- One of the main risks of wardriving is the potential for hacking. If unauthorized access is gained to a wireless network, it can result in data breaches, identity theft, or other malicious activities.
- Wardriving can be seen as an invasion of privacy, as it involves collecting information from other people’s networks without their knowledge or consent.
- There is also the risk of legal repercussions, as accessing wireless networks without permission is often illegal in many jurisdictions.
- When wardriving, it is possible to come across networks that have weak or default passwords, making them vulnerable to exploitation.
- While driving, paying attention to mapping and scanning for networks can be distracting and pose a risk to the safety of the driver and others on the road.
Benefits of Wardriving
Wardriving, the practice of searching for and mapping wireless networks using a car, can provide several benefits. One of the main advantages is the ability to detect and map WiFi networks in a given area. By driving around and conducting WiFi scans, wardrivers can create a comprehensive map of all the access points in an area.
This mapping can be useful for various purposes. For example, wardriving can help identify areas with low WiFi coverage, allowing individuals or businesses to make informed decisions about network installations or expansions. The data collected from wardriving can also be used to optimize the placement of wireless routers and access points for maximum coverage and signal strength.
Another benefit of wardriving is the ability to identify security vulnerabilities in wireless networks. By scanning and analyzing the networks, wardrivers can detect weak or outdated security protocols, easily guessable passwords, or misconfigured routers. This information can be used by network administrators to improve the security of their networks and mitigate potential hacking risks.
Furthermore, wardriving can help monitor WiFi traffic in a given area. By analyzing the data collected during wardriving, it is possible to gain insights into the amount of network traffic, the types of devices connected to the networks, and the overall usage patterns. This information can be valuable for businesses looking to understand their customer base or for individuals monitoring their own network usage.
In summary, wardriving provides the opportunity to map and analyze wireless networks, detect security vulnerabilities, optimize network coverage, and monitor WiFi traffic. It is a valuable tool for individuals and organizations seeking to improve their WiFi infrastructure and strengthen their network security.
Risks and Potential Dangers
Wardriving can expose users to several risks and potential dangers due to the nature of searching for and mapping wireless networks. One major risk is the interception of network traffic. By driving around and scanning for WiFi networks, hackers can detect and intercept data transmitted over these networks, which may include sensitive information such as passwords or personal data.
Another potential danger is the possibility of gaining unauthorized access to wireless networks. Wardriving can provide hackers with valuable information about vulnerable access points, allowing them to exploit security weaknesses and gain unauthorized access to networks. Once inside a network, hackers can carry out various malicious activities, such as stealing data or launching further attacks.
Additionally, wardriving can pose risks to personal safety. Since the practice involves driving around to detect WiFi networks, distractions caused by scanning for networks or updating mapping software can divert the driver’s attention from the road. This may lead to accidents and endanger both the driver and other road users.
Moreover, there are legal considerations to be aware of when engaging in wardriving activities. In some jurisdictions, scanning and hacking into wireless networks without permission is illegal. Hackers could face legal consequences if caught, including fines and even imprisonment.
To mitigate these risks, it is important for individuals and organizations to prioritize network security. This includes regularly updating router firmware, using strong passwords, and implementing encryption protocols to protect network traffic. It is also crucial to educate users about the potential dangers of wardriving and promote safe practices, such as avoiding the use of public WiFi networks and regularly reviewing access logs to detect any unauthorized activity.
Protecting Your Network
Securing your wifi network is crucial in order to protect your data and maintain the integrity of your network. Wireless networks, also known as wifi networks, are vulnerable to hacking attempts, such as wardriving. Wardriving is the practice of driving around in a car to search for and map wifi access points and their locations.
One of the first steps to secure your network is to change the default password and username of your router. Many routers come with pre-set credentials, which are easy for hackers to guess. By changing these credentials to strong, unique ones, you can significantly reduce the risk of unauthorized access.
Regularly updating your router’s firmware is also important. Router manufacturers often release updates that patch known vulnerabilities, so keeping your router up to date will help protect against potential attacks.
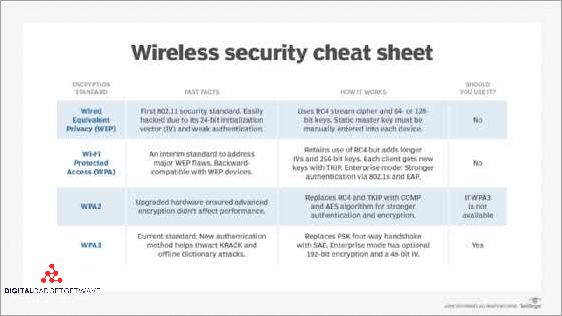
Another security measure is to enable network encryption. Using protocols like WPA2-PSK or WPA3 will secure your wireless network by encrypting the traffic between your devices and the router. This makes it difficult for hackers to intercept and decode any sensitive information.
Detecting and monitoring the devices connected to your network is another crucial step. Regularly scanning your network for unknown devices can help identify any potential threats. Most routers have features to display the connected devices, and you can also use network scanning tools to get more detailed information.
Additionally, disabling the broadcasting of your network’s SSID can add an extra layer of security. With the SSID hidden, it can be more difficult for potential hackers to detect and target your network.
Overall, taking proactive measures to secure your wireless network is essential in preventing unauthorized access and protecting your data. By following these steps and staying vigilant, you can minimize the risk of network breaches and ensure the safety of your network.
Secure Your Wireless Network
Securing your wireless network is crucial to protect your sensitive information and prevent unauthorized access. Here are some steps you can take to secure your wifi:
- Change the default username and password: The default login credentials for routers are widely known, so it’s important to change them to something unique and strong to prevent unauthorized access.
- Enable encryption: Use WPA2 or WPA3 encryption to secure your wifi traffic. This will prevent hackers from eavesdropping on your data and gaining access to your network.
- Disable SSID broadcasting: By hiding the name of your wifi network, you can make it less visible to potential attackers. They won’t be able to detect it easily when performing wardriving or scanning for available networks.
- Enable MAC address filtering: By configuring your router to only allow devices with specific MAC addresses to connect, you can add an extra layer of security.
- Regularly update router firmware: Keep your router’s firmware up to date to ensure that any known vulnerabilities are patched and your network is secure.
Remember that securing your wireless network is an ongoing process. Stay informed about new security threats and techniques, and regularly review and update your security measures to protect against potential hacking attempts.
Prevent Wardriving Attacks
Wardriving is the practice of searching for and mapping wireless networks, usually from a car, using a wireless scanner or Wi-Fi-enabled device such as a smartphone or laptop. These networks can include public Wi-Fi access points, as well as private and corporate networks.
Wardriving attacks can pose a serious security risk as they can potentially expose the vulnerabilities of wireless networks and their connected devices. To prevent such attacks, it is important to take necessary security measures.
1. Secure your wireless router: Change the default administrator username and password for your router, and enable encryption (such as WPA2) on your Wi-Fi network to protect your network traffic from being intercepted.
2. Disable broadcasting: Disable the Wi-Fi network’s SSID broadcasting feature, which prevents your network name from being visible to wardrivers. This makes it harder for them to detect and target your network.
3. Regularly scan for unauthorized access points: Use a wireless scanner or network management tool to periodically scan your environment for any unauthorized access points that may have been set up by wardrivers. You can then take appropriate action to secure your network.
4. Keep your devices updated: Regularly update the firmware and security patches for your wireless devices, including your router, to protect against known vulnerabilities and exploits.
5. Use strong passwords: Ensure that your Wi-Fi network password is strong and not easily guessable. Avoid using common passwords or easily identifiable information.
6. Utilize GPS coordinates: If possible, configure your router to only allow Wi-Fi connections from devices within a specific geographic location, using GPS coordinates. This helps restrict access to your network only to authorized devices.
7. Consider using guest networks: If you frequently have visitors or guests who need Wi-Fi access, consider setting up a separate guest network that is isolated from your main network. This helps protect your main network from potential vulnerabilities introduced by guest devices.
By taking these preventive measures, you can greatly enhance the security of your wireless network and reduce the risk of wardriving attacks.
FAQ about topic “Understanding Wardriving: Exploring the World of Wireless Network Search and Mapping”
What is wardriving?
Wardriving is the practice of searching for and mapping wireless networks using a vehicle or other mobile means. It involves driving around with a wireless device, typically a laptop or smartphone, equipped with a Wi-Fi scanner to detect and record the presence of wireless networks.
Why do people engage in wardriving?
There are several reasons why people engage in wardriving. Some do it for recreational purposes, enjoying the thrill of discovering new networks and mapping their locations. Others may do it out of curiosity or to learn more about wireless technology. However, it’s important to note that wardriving without permission is illegal and unethical.
Is wardriving legal?
Wardriving itself is not illegal, but using it to access or exploit unprotected wireless networks without permission is illegal in many jurisdictions. It’s always important to respect the privacy and security of others when engaging in any activity related to wardriving.
Can wardriving be used for malicious purposes?
Yes, wardriving can be used for malicious purposes. By identifying vulnerable or unprotected wireless networks, hackers can gain unauthorized access to sensitive information, inject malware, or launch attacks on the network or its users. It’s essential to secure wireless networks to protect against such threats.
Where can I find tools for wardriving?
There are several tools available for wardriving, both free and paid. Some popular ones include Kismet, NetStumbler, and WiGLE. These tools help detect and map wireless networks, providing information about network names, signal strength, encryption status, and more. It’s important to use these tools responsibly and in compliance with the law.


