A configuration item (CI) is a key component of any system or process that needs to be managed and controlled. It can be anything from a hardware or software item to a document, record, or asset. CIs are typically stored in a configuration management database (CMDB) and are used to track changes, monitor performance, and ensure the stability and reliability of a system or service.
The purpose of a configuration item is to provide an inventory of all the components that make up a system or process. This includes not only the physical elements, such as hardware devices and network infrastructure, but also the software applications, configurations, and settings. By having a comprehensive list of CIs, organizations can better understand their IT environment and make informed decisions about deployment, change management, and optimization.
Managing configuration items is a critical part of IT service management and is often done through automation and process controls. This includes creating a baseline configuration that represents the standard or desired state for a system or service. When changes are made, the CI is updated to reflect the new configuration, allowing for better control and accountability.
Effective configuration item management involves continuous monitoring and analysis of the CIs to ensure they are functioning as expected and meeting the needs of the organization. This includes tracking performance metrics, identifying potential vulnerabilities or risks, and making necessary adjustments to maintain the stability and reliability of the system or service. By keeping a record of all CIs and their associated attributes, organizations can more easily determine the impact of a change or issue and quickly resolve any problems that arise.
In conclusion, a configuration item is a fundamental component of any system or process. It is essential for organizations to have a comprehensive understanding of their CIs, as they play a crucial role in the management and optimization of systems and services. By effectively managing and controlling CIs, organizations can ensure the stability, reliability, and performance of their IT environment.
Contents
- 1 Understanding Configuration Items
- 2 Definition and Purpose
- 3 Types of Configuration Items
- 4 Configuration Item Lifecycle
- 5 Planning and Identification
- 6 Change Management
- 7 Verification and Audit
- 8 Configuration Item Management
- 9 Configuration Item Repository
- 10 Configuration Item Baseline
- 11 Configuration Item Traceability
- 12 Best Practices for Configuration Item Management
- 13 Regular Reviews and Updates
- 14 Documentation and Documentation Management
- 15 Collaboration and Communication
- 16 FAQ about topic “What is a configuration item: A comprehensive guide”
- 17 What is a configuration item?
- 18 Why are configuration items important in IT management?
- 19 How should configuration items be documented?
- 20 What are the challenges of managing configuration items?
- 21 How can organizations ensure the integrity of configuration items?
Understanding Configuration Items
In the field of IT service management, a configuration item (CI) is a fundamental element that is essential for the successful operation of a system or service. It can be anything from a hardware or software asset to a document or inventory record. CIs are used to track and manage the components that make up a system or service.
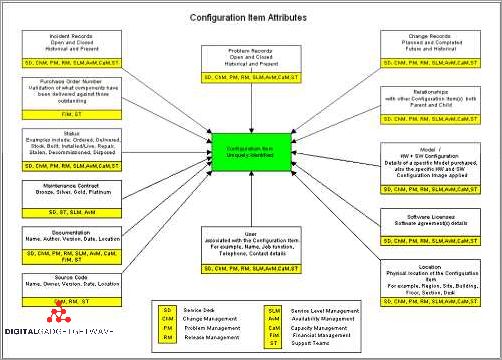
Each configuration item has a unique identifier and is defined by a set of attributes that describe its characteristics and properties. These attributes can include information such as the item’s name, type, version, location, and dependencies on other CIs. The CI record serves as a comprehensive source of information about the item and its relationships within the system.
Configuration items play a crucial role in various IT processes, such as service asset and configuration management, change management, and release and deployment management. They enable organizations to effectively plan, track, and manage the lifecycle of their IT assets and infrastructure.
For example, in a software development environment, a configuration item may refer to a specific version of a software application. This CI would encompass the source code, compiled binaries, configuration files, and associated documentation. By effectively managing and monitoring these CIs, organizations can ensure the successful deployment and operation of their software systems.
Configuration items are stored in a central configuration management database (CMDB) or repository, which serves as a single source of truth for all CIs within an organization’s IT environment. The CMDB enables efficient tracking, retrieval, and reporting of CI information, allowing organizations to understand the impact of changes, manage risks, and make informed decisions.
In summary, configuration items are essential components within a system or service that are used to track, manage, and understand the various elements that make up an organization’s IT infrastructure. By effectively managing these CIs, organizations can ensure the stability, reliability, and efficiency of their IT operations.
Definition and Purpose
A configuration item (CI) is a record in a database that represents a component of an IT system. It can be an asset, a document, a hardware device, or a software component. The main purpose of a configuration item is to track and manage the changes and relationships within the IT infrastructure.
A configuration item is a key element of configuration management, which is a process of identifying, controlling, and tracking the configuration of a system. It helps organizations maintain a baseline of their IT assets and ensure that changes are properly documented and authorized.
Configuration items are typically managed in a configuration management database (CMDB), which is a centralized database that stores information about the configuration items and their relationships. The CMDB provides a single source of truth for the IT infrastructure and enables efficient management, monitoring, and deployment of the system.
The main purpose of configuration items is to enable effective change management. By accurately documenting and tracking the configuration items, organizations can easily identify the impact of proposed changes and evaluate the risks associated with those changes. This helps in making informed decisions and ensures that the changes are implemented smoothly without causing disruptions to the system.
Configuration items also play a crucial role in asset management. By maintaining an inventory of the configuration items, organizations can keep track of their hardware and software assets, monitor their usage, and plan for future upgrades and replacements. This helps in optimizing the IT infrastructure and reducing unnecessary expenses.
In summary, a configuration item is a key component of configuration management. It represents a record of an IT asset, document, or software component and helps in tracking and managing the changes and relationships within the system. By utilizing configuration items and a CMDB, organizations can effectively manage their IT infrastructure, automate processes, and ensure smooth deployment and monitoring of the system.
What is a Configuration Item?
A Configuration Item (CI) is an essential component in the automation, process, and documentation of an organization’s hardware, software, network, and system assets. It represents a unique and identifiable entity that requires monitoring and management throughout its lifecycle.
A CI can refer to various entities, such as a piece of hardware, a software application, a network device, a database, or even a service. Each CI has its own specific attributes and characteristics that define its configuration, including its version, baselines, records, and relationships with other CIs.
The management of CIs involves tracking changes and deployments, ensuring that they are properly documented, and maintaining their integrity within the system. This includes managing their lifecycle, including creation, modification, and retirement.
With effective configuration item management, organizations can have a clear understanding of their assets and their relationships, enabling better decision-making, troubleshooting, and problem resolution. It helps in ensuring that the organization’s services and systems are functioning optimally and are aligned with the desired configuration.
In summary, a Configuration Item is a fundamental component in the management of an organization’s assets and services. It encompasses various entities and involves the monitoring, documentation, and control of their configuration. Effective CI management is crucial for maintaining a stable and efficient environment.
Importance of Configuration Items
Configuration items (CIs) are key elements in any system or network. They play a vital role in the monitoring, automation, and management of the system’s resources. CIs can be software, hardware, or even documentation that are required to support the system’s operations.
One of the main reasons CIs are of great importance is that they act as the baseline for the system. They provide a record of the current state and configuration of each item in the system. This baseline serves as a reference point for any changes or updates that may occur in the future.
CIs also play a crucial role in asset management and deployment processes. By having a clear definition and inventory of all the CIs in a system, it becomes easier to track and manage resources. This, in turn, helps in optimizing the deployment of resources and ensures that they are utilized efficiently.
Furthermore, having a well-maintained database of CIs allows for effective change management. Any changes made to the system or its components can be tracked and recorded, making it easier to identify potential issues or conflicts. This helps in reducing downtime and ensuring a smooth transition during system upgrades or updates.
Another significant importance of CIs is that they facilitate effective service management. By having a comprehensive inventory of all CIs in a system, it becomes easier to provide accurate and timely support to users. This can include troubleshooting, resolving issues, or even providing upgrades or patches to the system.
In conclusion, configuration items are of great importance in any system or network. They provide the necessary documentation, tracking, and control required for effective management. By maintaining a well-organized and up-to-date database of CIs, organizations can ensure the smooth operation and optimization of their systems.
Types of Configuration Items
When it comes to configuration management, there are various types of configuration items that need to be considered. These configuration items can be classified into different categories based on their nature and purpose. Here are some of the common types of configuration items:
1. System configuration items: These include the configuration settings and parameters of a software or hardware system. They define how the system should behave and can be used to set up and configure various system components.
2. Document configuration items: These are the configuration items that relate to any documents or files that are part of a configuration management system. They can include design documents, user manuals, specifications, and other relevant documentation.
3. Network configuration items: These configuration items are related to the configuration and management of network devices and infrastructure. They can include routers, switches, firewalls, IP addresses, and other network-related settings.
4. Asset configuration items: These configuration items are related to the management of physical assets and resources. They can include hardware items such as servers, computers, storage devices, as well as non-hardware assets like software licenses or intellectual property.
5. Service configuration items: These configuration items are related to the configuration and management of services. They can include service-level agreements, performance metrics, service dependencies, and other service-related settings.
6. Automation configuration items: These configuration items are related to the automation of processes and tasks. They can include scripts, workflows, job schedules, and other automation-related settings.
7. Record configuration items: These configuration items are related to the management of records and data. They can include databases, data schemas, data dictionaries, and other record-related settings.
8. Change configuration items: These configuration items are related to the management of changes in a system or process. They can include change requests, change logs, change approvals, and other change-related settings.
9. Baseline configuration items: These configuration items are used as a reference point to compare the current state of a system or process. They can include baseline versions of software, hardware configurations, or process documentation.
10. Monitoring configuration items: These configuration items are related to the monitoring and tracking of system performance and health. They can include monitoring tools, alert thresholds, performance metrics, and other monitoring-related settings.
11. Deployment configuration items: These configuration items are related to the deployment and installation of software or hardware components. They can include deployment scripts, installation guides, and other deployment-related settings.
12. Inventory configuration items: These configuration items are related to the management and tracking of inventory. They can include stock records, inventory levels, reorder points, and other inventory-related settings.
13. Management configuration items: These configuration items are related to the management and governance of the overall configuration management process. They can include configuration management plans, policies, and other management-related settings.
Overall, the types of configuration items will vary depending on the specific needs and requirements of the organization or system being managed. It is important to identify and define these configuration items to ensure effective configuration management.
Hardware Configuration Items
In the context of configuration management, hardware configuration items (CIs) refer to the physical components and devices that make up a system or network. These CIs are essential for inventories, automation, change management, and monitoring processes.
Hardware CIs include assets such as servers, routers, switches, printers, and other network devices. Each hardware item is a unique configuration item with its own set of specifications, functionalities, and dependencies.
The configuration management process for hardware CIs involves documenting the details of each item, establishing a baseline, and tracking any changes or updates made to the hardware throughout its lifecycle. This documentation is typically maintained in a configuration management database (CMDB).
Hardware CIs play a crucial role in the management and deployment of software and services within a system or network. They provide the necessary infrastructure and resources for running various applications, storing and processing data, and facilitating network connectivity.
Monitoring hardware CIs is essential for ensuring their proper functioning and identifying any issues or faults. This can be done through continuous monitoring tools that track performance metrics, hardware health, and network connectivity.
Effective management of hardware CIs involves maintaining accurate and up-to-date documentation, including the specifications, location, and dependencies of each item. This documentation enables IT teams to plan and execute hardware-related changes, upgrades, or troubleshooting activities efficiently.
In summary, hardware configuration items are the physical components and devices that form the foundation of a system or network. Proper management of these items is essential for effective system deployment, monitoring, and change management processes.
Software Configuration Items
A software configuration item (SCI) is a defined software component that is identified and managed in the configuration management process. SCIs are the building blocks of a software system and can include items such as source code, executable files, configuration files, documentation, and other related artifacts.
Automation plays a crucial role in managing software configuration items. Automation helps in streamlining the process of identifying, tracking, and managing SCIs. It allows for the automatic detection of changes in the software system, which aids in efficiently managing and updating the configuration items.
Hardware components, such as servers, routers, and switches, can also be considered as software configuration items. These hardware components often require specific software configurations to function properly and must be managed as part of the overall configuration management process.
The change management process is closely tied to software configuration items. Any changes made to the software components need to be carefully planned, documented, and tracked to ensure that the integrity of the system is maintained. Change requests should be reviewed, approved, and implemented in a controlled manner to prevent any unintended consequences.
Monitoring and managing software configuration items is essential for keeping the system in a working state. Regular audits and checks ensure that the software components are up to date, properly configured, and meet the required standards. Any discrepancies or deviations from the baseline configuration should be promptly identified and addressed.
Network configuration items are critical for the proper functioning of network systems. Configuration items related to network infrastructure, such as routers, switches, and firewalls, need to be properly managed to ensure the smooth operation of the network.
Asset management and inventory control are important aspects of software configuration management. An accurate record of all software configuration items, including their versions, dependencies, and locations, helps in efficient deployment, troubleshooting, and maintenance of the system.
The process of deploying software configuration items involves installing, configuring, and testing the components in a specific environment. The deployment process should be well-documented and repeatable to ensure consistency and minimize errors.
Software configuration items related to databases are critical for managing and storing data. Configuration items such as database schemas, tables, indexes, and stored procedures need to be properly managed and controlled to ensure data integrity and security.
Documentation plays a vital role in managing software configuration items. Detailed and up-to-date documentation helps in understanding the purpose, functionality, and dependencies of each configuration item. It aids in troubleshooting, maintenance, and future enhancements of the software system.
Service configuration items are specific to the configuration and management of software services. These items include service configurations, service-level agreements, and monitoring parameters. Proper management of service configuration items ensures the availability and performance of the software services.
System configuration items encompass the overall configuration and setup of a software system. It includes the combination of hardware, software, network, and other components that form the system. Managing system configuration items ensures the stability, reliability, and performance of the software system.
In conclusion, software configuration items are crucial components of a software system that need to be carefully identified, managed, and controlled. Proper configuration management processes and tools help in efficiently managing software configuration items, ensuring the integrity and stability of the system.
Documentation Configuration Items
The system documentation configuration item is a key component of configuration management. It provides a comprehensive definition of the system, including its architecture, design, and operation. This document is crucial for understanding the system and ensuring that any changes are properly recorded and managed.
Change documentation configuration items are used to track and document changes to a system or process. These documents record the details of the change, including the reason for the change, the impact on the system, and any necessary actions or updates that need to be made. This information is important for maintaining an accurate inventory of changes and ensuring that the system remains up to date.
Network documentation configuration items are used to document the network infrastructure of an organization. These documents provide a detailed record of the network’s layout, including its hardware, software, and connections. They are essential for troubleshooting network issues and planning for future network changes or upgrades.
Baseline documentation configuration items serve as a reference point for the configuration of a system or process. They capture a snapshot of the system or process at a specific point in time, including its configuration, settings, and performance metrics. Baseline documents are useful for comparison, troubleshooting, and ensuring that the system remains consistent over time.
Asset documentation configuration items are used to document the various assets of an organization, such as hardware, software, and devices. These documents provide a comprehensive record of each asset, including its specifications, location, and maintenance history. Asset documentation is crucial for asset management, deployment, monitoring, and maintenance.
Service documentation configuration items are used to document the various services provided by an organization. These documents include information about the service, such as its purpose, scope, and requirements. Service documentation is crucial for managing and providing high-quality services to customers.
Database documentation configuration items are used to document the structure and contents of a database. These documents provide a detailed record of the database schema, tables, relationships, and data. Database documentation is essential for understanding and managing the database effectively.
Configuration management documentation configuration items are used to document the processes and procedures for configuration management. These documents outline the steps and guidelines for managing configuration items, including their creation, modification, and control. They are essential for ensuring consistency, accuracy, and efficiency in the configuration management process.
Configuration Item Lifecycle
A configuration item (CI) refers to any hardware, software, network, or service component that is part of a larger configuration. The lifecycle of a configuration item includes different stages, from its initial deployment to its eventual retirement or disposal. The lifecycle of a configuration item involves several key steps, including definition, deployment, monitoring, change management, and retirement or disposal.
Definition: The first stage in the configuration item lifecycle is the definition. This involves identifying and documenting the configuration items that make up a system or service. This includes creating a record for each item, providing a detailed description, and categorizing it according to its type (e.g., hardware, software, database).
Deployment: After the configuration items are defined, they are deployed in the system or service. This involves physically installing the hardware components, installing the software, and configuring the network. Each configuration item is recorded and tracked in the configuration management database (CMDB) or inventory.
Monitoring: Once the configuration items are deployed, they need to be monitored to ensure their proper functioning and performance. This involves regular checks and measurements to identify any deviations or issues. Monitoring can be done manually or through automation tools, and the results are recorded for further analysis and problem resolution.
Change management: Throughout the lifecycle of a configuration item, changes may be required to address issues, improve performance, or upgrade the system or service. Change management involves documenting and managing these changes to ensure they are properly planned, tested, and implemented. This helps maintain the integrity and stability of the configuration items and the overall system or service.
Retirement or disposal: At the end of its lifecycle, a configuration item may be retired or disposed of. This could be due to hardware becoming obsolete, software reaching its end-of-life, or a change in business requirements. The retirement or disposal process involves removing the configuration item from the system, updating the inventory or CMDB, and properly disposing of any physical assets.
In conclusion, the lifecycle of a configuration item involves several stages, including definition, deployment, monitoring, change management, and retirement or disposal. Proper management of the configuration item lifecycle is crucial for maintaining a reliable and efficient system or service.
Planning and Identification
In the context of configuration management, planning and identification are key steps in ensuring the effective management of configuration items (CIs). Planning involves defining the scope of the configuration management process and establishing the necessary policies and procedures for managing CIs. This includes determining the level of automation and tools needed to support the process.
Identification is the process of uniquely identifying and documenting CIs. This involves assigning a unique identifier to each CI, such as a serial number or a name, to facilitate easy tracking and change management. The identification process should also define the attributes and characteristics of each CI, such as its type, version, location, and owner.
Software CIs can include applications, libraries, or modules, while hardware CIs can include servers, routers, or other network devices. Each CI should be recorded in a configuration management system or database, which serves as the central repository for all configuration-related information.
Planning and identification also involve establishing baselines for CIs. A baseline is a predefined configuration state that serves as a reference point for comparison and change control. It captures the specific versions and configurations of CIs at a certain point in time and is used to ensure consistency and stability throughout the deployment and change management processes.
Effective planning and identification of CIs are essential for efficient configuration management. They provide a solid foundation for other configuration management activities, such as change management, monitoring, and inventory management of CI.
In summary, planning and identification are crucial steps in the configuration management process. By defining the scope and establishing the necessary policies and procedures, organizations can effectively manage CIs. The identification process ensures each CI is uniquely identified and documented, and baselines provide a reference point for change control. All of these activities contribute to the successful management of configuration items within an organization.
Defining Configuration Item Requirements
In the context of configuration management, defining the requirements of a configuration item is crucial for effective asset management and deployment. A configuration item can refer to any element that needs to be managed as part of a system or service. This can include hardware components, software applications, databases, documents, or any other record or item that contributes to the functioning of a system.
The first step in defining configuration item requirements is to establish a clear and comprehensive definition of what the item entails. This includes specifying the purpose, functionality, and any dependencies or relationships it may have with other items or processes within the system or service. This definition provides a baseline for understanding how the item should be configured, monitored, and managed.
Configuration item requirements also involve identifying the necessary attributes and properties that need to be documented and tracked. These attributes can include the item’s unique identifier, version, state, owner, location, and any relevant metadata. Additionally, configuration item requirements may involve defining appropriate change management processes to ensure that any modifications or updates to the item are properly tracked and approved.
Furthermore, configuration item requirements may include specifying the necessary monitoring and automation mechanisms for the item. This can involve establishing monitoring parameters and thresholds, setting up alerts and notifications for any deviations or critical events, and implementing automated processes for configuration item deployment, testing, and validation.
Finally, configuration item requirements should consider the item’s role in the overall network or system architecture. This includes identifying any interdependencies or relationships it may have with other items, processes, or services. By understanding how the item fits into the larger ecosystem, it is possible to establish effective configuration management practices that ensure the smooth operation and performance of the system or service as a whole.
In summary, defining configuration item requirements is an essential step in effective configuration management. By clearly defining the item’s purpose, attributes, relationships, and monitoring and management processes, it becomes possible to ensure the integrity, stability, and performance of a system or service.
Establishing Configuration Item Identification
Configuration Item (CI) identification is a critical aspect in the management of IT systems and services. It involves the definition and establishment of a comprehensive record of all the CIs in an organization’s infrastructure. By accurately identifying and documenting these items, organizations can effectively control and automate their IT environment.
An efficient way to establish CI identification is through the use of a robust configuration management database (CMDB). The CMDB acts as a central repository that stores information about every CI, including its attributes, relationships, and dependencies. This allows IT professionals to easily track, monitor, and manage all the CIs in their environment.
When it comes to identifying CIs, they can encompass a wide range of assets, including hardware, software, network components, and documentation. The identification process involves assigning unique identifiers, such as serial numbers or asset tags, to each CI. These identifiers are then recorded in the CMDB, providing a reliable reference for system administration, change management, and service deployment.
Configuration items are generally categorized into different types or classes based on their characteristics and roles within the IT environment. This helps in organizing and managing the CIs effectively. Some common types of CIs include applications, servers, databases, network devices, and infrastructure components.
Establishing CI identification is a crucial step in maintaining configuration baselines. A baseline represents the documented configuration of a CI at a specific point in time. It serves as a reference point for future changes and helps in identifying deviations and managing the integrity and consistency of the IT environment.
Continuous monitoring and updating of the CMDB and CI inventory is essential to ensure accurate identification and management of CIs. Regular audits and reviews help in detecting and resolving any discrepancies or inconsistencies, thus enhancing the overall efficiency and effectiveness of the IT system or service.
Change Management
Change management is a crucial component of any configuration management system. It is the process of controlling and coordinating changes to the configuration items in an organization’s inventory. This includes any changes to hardware, software, network, and database configurations, as well as changes to documentation and service definitions.
A change management system keeps track of every change made to a configuration item, creating a record of the change for future reference. This allows for accurate monitoring and auditing of the system, ensuring that all changes are documented and authorized.
One of the main goals of change management is to minimize the impact of changes on the operational stability of an organization. This involves carefully planning and scheduling changes, and assessing the potential risks and consequences. Changes are typically implemented in a controlled and organized manner, with proper testing and validation before deployment.
Automation plays a key role in change management, as it helps streamline the change process and reduce human error. Automated tools and software can be used to automatically capture and document changes, enforce change policies, and provide real-time monitoring and reporting.
Change management also relies on the concept of baselines, which are reference points that represent a known and stable state of the system. Baselines serve as a benchmark for comparing and evaluating changes, helping to ensure that only authorized and approved changes are implemented.
In conclusion, change management is an essential part of configuration management, allowing organizations to effectively and efficiently handle changes to their configuration items. By implementing a robust change management process, organizations can maintain the integrity and stability of their systems while adapting to the evolving needs of their business.
Managing Configuration Item Changes
Managing configuration item changes is a crucial aspect of the configuration management process. Each configuration item, whether it is a piece of hardware, software, or a network component, has a defined configuration baseline that should be maintained.
Configuration item changes can occur due to various reasons, such as upgrades, patches, or bug fixes. It is important to document all changes made to configuration items to keep track of the modifications and ensure that the configuration items are in line with the desired state.
Change management plays a significant role in managing configuration item changes. It involves a systematic process of requesting, reviewing, approving, and implementing changes. This process helps in maintaining the integrity of the configuration items and minimizing risks associated with changes.
Automation tools and software can greatly assist in managing configuration item changes. These tools can track the changes made to configuration items, provide real-time inventory and asset management, and streamline the change management process.
Monitoring and auditing configuration item changes is also a vital aspect of their management. Regular monitoring helps ensure that configuration items are functioning as expected and are in compliance with their predefined baseline. Auditing provides an additional layer of validation and helps identify any unauthorized or unexpected changes.
A configuration item change management database can be used to store and manage records of all changes made to configuration items. This database serves as a centralized repository for tracking and documenting changes, providing a historical record of configuration item modifications.
In conclusion, managing configuration item changes is a critical part of the configuration management process. It involves defining baselines, implementing a change management process, utilizing automation tools, monitoring changes, and maintaining a comprehensive change record. Following these practices ensures that configuration items are kept up to date and aligned with organizational requirements.
Evaluating Impact of Changes on Configuration Items
When considering changes to configuration items, it is crucial to evaluate their impact on the overall system. Configuration items can include various components such as hardware, documents, databases, baselines, networks, assets, and more. Each of these items plays a significant role in the definition, record, and management of the configuration.
During the change management process, it is necessary to assess how modifications to specific configuration items will affect the entire system. This evaluation involves analyzing the relationship between different configuration items, understanding their dependencies, and predicting the potential consequences of any alterations. It is important to have an accurate inventory of all configuration items to properly evaluate their impact.
Automation tools and monitoring systems can assist in evaluating the impact of changes on configuration items. These tools can provide insights into the interconnections between hardware, software, and processes. By analyzing the relationship between different items and their associated workflows, it becomes easier to assess the potential effects of a change.
Furthermore, conducting thorough testing and simulations can help in evaluating the impact of changes on configuration items. By creating test environments that closely resemble the production system, it is possible to observe the behavior of configuration items under different conditions. This allows for a more accurate assessment of the potential impact of a change before its actual deployment.
In summary, evaluating the impact of changes on configuration items requires a comprehensive understanding of the relationships between different components. It involves analyzing dependencies, predicting consequences, and utilizing automation tools and monitoring systems. Thorough testing and simulations can also aid in accurately assessing the potential impact. By considering these factors, organizations can make informed decisions regarding changes to their configuration items.
Implementing Approved Changes
Implementing approved changes is a crucial step in the configuration management process. It involves the actual deployment of changes to the relevant system or network. This process ensures that all approved changes are accurately implemented and recorded.
Before implementing changes, it is essential to have a comprehensive inventory of assets and software within the system. This inventory helps in identifying the affected items and ensuring that the changes are applied to the correct components.
Effective implementation of approved changes requires careful monitoring and documentation. A robust change management system should have mechanisms in place to track the progress of each change and record any issues or deviations from the original plan.
Automation plays a significant role in the implementation process, as it helps streamline and expedite the deployment of changes. Automation tools can be used to automate repetitive tasks, such as software updates or hardware configuration changes, reducing the risk of human error and improving efficiency.
Implementing approved changes also involves establishing baselines to ensure consistency and reliability. Baselines act as reference points for future changes and help maintain a stable and predictable system environment.
It is crucial to test the changes thoroughly before deploying them into a live environment. This testing phase helps identify any potential issues or conflicts that may arise due to the implemented changes. Testing can involve functional testing, integration testing, and performance testing to ensure that the changes do not have any adverse effects on the system or network.
Throughout the implementation process, it is important to follow defined processes and procedures. This includes adhering to change management policies, ensuring proper documentation of all changes made, and recording the details of the implementation process.
In conclusion, implementing approved changes involves careful management and control of the change process. This includes asset inventory, software monitoring, deployment, and documentation. Automation and baselining play essential roles in maintaining efficiency and stability, while thorough testing ensures the changes do not negatively impact the system or network.
Verification and Audit
The verification and audit process plays a critical role in the management of configuration items (CIs) within an organization. It involves ensuring that all hardware, software, and network components are accurately documented and recorded.
Verification and audit processes include regular checks to ensure that the configuration items are aligned with the defined baseline. This involves comparing the current state of the CIs with their documented configurations and identifying any inconsistencies or deviations.
Automation tools and software are often used to facilitate the verification and audit process. These tools can scan the organization’s database and compare it with the actual inventory and deployment records, providing a comprehensive overview of the current state of the CIs.
During the verification and audit process, any changes to the CIs must be properly documented. This includes capturing the details of the change, recording it in the configuration management database, and updating the relevant documentation and records.
The verification and audit process also involves monitoring the performance and availability of the CIs. This can be done through various monitoring tools and processes, which can alert the IT team to any abnormalities or issues that may impact the service delivery.
Overall, the verification and audit process is crucial in maintaining an accurate and up-to-date record of all configuration items within an organization. It ensures that the CIs are aligned with the defined baseline, and any changes are properly documented. This provides the foundation for effective configuration management and supports the overall service delivery process.
Conducting Configuration Item Verification
Configuration Item Verification is a crucial process in configuration management that ensures the accuracy and completeness of the configuration items (CIs) in a database. It involves conducting regular checks and audits to verify the configuration items against their defined baselines and the documented records. The purpose of this process is to maintain the integrity and reliability of the configuration management database (CMDB).
To conduct configuration item verification, an organization needs to establish a systematic approach. This involves developing a detailed plan that outlines the steps and criteria for verification. The plan should include the identification of the configuration items to be verified, the verification methods, and the frequency of verification.
During the verification process, each configuration item is examined to ensure that it aligns with the defined baseline and the documented records. This includes verifying that the item’s attributes, relationships, and dependencies are accurate. Any discrepancies or inconsistencies found during the verification must be addressed and resolved to maintain the accuracy of the CMDB.
Configuration item verification can be conducted manually or with the assistance of automation tools. Manual verification involves reviewing the documentation and physically checking the configuration items. On the other hand, automation tools can help automate the verification process by scanning the CMDB, comparing the actual configuration items with the documented ones, and generating reports of any inconsistencies.
The benefits of conducting configuration item verification include improved accuracy and reliability of the CMDB, better asset management, enhanced change management processes, and more efficient deployment and monitoring of services. It also helps organizations ensure compliance with regulatory requirements and mitigate risks associated with configuration errors.
In conclusion, configuration item verification is a critical process in configuration management that aims to ensure the accuracy and completeness of configuration items in a database. Through regular checks and audits, organizations can maintain the integrity of their CMDB and effectively manage their configuration items, whether they are hardware, software, or network assets.
Performing Configuration Item Audits
Configuration item audits are an essential part of the configuration management process. They involve evaluating the current state of software, hardware, and other assets in an organization’s IT infrastructure. Audits help ensure that the configuration items are in compliance with the defined baselines and meet the organization’s requirements.
During a configuration item audit, the configuration items are compared against their defined baselines. Baselines provide a point of reference for the configuration items and serve as a standard for comparison. The audit process helps identify any discrepancies or deviations from the baseline, allowing for corrective action to be taken.
A configuration item audit involves gathering information about each configuration item, such as its specifications, documentation, and current status. This information is typically stored in a configuration management database or another centralized system. The audit may include physical inspection of hardware assets, verification of software licenses, or monitoring network configurations.
The configuration item audit process can be performed manually or using automation tools. Automation can help streamline the audit process and ensure consistency and accuracy in the results. It can also provide a more efficient way to collect and analyze data from a large number of configuration items.
Configuration item audits are crucial for effective configuration management and overall IT service management. They help maintain the integrity of the configuration items, minimize the risk of unauthorized changes, and support accurate asset management. Regular audits also ensure that the configuration management process is implemented and followed consistently across the organization. By maintaining an accurate and up-to-date inventory record, organizations can better manage their IT assets and make informed decisions about changes or upgrades to their systems.
Documenting Configuration Item Status
Documenting the status of configuration items is a crucial part of the configuration management process. It involves keeping track of the current state and relevant information about each item in a structured and organized manner.
There are different approaches to documenting configuration item status. One common method is through a manual process, where updates are recorded and maintained manually. This can be time-consuming and prone to human errors.
Another approach is automation, using software tools specifically designed for configuration management. These tools can automatically collect and update data on configuration items in real-time. This ensures accuracy and reduces the chances of missing or outdated information.
The documentation of configuration item status includes various aspects such as the software or network components, databases, hardware, and other assets that are part of the system. Each item should have a well-defined and documented definition, including its purpose, specifications, and dependencies.
Monitoring and recording changes to configuration items is an essential part of documenting their status. This includes keeping track of changes made during deployment or updates, as well as identifying and managing any deviations from the baseline configuration. Changes to configuration items should be carefully documented to ensure transparency and enable proper evaluation and control.
Configuration item status documentation also plays a crucial role in service management. It provides valuable information for analyzing the impact of changes, troubleshooting issues, and meeting compliance requirements. It allows for effective asset management, as it helps in identifying and tracking the lifecycle of each item.
In conclusion, documenting configuration item status is a vital aspect of configuration management. It ensures accurate and up-to-date information about each item, facilitates change management, and supports effective service delivery and asset management. Whether done manually or through automation, proper documentation helps in maintaining system integrity and enables efficient decision-making processes.
Configuration Item Management
The management of configuration items (CIs) plays a crucial role in ensuring the smooth functioning of a complex IT system. Configuration items refer to any component or asset that is part of a system or service. This can include hardware, software, network devices, databases, records, and more.
Configuration item management involves various processes and activities, such as the definition, deployment, and documentation of CIs. A comprehensive understanding of the configuration items within a system is essential for effective management.
One of the key aspects of configuration item management is maintaining a baseline of each CI. A baseline is a documented snapshot of a CI’s configuration at a specific point in time. This provides a reference point for any changes made to the CI and enables proper monitoring and control of the system.
Effective configuration item management also involves change management processes. This includes accurately recording any changes made to a CI, as well as ensuring proper documentation and communication of these changes. Configuration items must be managed in a way that minimizes risk and disruptions to the system.
Automation can greatly aid in configuration item management. Automated tools and systems can be used to track and monitor CIs, ensure accurate documentation, and streamline the change management process. These tools can also assist in inventory management, helping organizations keep track of their various assets and resources.
Configuration item management is an ongoing process that requires continuous attention and maintenance. It is essential for ensuring the stability and reliability of a system or service. By effectively managing configuration items, organizations can minimize downtime, improve efficiency, and optimize their IT infrastructure.
Configuration Item Repository
A configuration item repository is a centralized inventory and record-keeping system that tracks the changes, services, systems, and automation related to software and hardware assets within an organization. It is a critical component of configuration item management, which ensures that the organization has visibility into the current state and historical changes of all configuration items.
The repository is typically implemented as a database or a document management system, where each configuration item is represented as a separate record. This allows for easy access and retrieval of information related to each item, including its definition, baseline, deployment process, and associated documentation.
By maintaining a comprehensive configuration item repository, organizations can effectively manage and track their assets throughout their lifecycle. This includes monitoring the changes made to configuration items, such as software updates, hardware upgrades, or network reconfigurations. Additionally, it provides a centralized location for storing important documentation, such as user manuals, technical specifications, and service level agreements.
The repository also plays a crucial role in asset management, as it helps organizations keep track of the hardware and software assets they own. It enables efficient planning and budgeting by providing an accurate inventory of assets, allowing organizations to identify potential redundancies or gaps in their IT infrastructure.
Furthermore, the configuration item repository facilitates the implementation of change management processes. It allows organizations to document and track proposed changes, ensuring that all stakeholders are aware of and have approved the changes before they are implemented. This helps prevent unauthorized changes, minimize potential disruptions, and improve the overall stability and reliability of the IT environment.
In conclusion, a configuration item repository is a vital tool for effective configuration item management. It acts as a centralized database of information, enabling organizations to track and manage their assets, document changes, and ensure the stability and reliability of their IT systems.
Choosing a Configuration Item Repository
When it comes to managing and maintaining the configuration items (CIs) within your organization, having a reliable and efficient configuration item repository is essential. This repository serves as a centralized record of all the CIs that are part of your system or service.
There are several factors to consider when choosing a configuration item repository. First and foremost, it should have comprehensive monitoring capabilities to ensure that any changes or updates to the CIs are tracked and recorded. This monitoring process plays a crucial role in maintaining the integrity of the CIs and helps with the overall management of your inventory.
Another important aspect to consider is the deployment process. The configuration item repository should provide a seamless and efficient way to deploy new CIs or update existing ones. This includes automating the deployment process as much as possible to minimize manual errors and ensure consistency across the system.
The ability to document and define each configuration item is also critical. The repository should allow you to create detailed records for each CI, including its purpose, dependencies, and any associated assets or baselines. This documentation is essential for understanding the role and impact of each CI within the system or service.
In addition, the configuration item repository should support various types of CIs, including software, hardware, network, and database components. It should provide a flexible and robust framework for storing and organizing these different types of items, allowing for easy retrieval and management.
Lastly, the repository should integrate well with your existing systems, such as change management or service management tools. This integration ensures a seamless flow of information and allows for better coordination and collaboration between different teams and processes.
In conclusion, choosing the right configuration item repository is crucial for effectively managing and maintaining the configuration items within your organization. Consider factors such as monitoring capabilities, deployment process, documentation features, support for different item types, and integration with existing systems to ensure a smooth and efficient management process.
Organizing and Maintaining the Repository
Organizing and maintaining the repository for configuration items is essential for effective configuration management. The repository serves as a centralized location where all the documents, records, and baselines related to the configuration items are stored. It provides a structured and organized approach to managing the configuration items throughout the software development life cycle.
Documentation: The repository contains various documentation related to configuration items, such as design documents, user manuals, and technical specifications. These documents provide a detailed description of the configuration items and their functionalities.
Deployment Records: The repository also maintains deployment records that track the deployment of configuration items in different environments. These records help in monitoring the deployment process and ensuring that the correct versions of configuration items are used.
Database: The repository includes a database that stores the information about the configuration items, including their attributes, relationships, and dependencies. This database serves as a valuable resource for managing and tracking the configuration items throughout their lifecycle.
Change Management: The repository houses the change management process, which facilitates the tracking and control of changes made to the configuration items. This process ensures that all changes are properly documented and approved before being implemented.
Inventory Management: The repository serves as an inventory management system for the configuration items. It keeps track of the different versions, locations, and states of the configuration items, providing a comprehensive view of the inventory.
Automation: The repository may incorporate automation tools and systems to streamline the configuration management process. These tools automate tasks such as version control, documentation generation, and dependency tracking, making the management of configuration items more efficient.
Service Management: The repository can be integrated with service management systems to provide a seamless experience for managing configuration items within the context of service delivery. This integration ensures that configuration items are aligned with service requirements and delivers value to the customers.
Network and Hardware: The repository includes information about network and hardware configuration items, such as routers, switches, servers, and other network devices. This information helps in managing and maintaining the network infrastructure efficiently.
Asset Management: The repository serves as a central repository for managing and tracking hardware and software assets. It keeps a record of all the assets, including their location, ownership, and usage, ensuring that the assets are effectively utilized.
System Configuration: The repository stores the configurations of software systems, including the settings, preferences, and options. This information helps in maintaining and reproducing the desired system configuration across different environments.
Configuration Item Baseline
A Configuration Item (CI) Baseline is a fundamental aspect of the configuration management process. It refers to a specific version of a configuration item that has been formally documented and approved. Configuration items are any tangible or intangible components of a system or service that need to be managed and controlled.
In the context of configuration management, a baseline is a fixed reference point that serves as the basis for future changes and comparisons. It represents a snapshot of the system or service in a particular state, capturing all the relevant details and configurations at a specific point in time.
The CI Baseline is maintained in a centralized database, often called a Configuration Management Database (CMDB). This database acts as a record and inventory of the various configuration items, their attributes, and their relationships with other components in the system.
The establishment and management of a CI Baseline involve several key processes. The first step is the identification and definition of the configuration items that are considered essential for the system or service. This process involves categorizing and documenting each item, including details such as its purpose, function, and dependencies.
Once the configuration items are identified, the baseline is created by documenting their current state and configurations. This includes capturing information about the hardware, software, network, and other relevant components. A baseline document is typically created to serve as a reference point for any future changes or updates.
The CI Baseline plays a crucial role in the change management process. It provides a baseline against which any proposed changes can be assessed and evaluated. Any modifications or updates to the system or service must go through a formal change control process, where the impact on the CI Baseline is carefully considered.
Automation tools and software can greatly assist in the management of CI Baselines. These tools can help track and monitor changes, maintain an accurate inventory, and ensure compliance with defined configurations. They provide a systematic approach for deployment, updating, and tracking changes to configuration items.
In conclusion, a Configuration Item Baseline is a documented and approved version of a configuration item that serves as a reference point for future changes and comparisons. It is a critical part of the configuration management process, helping to ensure consistency, control, and accuracy in system and service configurations.
Establishing Configuration Item Baselines
Establishing configuration item baselines is a crucial step in the management of a system or service. A configuration item is any component of the system or service that must be managed and controlled. This can include hardware, software, documentation, databases, and more.
To create a baseline, the configuration items need to be identified and defined. This involves recording details such as the item’s purpose, version, and other relevant information. The baseline serves as a reference point for comparison and ensures consistency throughout the system or service.
Monitoring and tracking changes to the configuration items is essential for maintaining the baseline. A change management process should be implemented to ensure that any modifications or updates to the items are documented and approved. This allows for proper control and prevents unauthorized changes from being made.
Automation can greatly assist in establishing and maintaining configuration item baselines. Automated tools can help with inventory management, version control, and tracking changes. This eliminates the need for manual tracking and reduces the risk of errors or omissions.
The baseline also serves as an asset for deployment or restoration purposes. In the event of a system failure, having a well-documented baseline ensures that all necessary configuration items can be quickly identified and restored. This minimizes downtime and enables efficient recovery.
In summary, establishing configuration item baselines involves the definition, documentation, and management of the components that make up a system or service. This process allows for consistency, control, and efficient management of changes. By implementing a baseline, organizations can ensure that their systems and services are reliable and meet their intended purpose.
Managing Changes to Configuration Item Baselines
Managing changes to configuration item baselines is a crucial aspect of configuration management. A baseline is a reference point that represents the state of a configuration item at a specific point in time. It serves as a foundation for managing changes to configuration items.
When a change is required in a configuration item, whether it is a software, hardware, or network asset, it is necessary to carefully document and record the proposed change. This information is typically stored in a configuration management database (CMDB) or a configuration management system (CMS).
Once the change request is documented, it goes through a formal review process. This process involves evaluating the impact of the change on the configuration item, as well as assessing any potential risks or conflicts with other items. The change request may also require approval from relevant stakeholders or a change control board.
After the change request is approved, the configuration item baseline is updated to reflect the proposed changes. This update includes modifying relevant attributes, such as version numbers, release dates, and dependencies. It is important to ensure that all changes made to the configuration item are accurately recorded and reflected in the baseline.
Furthermore, managing changes to configuration item baselines often involves automation and deployment processes. This allows for efficient and consistent implementation of changes across multiple systems. Automation eliminates manual errors and helps enforce compliance with configuration management policies.
Throughout the change management process, it is essential to have effective monitoring and control mechanisms in place. This enables continuous monitoring of the configuration items and ensures that any unauthorized or unexpected changes are detected and addressed promptly.
In summary, managing changes to configuration item baselines involves a systematic and rigorous process of documenting, reviewing, and updating configuration items. It requires the use of configuration management tools and techniques, as well as effective monitoring and control mechanisms. By properly managing and controlling changes, organizations can maintain the integrity and stability of their configuration items and provide reliable and efficient services to their customers.
Configuration Item Traceability
Configuration Item Traceability refers to the ability to track and manage the various components and attributes of a configuration item throughout its lifecycle. A configuration item is a specific entity that is a part of a larger system or service, such as hardware, software, documentation, or a network component.
The traceability of configuration items is vital for effective configuration management. It allows for the identification of each item, its relationship to other items, and the ability to track changes made to it over time. This traceability enables organizations to have a comprehensive understanding of their IT infrastructure and ensures that all components are properly documented and managed.
Configuration item traceability begins with the initial definition and creation of the item. This includes documenting its specifications, properties, and relationships to other items. Throughout the deployment process, the item’s status, location, and other relevant information are recorded and updated in a central database or asset management system.
Changes to configuration items are also tracked and documented. Any modifications, updates, or replacements made to the item are recorded, along with the reason for the change and the individual responsible. This change history provides a clear audit trail and allows organizations to understand the impact of each modification on the overall system or service.
Configuration item traceability is essential for efficient change management. It allows organizations to assess the potential impact of proposed changes and make informed decisions about whether to proceed. Additionally, it facilitates troubleshooting and problem resolution by providing a clear record of the item’s configuration and its relationship to other components.
Automation and monitoring tools play a crucial role in configuration item traceability. These tools can automatically discover and inventory configuration items, monitor their performance, and alert administrators to any deviations from the baseline configuration. This proactive approach helps organizations identify and resolve configuration issues before they impact the quality of service.
In conclusion, configuration item traceability is the key to effective configuration management. It enables organizations to maintain an accurate and up-to-date record of their IT assets, track changes made to those assets, and make informed decisions about their IT infrastructure. By implementing robust traceability practices, organizations can ensure the stability, reliability, and security of their systems and services.
Ensuring Configuration Item Traceability
In configuration management, ensuring traceability is essential to effectively track and manage configuration items throughout their lifecycle. Traceability provides a record of the relationships and dependencies between different items, allowing for better understanding and control of the system as a whole.
One way to ensure traceability is by maintaining a comprehensive inventory of all configuration items. This inventory should include both hardware and software components, as well as any other related assets. Each item should be assigned a unique identifier and its properties, such as version number and dependencies, should be recorded.
A baseline, or a reference point in the configuration item’s lifecycle, is another important aspect of traceability. Baselines capture the state of the system at a specific point in time and provide a foundation for managing and controlling changes. By establishing and documenting baselines, organizations can easily track and compare different versions of configuration items.
Change management processes are also crucial for ensuring traceability. These processes should include proper documentation and monitoring of any changes made to configuration items. This can be achieved through using an automated system that tracks and records all changes, including the date, time, and person responsible for the change.
Configuration item traceability can further be enhanced through the use of a dedicated configuration management database (CMDB). A CMDB serves as a centralized repository for all configuration item data, allowing for easy access and retrieval of information. It helps in maintaining accurate and up-to-date records of configuration items, their relationships, and their current state.
Additionally, organizations should implement network and system monitoring tools to ensure ongoing traceability. These tools can actively monitor the configuration items, alerting the IT team about any unauthorized changes or anomalies. By continuously monitoring the configuration items, organizations can promptly address any issues and maintain the integrity of the system.
In summary, ensuring configuration item traceability is essential for effective configuration management. By maintaining a comprehensive inventory, establishing baselines, implementing change management processes, utilizing a CMDB, and leveraging network and system monitoring, organizations can effectively track and manage their configuration items throughout their lifecycle.
Using Configuration Item Traceability for Change Management
Configuration item traceability plays a crucial role in change management processes. It involves the recording and monitoring of changes made to configuration items throughout their lifecycle. A configuration item can refer to any component, system, service, or asset that is part of an organization’s infrastructure.
The traceability process starts with the definition of configuration items and their relationships. This includes identifying software, hardware, documentation, databases, networks, and other assets that make up the organization’s configuration.
By establishing traceability, organizations can effectively track changes and understand the impact they might have on the overall system. This helps in planning and managing change deployments, ensuring that any alterations to the configuration are done in a controlled and coordinated manner.
Configuration item traceability allows organizations to maintain a comprehensive inventory of their assets and establish a baseline for their configuration. It enables efficient change management by providing a clear picture of the dependencies between different items and services.
With the help of automation tools and software, organizations can easily track and document changes made to configuration items. This ensures that all modifications are properly recorded and can be easily accessed whenever required.
In conclusion, configuration item traceability is a vital component of change management processes. It enables organizations to effectively manage and control changes to their infrastructure, ensuring stability and minimizing risks associated with alterations to the configuration.
Best Practices for Configuration Item Management
Deployment Definition: Clearly define the configuration items that will be part of the deployment process. This includes identifying the software, hardware, and network components that need to be configured and managed.
Change Management: Implement a robust change management process to track and control changes to configuration items. This includes documenting and reviewing proposed changes, assessing their impact, and ensuring proper authorization and implementation.
Inventory Management: Maintain an accurate inventory of all configuration items in a central database. This inventory should include details such as item name, description, version, location, and any associated documentation or records.
Baseline Management: Establish and maintain baseline configurations for different systems and services. This involves defining a standard configuration for each item and periodically auditing and updating the baselines to ensure their accuracy and relevance.
Automation and Monitoring: Implement automation and monitoring tools to streamline the management of configuration items. These tools can automate the deployment and configuration processes, detect and alert on changes or discrepancies, and provide real-time visibility into the status of configuration items.
Document and Record Management: Maintain thorough documentation and records for all configuration items. This includes documenting their purpose, specifications, dependencies, and any related processes or procedures. It also involves keeping records of any changes, incidents, or issues that occur throughout the item’s lifecycle.
Item Lifecycle Management: Define and enforce clear processes for the creation, modification, removal, and retirement of configuration items. This includes establishing roles and responsibilities, defining approval workflows, and implementing controls to ensure that all changes are properly documented and authorized.
Service Integration: Integrate configuration item management with other IT service management processes and tools. This ensures that configuration items are effectively tracked and managed throughout their lifecycle, and that their configurations and dependencies are accurately reflected in other IT systems and services.
By following these best practices, organizations can ensure a high level of control and consistency in their configuration item management processes. This helps minimize the risk of errors, disruptions, and security breaches, and enables efficient and reliable IT service delivery.
Regular Reviews and Updates
Regular reviews and updates are an essential part of configuration item management. As the environment changes, it is important to regularly review and update the configuration items to ensure that they accurately reflect the current state of the system or service.
During the review process, each configuration item, whether it is a hardware item, a software asset, a network configuration, or a document, should be checked for any changes or updates that may have occurred since the last review. This includes changes in the configuration item’s baseline, changes in the deployment process, or any changes in the monitoring or management of the item.
Regular updates also involve updating the configuration item database or record, which serves as the central repository for all configuration items. This database should be regularly updated to reflect the current state of the system or service. It is important to document any changes or updates made to the configuration items and maintain a record of these changes for future reference.
Automated tools and software can greatly assist in the regular review and update process. These tools can help identify any discrepancies or inconsistencies in the configuration items and provide recommendations for remediation. They can also automate the process of updating the configuration item database and generating reports on any changes or updates made.
Regular reviews and updates are not only important for maintaining an accurate and up-to-date record of the system or service’s configuration, but also for ensuring that any changes or updates are properly implemented and documented. This can help prevent errors, issues, and downtime by identifying potential problems and addressing them proactively.
Importance of Regular Reviews and Updates
Regular reviews and updates are crucial for effective configuration management processes. These activities help ensure that the inventory of hardware, software, and network assets is accurate and up-to-date. By reviewing and updating the configuration items regularly, organizations can better manage changes and maintain a stable baseline for their systems.
Regular reviews and updates involve examining each configuration item in the database, assessing its current state, and identifying any changes or updates that may be required. This helps in keeping track of the current status of each item and ensures that the documentation and record of the item are accurate and reliable.
In addition to maintaining an accurate inventory, regular reviews and updates also help in monitoring the performance of configuration items and identifying any issues or vulnerabilities. This allows for timely action to be taken to address these issues and ensure the stability and security of the system.
Regular reviews and updates can also help in the efficient deployment of new services or changes to existing services. By ensuring that all relevant configuration items are updated and in line with the desired state, organizations can minimize the risk of errors or disruptions during the deployment process.
Automation can play a significant role in facilitating regular reviews and updates. Automated tools and systems can help in scanning the inventory, comparing it with a desired configuration, and generating reports on discrepancies or inconsistencies. This not only saves time but also increases the accuracy and reliability of the review and update process.
In conclusion, regular reviews and updates are essential for effective configuration management. They help organizations maintain an accurate and reliable inventory, address issues and vulnerabilities promptly, ensure smooth deployment of new services, and leverage automation for efficiency and accuracy. By incorporating regular reviews and updates into their configuration management practices, organizations can enhance their overall system stability and security.
Conducting Effective Reviews and Updates
Conducting regular reviews and updates is crucial for maintaining an efficient and reliable network and system configuration. These reviews help ensure that the configuration items are up to date and in line with the organization’s requirements and standards.
Monitoring the baseline configuration is essential to identify any inconsistencies or deviations in the network and system configuration. This involves tracking changes to hardware and software components, documenting their configurations, and comparing them to the defined baseline.
An important aspect of conducting effective reviews is keeping an accurate inventory of all configuration items. This inventory should include detailed information about each item, such as its unique identifier, description, location, and current status. By having a comprehensive inventory, organizations can easily track and manage their assets.
Regularly updating the configuration items is necessary to incorporate any changes or enhancements to the network and system. This includes deploying software updates, hardware upgrades, or configuration changes as required. Accurate documentation of these updates is crucial for maintaining a record of all changes made to the configuration items.
Effective configuration item management involves establishing a defined process for reviewing and updating configuration items. This process should outline the steps for conducting reviews, documenting changes, and ensuring that all updates are properly implemented. By following a standardized process, organizations can minimize errors and maintain the integrity of their configuration items.
In conclusion, conducting effective reviews and updates is essential for maintaining an optimized and reliable network and system configuration. By monitoring the baseline, maintaining an accurate inventory, and following a defined process, organizations can ensure that their configuration items are up to date and aligned with their requirements and standards.
Documentation and Documentation Management
Documentation is an essential component of configuration management. It involves keeping records, creating baselines, and managing changes in an organization’s assets and services. Documenting configuration items, such as hardware, software, network components, and databases, helps ensure accurate and up-to-date information about the system.
Documentation management is the process of creating, organizing, and maintaining documents related to configuration items. It includes establishing guidelines and procedures for documentation, defining standards for document formats, and assigning responsibilities for document creation and maintenance. Effective documentation management ensures that all relevant information is captured and easily accessible, facilitating efficient asset deployment, change management, and system monitoring.
One important aspect of documentation management is version control. It involves maintaining a record of changes made to a document over time, including who made the change and when. Version control helps in tracking the evolution of a document and ensures that the correct and most recent version is being used. This is particularly important when managing configuration items that undergo frequent changes or updates.
Documentation management also includes defining the scope and structure of documentation. It involves categorizing configuration items into logical groups and creating hierarchical structures to organize the documentation. This allows for easy navigation and retrieval of information when needed. Additionally, documenting the relationships between different configuration items helps in understanding the dependencies and impact of changes within the system.
Furthermore, effective documentation management includes establishing a formal approval process for creating and modifying documents. This process helps ensure that all documentation follows the defined standards and is accurate before being released. It also provides a mechanism for tracking and auditing changes made to the documentation.
Creating and Maintaining Documentation
Documentation plays a crucial role in the configuration management process. It serves as a comprehensive record of all the configuration items within a system or network. This includes hardware, software, and network assets. Documentation helps in creating a baseline for the system, as well as in tracking any changes made to the configuration items.
Creating documentation starts with defining the configuration items. Each item should have a clear and detailed definition, including information on its purpose, specifications, and dependencies. This documentation helps in identifying the relationships between different configuration items and ensuring that all necessary components are accounted for.
Once the configuration items are defined, they need to be recorded in a database or an inventory management system. This database serves as a central repository for all the configuration items and their associated information. It also allows for easy retrieval and monitoring of the items, facilitating efficient management of the system.
Documentation should also include information on the deployment and change management processes. This includes details on how configuration items are deployed, updated, and retired, as well as the procedures for requesting and approving changes. This information helps in ensuring that all changes are properly documented and can be tracked throughout the system.
Maintaining documentation is equally important as creating it. Regularly updating and reviewing the documentation ensures that it remains accurate and up to date. This includes capturing any changes made to the configuration items, whether it is a hardware upgrade, software patch, or network reconfiguration. Additionally, documentation should also include monitoring and troubleshooting processes, providing guidelines for identifying and resolving any issues.
In conclusion, creating and maintaining documentation is a critical aspect of the configuration management process. It serves as a comprehensive record of all configuration items, providing a baseline for the system. By accurately documenting information on hardware, software, and network assets, as well as deployment and change management processes, organizations can effectively manage their systems and ensure smooth operations.
Document Management Best Practices
Document management refers to the practices and processes involved in storing and organizing documents in a systematic and efficient manner. Effective document management is crucial for businesses to ensure easy access to important information, streamline workflows, and maintain compliance with industry regulations. Here are some best practices to consider:
- Document Classification: Develop a clear and consistent classification system to categorize documents based on their type, purpose, and content. This will facilitate easy retrieval and ensure that documents are stored in the appropriate locations.
- Version Control: Implement a version control system to manage document revisions and track changes over time. This prevents confusion and ensures that the most up-to-date information is readily available.
- Metadata Management: Use metadata to provide additional information about documents, such as author, creation date, and keywords. This enables efficient searching and allows users to quickly locate relevant documents.
- Document Security: Set up adequate security measures to protect sensitive documents from unauthorized access. This may include encryption, access controls, and regular monitoring of document activity.
- Document Retention: Define clear policies for document retention and disposal. This helps to minimize clutter and ensures compliance with legal and regulatory requirements.
- Document Workflow: Establish defined processes for document creation, review, approval, and distribution. Automating these workflows can improve efficiency and reduce manual errors.
- Backup and Disaster Recovery: Implement regular backup procedures to safeguard documents from hardware failures, natural disasters, and other unforeseen events. This ensures business continuity and minimizes the risk of data loss.
- Document Collaboration: Use collaborative tools and software that allow multiple users to work on documents simultaneously. This promotes real-time collaboration and enhances productivity.
- Document Auditing: Regularly audit document management processes to identify areas for improvement and ensure adherence to established policies. This includes monitoring document access, changes, and usage patterns.
- Training and Awareness: Provide comprehensive training to employees on document management best practices and the proper use of document management systems. This helps to ensure consistency and reduces the risk of human error.
Implementing these document management best practices will enable organizations to effectively manage their documents, improve efficiency, and maintain a centralized and reliable repository of information. By taking a systematic approach to document management, businesses can optimize their processes, enhance collaboration, and enhance overall productivity.
Collaboration and Communication
In the world of configuration management, collaboration and communication play a crucial role in ensuring the successful deployment and change management of configuration items. Configuration items are the building blocks of a system, whether it’s hardware or software, and maintaining an accurate and up-to-date record of these items is crucial for effective management.
When it comes to collaboration, teams need to work together to ensure that changes to configuration items are properly documented and communicated. This includes updating the database or inventory with any modifications made to hardware or software, as well as maintaining a record of the baseline configuration for reference.
In order to facilitate effective communication and collaboration, it is important to establish clear processes and guidelines for handling configuration items. This could include defining roles and responsibilities within the team, establishing a structured change management process, and implementing automation and monitoring tools to track changes and ensure compliance with predefined baselines.
Collaboration and communication also extend beyond the internal team. It is important to have a clear understanding of the dependencies and relationships between different configuration items, such as network devices, servers, databases, and applications. This allows for effective coordination with other teams or service providers to ensure that changes or updates to one item do not have unintended consequences on others.
Overall, effective collaboration and communication are essential for successful configuration item management. By establishing clear processes, maintaining accurate records, and engaging in proactive communication, teams can ensure that changes and deployments are carried out smoothly and with minimal disruption to the system or service.
Establishing Effective Collaboration
In today’s fast-paced and interconnected world, collaboration plays a crucial role in ensuring the success of any project or initiative. When it comes to IT infrastructure, establishing effective collaboration is essential for seamless deployment, management, and monitoring of network configurations and changes.
A key component of effective collaboration is the establishment of a centralized configuration item database. This database serves as a single source of truth, containing a comprehensive record of all configuration items, such as hardware and software assets, network components, and system baselines. By maintaining an up-to-date and accurate inventory of configuration items, teams can easily access and retrieve critical information, saving time and effort.
Documenting and recording changes to configuration items is another important aspect of collaboration. Teams can use change management processes to track and record any modifications made to configuration items, ensuring transparency and accountability. This documentation assists in troubleshooting, as it provides a clear history of changes that have been made, allowing teams to identify potential issues or conflicts.
Automation can also play a significant role in establishing effective collaboration. By leveraging automation tools and software, teams can streamline repetitive tasks and processes, reducing the risk of human error and increasing productivity. Automation can be used to automate the deployment of configuration items, monitor their performance, and generate reports, freeing up valuable time for teams to focus on more strategic initiatives.
In summary, establishing effective collaboration in the context of configuration item management involves maintaining a centralized database, documenting and recording changes, and leveraging automation tools. By doing so, teams can streamline their processes, ensure accurate and timely information retrieval, and ultimately drive the success of their IT infrastructure projects.
Communicating Configuration Item Changes
When it comes to managing and maintaining a complex system, such as a network or a hardware deployment, keeping track of configuration items is crucial. Configuration items can include hardware, software, processes, and more, and any change to these items can have a significant impact on the overall system.
One effective way to manage these changes is by implementing a configuration management system, which helps to keep a record of all configuration items and their corresponding changes. This system can be in the form of a database, a document, or a specialized software.
Communication is key when it comes to managing configuration item changes. It is important to inform all relevant stakeholders about any changes that will be made to configuration items, as well as the reasons for these changes. This can include notifying the system administrators, the IT team, and any other individuals who may be affected by the changes.
One common method of communicating these changes is through a change management process. This process typically involves documenting the change, assessing its impact, and getting approval from the appropriate stakeholders before implementing the change.
In addition to communicating the changes, it is also important to keep a record of the changes that have been made. This can be done by maintaining an inventory or a baseline of the configuration items, which includes details such as their current state, their previous state, and any changes that have been made to them.
Another important aspect of communicating configuration item changes is monitoring. This can involve automated monitoring tools that keep track of any changes to the system and notify the relevant stakeholders in real-time. Monitoring can help ensure that any changes are implemented correctly and that any issues or errors are identified and resolved promptly.
In conclusion, communicating configuration item changes is vital for the proper management of a complex system. By keeping a record of changes, informing stakeholders, and implementing appropriate monitoring, organizations can ensure that configuration items are properly managed and that any changes are implemented smoothly and efficiently.
FAQ about topic “What is a configuration item: A comprehensive guide”
What is a configuration item?
A configuration item (CI) is a fundamental component of an IT system. It can be a hardware device, software component, documentation, or any other entity that needs to be managed and controlled to ensure the IT system’s proper functioning.
Why are configuration items important in IT management?
Configuration items are important in IT management because they provide a structured approach to managing and controlling IT systems. By defining and categorizing configuration items, organizations can accurately track changes, identify dependencies, and assess the impact of modifications on the overall system.
How should configuration items be documented?
Configuration items should be documented using a centralized configuration management database (CMDB). The CMDB acts as a repository of information about the configuration items, their attributes, relationships, and history. This documentation enables IT teams to have a clear understanding of the system’s configuration and its evolution over time.
What are the challenges of managing configuration items?
Managing configuration items can be challenging due to various factors. One challenge is the constant change in IT environments, which requires regular updates and modifications to the configuration items. Another challenge is maintaining accuracy and consistency in the documentation, as configuration items may have complex relationships and dependencies. Additionally, tracking and controlling configuration items across different teams and departments can be difficult.
How can organizations ensure the integrity of configuration items?
Organizations can ensure the integrity of configuration items by implementing strong change management processes. This includes having a clear approval process for modifications, conducting impact assessments before making changes, and having proper documentation and communication channels in place. Regular audits and reviews of the configuration items can also help identify and resolve any integrity issues.


