Data Execution Prevention (DEP) is a critical system defense mechanism that helps protect against various cyber threats. It is a technology that gives the control of executing code in memory to the operating system, aiming to prevent the exploitation of vulnerabilities.
Vulnerabilities in software often arise from memory-related issues, such as buffer overflows. Cybercriminals can take advantage of these vulnerabilities by injecting malicious code into a program’s memory and executing it. This kind of attack, known as an exploit, can lead to data breaches, system compromise, or the spread of malware. DEP plays a crucial role in preventing such attacks by blocking the execution of code in memory regions marked as non-executable.
DEP is implemented at both the hardware and software levels. Hardware-enforced DEP relies on CPU support to mark memory pages as executable or non-executable. This prevents the execution of code in non-executable pages, making it more difficult for attackers to run their malicious code. Software-enforced DEP, on the other hand, is implemented by the operating system and certain applications. It uses data structure checks and code signing to identify and prevent the execution of malicious code.
By preventing the execution of unauthorized code, DEP adds an extra layer of protection to the system. It helps mitigate the risk of attacks that exploit vulnerabilities in software, reducing the likelihood of successful malware infections and other cyber threats. However, it is important to note that DEP is just one component of a comprehensive cybersecurity strategy. Organizations and individuals should also implement other security measures, such as firewalls, antivirus software, and regular software updates, to ensure maximum protection.
Contents
- 1 Understanding Data Execution Prevention
- 2 The Benefits of Data Execution Prevention
- 3 Implementing Data Execution Prevention
- 4 Data Execution Prevention Best Practices
- 5 FAQ about topic “Data Execution Prevention: What You Need to Know”
- 6 What is Data Execution Prevention (DEP)?
- 7 How does Data Execution Prevention work?
- 8 Is Data Execution Prevention enabled by default?
- 9 What are the benefits of using Data Execution Prevention?
- 10 Can Data Execution Prevention interfere with legitimate software?
Understanding Data Execution Prevention
Data Execution Prevention (DEP) is an important cybersecurity technology that helps protect computer systems and software from vulnerabilities and malicious attacks. It works by preventing the execution of code in memory areas that are intended for data storage, thus reducing the risk of malware and exploit attacks.
DEP operates at the hardware level and is supported by both the operating system and the processor. It provides an additional layer of defense against buffer overflow attacks, where an attacker may exploit a vulnerability in a program to overwrite memory and execute malicious code. By preventing the execution of code in these memory areas, DEP mitigates the threat and enhances system security.
DEP can be implemented in two different modes: hardware-enforced DEP and software-enforced DEP. Hardware-enforced DEP relies on the processor’s built-in capabilities to mark certain memory pages as non-executable, while software-enforced DEP is achieved through software settings and does not require specific hardware support.
While DEP is an effective defense mechanism, it is important to note that it is not a foolproof solution. Advanced malware and exploits can still find ways to bypass DEP, especially if they are designed to exploit zero-day vulnerabilities that are unknown to security software. Therefore, it is crucial to keep software and systems up-to-date with the latest patches and security updates to minimize the risk of attacks.
In conclusion, Data Execution Prevention is a critical technology in the field of cybersecurity. By preventing the execution of code in certain memory areas, DEP helps protect systems and software from malware and exploit attacks. However, it should be complemented with other security measures and best practices to ensure comprehensive protection against evolving cyber threats.
What is Data Execution Prevention?
Data Execution Prevention (DEP) is a protection feature built into the operating system that helps prevent the execution of malicious code in order to enhance system security. It is an essential technology in defending against a wide range of threats, including buffer overflow exploits and certain types of malware attacks.
DEP works by monitoring the execution of code in memory and preventing the execution of any code that is not explicitly allowed. This helps to prevent the exploitation of vulnerabilities that could be present in software or system components, reducing the risk of unauthorized access or control over a system.
One of the main vulnerabilities that DEP helps to mitigate is buffer overflow attacks. These attacks occur when a program or process attempts to write more data into a buffer than it can hold, leading to the overwriting of adjacent memory locations. By preventing the execution of code in these vulnerable areas of memory, DEP can effectively block buffer overflow exploits.
DEP can be implemented in both hardware and software. In hardware-based DEP, the processor and its memory management unit provide the necessary defense mechanisms to identify and prevent the execution of malicious code. Software-based DEP, on the other hand, relies on the operating system and additional software tools to enforce the execution control.
In summary, Data Execution Prevention is a critical defense mechanism that helps protect against memory-related vulnerabilities and malicious code execution. By preventing the execution of code in certain areas of memory, DEP reduces the risk of system compromise and enhances overall system security.
How Does Data Execution Prevention Work?

Data Execution Prevention (DEP) is a security technology designed to prevent malicious code from executing on a system. It works by monitoring and controlling the execution of code in a system’s memory, specifically targeting buffer overflow vulnerabilities.
A buffer overflow vulnerability occurs when a program tries to store more data in a buffer than it can handle. Malware can exploit this vulnerability to insert malicious code into the system’s memory, which can then be executed to launch attacks or gain unauthorized access.
DEP acts as a defense mechanism against such threats by identifying and blocking the execution of code that is stored in memory regions marked as non-executable. It does this by keeping track of the memory pages that contain code and data, and only allowing the execution of code from memory pages marked as executable.
DEP uses a combination of hardware and software technology to provide this protection. On supported processors, such as the Intel Pentium Pro and later models, it utilizes the processor’s built-in memory protection feature called the Execute Disable Bit (XD bit). This bit allows the operating system to mark certain memory pages as non-executable, preventing code execution.
In addition to hardware support, DEP also relies on software-based techniques. It works in conjunction with the operating system and applications to mark memory pages as either executable or non-executable. In the case of an application, DEP monitors the memory it uses and prevents any execution from non-executable regions.
DEP plays a crucial role in the overall security and protection of a system. By preventing the execution of malicious code, it reduces the risk of various types of exploits, such as buffer overflow attacks. It is an essential component of modern cybersecurity strategies, providing an additional layer of defense against malware and other threats.
Why is Data Execution Prevention Important?
Data Execution Prevention (DEP) is a technology that helps protect computer systems by preventing certain types of attacks and exploits. It works by marking certain areas of memory as non-executable, preventing them from being used to store and run code. This serves as a defense mechanism against buffer overflow and other similar attacks that try to inject malicious code into a system’s memory.
DEP is an important security feature because it adds an additional layer of protection against software vulnerabilities and exploits. By preventing the execution of code in certain areas of memory, it helps mitigate the risk of attacks that target these vulnerabilities. It acts as a safeguard that helps protect sensitive data and the overall integrity of the system.
One of the main benefits of DEP is that it is implemented in hardware, making it more difficult for attackers to bypass. While software-based security measures can be circumvented, DEP’s hardware-enforced protection provides a higher level of security. It ensures that even if a software vulnerability is exploited, the attacker is unable to execute code from the compromised area of memory.
DEP plays a crucial role in the overall cybersecurity of a system. It helps guard against memory-related vulnerabilities, which are a common target for attackers. By preventing the execution of malicious code, DEP minimizes the potential damage that can be caused by an attack. It acts as a proactive measure that strengthens the system’s security and reduces the risk of data breaches and unauthorized access.
In conclusion, Data Execution Prevention is important because it provides an additional layer of protection against software vulnerabilities and exploits. By preventing the execution of code in certain areas of memory, DEP helps mitigate the risk of attacks and enhances the overall security of a system. It serves as a defense mechanism and plays a crucial role in safeguarding sensitive data and protecting against cybersecurity threats.
The Benefits of Data Execution Prevention
Data Execution Prevention (DEP) is a security technology that helps protect the system from malware attacks and data exploits. It is designed to protect the memory by preventing unauthorized execution of code in certain areas, such as the buffer overflow vulnerability. Here are some of the benefits of using DEP:
1. Hardware-Level Protection: DEP is implemented at the hardware level, making it an effective defense against attacks. By utilizing hardware support, it adds an extra layer of protection to the system’s memory, making it difficult for attackers to execute malicious code.
2. Prevention of Buffer Overflow Attacks: DEP helps prevent buffer overflow attacks by marking executable memory regions as non-executable. This prevents attackers from exploiting vulnerabilities in software that could be used to execute malicious code through buffer overflow techniques.
3. Improved System Stability: DEP helps enhance the stability and overall performance of the system. By preventing the execution of unauthorized code, it reduces the risk of system crashes, hangs, and other stability issues caused by malware or malicious attacks.
4. Enhanced Software Security: DEP provides an additional layer of security to software applications. It helps protect against various types of malware, including Trojans, viruses, and other forms of malicious software that rely on executing code in memory.
5. Mitigation of Zero-Day Threats: DEP can help mitigate the risk of zero-day attacks. Since it prevents the execution of unauthorized code, it reduces the likelihood of successful exploitation of unknown vulnerabilities that have not yet been patched by software vendors.
Overall, Data Execution Prevention is a crucial technology for enhancing system security and protecting against various types of malware attacks. By preventing the execution of unauthorized code, it adds an extra layer of protection and reduces the risk of data breaches and other cybersecurity threats.
Improved System Security
In today’s cybersecurity landscape, it is crucial to have a strong defense against malware and other malicious attacks that can compromise a system’s security. Data Execution Prevention (DEP) is a technology that provides an additional layer of protection against these threats.
DEP helps protect a system by preventing the execution of code in data-only memory regions, such as the stack and heap. By controlling the memory execution, DEP can effectively mitigate the risk of a successful exploit or attack.
One of the key benefits of DEP is its hardware-enforced execution control. Unlike software-based security measures, DEP leverages hardware features to monitor the execution of code in memory. This ensures that even if a vulnerability exists in the software, DEP can still prevent the execution of any malicious code.
DEP acts as a shield for a system, preventing the execution of malicious code that may be injected through various means, such as web browsers or email attachments. By denying unauthorized code execution, DEP helps to minimize the impact of malware and greatly enhances the system’s overall security.
By incorporating DEP into a system’s security framework, organizations can significantly reduce the chances of falling victim to an attack. DEP serves as a proactive defense mechanism that continuously monitors and protects against potential threats, ensuring the integrity and confidentiality of critical data.
In conclusion, DEP is a powerful technology that strengthens a system’s security by preventing the execution of malicious code. With its hardware-enforced execution control and proactive approach to cybersecurity, DEP is a critical component in defending against the ever-evolving landscape of threats and attacks.
Effective Countermeasure against Buffer Overflow Attacks
Buffer overflow attacks are a serious threat to software security. They occur when a program attempts to store more data in a buffer than it can handle, resulting in the overflow of data into adjacent memory locations. This can lead to the execution of malicious code, compromising the system’s security.
To protect against buffer overflow attacks, data execution prevention (DEP) technology can be implemented. DEP is a cybersecurity defense mechanism that prevents malicious code from being executed in specific areas of memory. By marking certain memory regions as non-executable, DEP can effectively block buffer overflow exploits.
DEP operates at both the hardware and software levels. At the hardware level, it utilizes special flags in the memory management unit to designate memory regions for code execution or data storage. At the software level, the operating system and applications are responsible for enforcing DEP policies.
By implementing DEP, the risk of buffer overflow attacks can be significantly reduced. DEP prevents the execution of malicious code injected into a vulnerable program’s memory, thereby mitigating the potential damage caused by such attacks. However, it should be noted that DEP is not a foolproof solution and should be used in conjunction with other security measures to ensure comprehensive protection against malware and other cyber threats.
In summary, DEP is an effective countermeasure against buffer overflow attacks. By preventing the execution of malicious code in specific memory areas, DEP enhances software security and reduces the risk of exploitable vulnerabilities. It is an essential component of modern cybersecurity defenses and should be implemented alongside other protective measures to ensure the highest level of system protection.
Implementing Data Execution Prevention
Data Execution Prevention (DEP) is a crucial protection mechanism in cybersecurity that helps defend against various types of attacks and vulnerabilities. DEP works by preventing the execution of malicious code in the memory of a system. By controlling both hardware and software, DEP reduces the risk of data and system exploitation, making it an essential component of overall security.
DEP operates by marking certain areas of memory as non-executable, preventing the execution of code in those regions. This effectively blocks potential attacks that rely on buffer overflow or other memory-based vulnerabilities. By limiting the ability of malware to run arbitrary code, DEP significantly reduces the chances of successful system compromise.
To implement DEP, both hardware and software support is required. The hardware part involves the use of a processor capable of supporting DEP. Modern processors often include this feature, enabling the enforcement of memory protection. On the software side, the operating system and individual applications need to be properly configured to utilize DEP. This includes enabling DEP at the system level and ensuring that all software components are compatible with DEP’s requirements.
While DEP is effective in preventing code execution in memory, it is not a bulletproof solution. Sophisticated malware and attacks can bypass DEP by exploiting other vulnerabilities or using advanced techniques. Therefore, DEP should be used in conjunction with other security measures, such as antivirus software, firewalls, and regular system updates, to create a comprehensive defense against threats.
When implementing DEP, it is crucial to consider both the benefits and potential drawbacks. While DEP enhances security, it can also result in compatibility issues with certain software applications that may require the execution of code in non-standard areas of memory. Careful testing and evaluation should be conducted to ensure that DEP does not negatively impact essential software functionality.
In conclusion, implementing Data Execution Prevention is an important step towards enhancing the security of a system. By preventing the execution of malicious code in memory, DEP helps mitigate various threats and vulnerabilities. While it is not a foolproof solution, when combined with other security measures, DEP significantly improves the overall cybersecurity posture of a system.
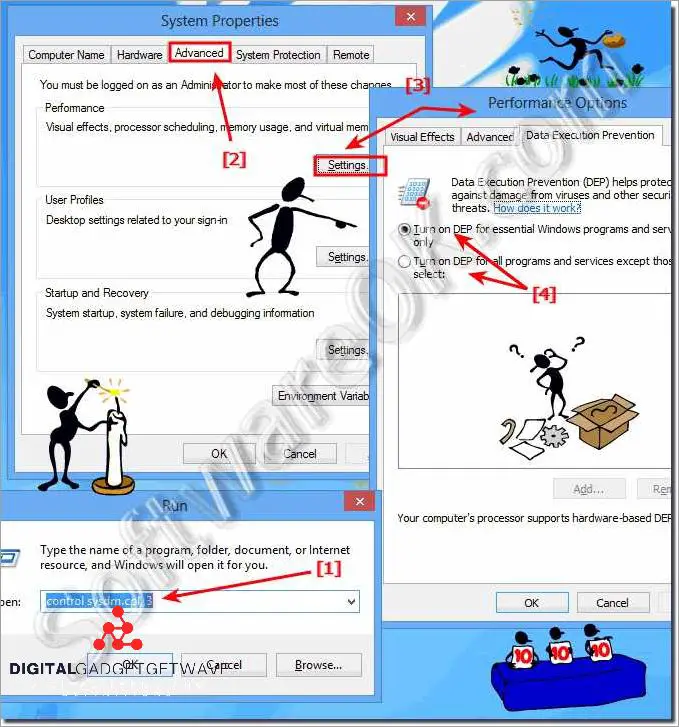
Activating Data Execution Prevention
Data Execution Prevention (DEP) is a vital feature that provides an additional layer of protection for computer systems against certain types of attacks and malware. By activating DEP, you enable the system to prevent the execution of malicious code in protected memory areas.
DEP serves as an important defense mechanism against buffer overflow attacks, which are among the most common types of threats in the cybersecurity landscape. This technology detects and stops attempts to execute code from non-executable memory regions, effectively preventing the exploitation of system vulnerabilities.
Activating DEP involves both hardware and software controls. Firstly, the hardware must support the necessary technology, such as the NX (No eXecute) or XD (eXecute Disable) bit, which determines the executable or non-executable status of a memory page. Most modern processors have this capability.
Once the hardware support is in place, DEP can be enabled through the operating system or specific software. The configuration settings for DEP allow you to enable protection for essential Windows programs only, or you can choose to enable it for all programs and services.
The activation of DEP significantly reduces the risk of successful execution of malware or other malicious code on your system. However, it is important to note that DEP is not the only safeguard against cyber threats. It should be used in conjunction with other security measures, such as regular software updates, strong passwords, and the use of reputable antivirus software.
In conclusion, activating Data Execution Prevention is an essential step in enhancing the security of your computer system. By leveraging the hardware and software controls provided by DEP, you can defend against various exploits and minimize the potential risks associated with executing malicious code. It is crucial to prioritize cybersecurity measures to safeguard your data and maintain the integrity of your system.
Compatibility Considerations
When implementing Data Execution Prevention (DEP) technology, it is important to consider compatibility issues that may arise. DEP works by preventing the execution of data in certain areas of memory, which can have implications for software and hardware compatibility.
Some older software, especially legacy applications, may not be compatible with DEP. These applications may have code that violates DEP’s restrictions on executing data from certain memory locations. In such cases, DEP may need to be disabled for the software to function properly. It is important to carefully evaluate the risks and benefits before disabling DEP, as it can leave the system vulnerable to various security threats.
Additionally, compatibility issues can also arise with certain hardware and device drivers. Some older hardware may not support the necessary features and protections required by DEP. Incompatible drivers can cause system instability and potentially expose the system to malicious attacks.
It is crucial to keep software and operating systems up to date to ensure compatibility with DEP. Regular updates and patches from software vendors often address compatibility issues and provide necessary improvements to DEP support.
Furthermore, it is important to note that while DEP provides an effective defense against many types of attacks, it is not a foolproof solution. Advanced malware and exploits can still find vulnerabilities and bypass DEP protection. Therefore, it is essential to combine DEP with other security measures, such as anti-malware software, to provide a comprehensive protection for the system.
In conclusion, implementing DEP for enhanced security involves careful consideration of compatibility issues. Compatibility problems with software, hardware, and drivers may arise, which may require disabling or updating DEP to ensure system stability and security. It is important to regularly update software and combine DEP with other security measures to mitigate the risk of attacks and protect against evolving threats.
Data Execution Prevention Best Practices
Data Execution Prevention (DEP) is a technology that helps protect a system from threats such as malware. By preventing the execution of data in certain memory regions, DEP acts as a defense mechanism against various types of attacks that exploit vulnerabilities in software.
1. Enable DEP: The first and most important best practice is to ensure that DEP is enabled on your system. This can typically be done through the system settings or BIOS configuration. Enabling DEP will provide an additional layer of protection against memory-based attacks.
2. Keep hardware and software up to date: It is important to regularly update your system’s hardware drivers and software applications. These updates often include security patches that address vulnerabilities and enhance the overall security of the system, including DEP functionality.
3. Use comprehensive security solutions: Implementing an effective cybersecurity defense strategy is crucial for protecting your system. This includes using a reliable antivirus software, firewall, and other security solutions that can help detect and prevent malware infections that may circumvent DEP.
4. Practice safe browsing habits: Many malware and exploit attacks are delivered through malicious websites, phishing emails, and other online sources. To minimize the risk of encountering such threats, it’s important to exercise caution while browsing the internet and avoid clicking on suspicious links or downloading files from untrusted sources.
5. Regularly backup your data: Even with protective measures in place, there is always a chance of a successful attack. Therefore, it is essential to regularly backup your important data. This will ensure that you have a copy of your data in case it becomes compromised or inaccessible due to a malware attack or other incident.
6. Educate yourself and your users: Knowledge about common cybersecurity threats and best practices is crucial. It’s important to stay informed about the latest security trends and educate yourself and your users on how to recognize and avoid potential threats. This can help mitigate the risks associated with malware attacks that may bypass DEP protection.
7. Implement buffer overflow protections: Buffer overflow vulnerabilities are often targeted by malicious attackers. By implementing software controls, such as stack canaries, bounds checking, and address space layout randomization (ASLR), you can make it more difficult for attackers to exploit these vulnerabilities and bypass DEP.
8. Monitor for suspicious activities: Implementing a robust security monitoring system can help detect any unusual activity that may indicate a potential malware attack. Regularly review logs and alerts generated by your security solutions to identify any suspicious patterns or behaviors that may require further investigation and response.
In conclusion, implementing the best practices for Data Execution Prevention can significantly enhance the security of your system. By enabling DEP, keeping your hardware and software up to date, using comprehensive security solutions, and practicing safe browsing habits, you can effectively protect your system from memory-based attacks and malware threats.
Maintaining up-to-date Operating Systems and Software
Keeping operating systems and software up to date is a crucial step in ensuring the protection of data and preventing potential attacks. It is essential to regularly update both the operating system and software applications to mitigate any vulnerabilities that could be exploited by attackers.
Operating system updates often include security patches and bug fixes that address known vulnerabilities or weaknesses in the software. These updates enhance the overall security and stability of the system, reducing the risk of unauthorized access or data breaches. Additionally, updated operating systems provide improved features and functionality that can help defend against evolving cyber threats.
Software applications, especially those that handle sensitive data or have network connectivity, should also be kept up to date. Software updates often address known security vulnerabilities that could be exploited by attackers to gain unauthorized access or execute malicious code. By regularly updating software applications, users can ensure that they have the latest security patches and features to defend against emerging threats.
Failure to keep operating systems and software up to date puts the system at risk of being compromised by various types of attacks. Attackers can exploit vulnerabilities in outdated software to gain control over the system or manipulate sensitive data. Outdated software is more susceptible to malware infections, as new malware variants are designed to take advantage of known vulnerabilities. By keeping the software up to date, users can utilize the latest protection technology and significantly reduce the risk of falling victim to cyber threats.
Regularly updating operating systems and software is a fundamental aspect of cybersecurity, serving as a crucial defense against potential attacks. It ensures the system has the most recent security patches, bug fixes, and features to protect against both known and emerging threats. Maintaining up-to-date software also demonstrates a proactive approach to cybersecurity and showcases a commitment to safeguarding data and maintaining the integrity of the system.
Regularly Updating Hardware Drivers
Regularly updating hardware drivers is an essential aspect of ensuring the execution and protection of data in modern cybersecurity. Hardware drivers, also known as device drivers, are software programs that allow hardware devices to communicate with the operating system and perform specific functions. By updating these drivers, users can enhance the security and performance of their systems, minimizing the risk of exploitation by malware and other cyber threats.
Outdated hardware drivers can pose a serious security threat, as they may contain vulnerabilities that cyber attackers can leverage to gain unauthorized access to a system. These exploits can compromise a user’s control over their data, potentially leading to loss or theft of sensitive information. By regularly updating hardware drivers, users can take advantage of the latest security patches and bug fixes, bolstering the defense against potential attacks.
One of the key areas where regularly updating hardware drivers can have a significant impact on cybersecurity is memory management. Drivers play a crucial role in managing the system’s memory, including the buffer, which is a temporary storage area for data. Outdated drivers may not efficiently control the buffer, leaving it vulnerable to buffer overflow attacks. These attacks involve writing data beyond the allocated memory space and can be exploited by cybercriminals to inject malicious code and execute arbitrary commands.
By keeping hardware drivers up to date, users can improve the prevention of buffer overflow risks. Updated drivers often include enhancements that strengthen the buffer’s defense mechanisms, making it more difficult for attackers to exploit vulnerabilities. Additionally, regular updates can help mitigate compatibility issues between the hardware and software components of a system, allowing for improved overall system stability and security.
Overall, regularly updating hardware drivers is a crucial part of maintaining a secure and protected system. By staying vigilant and keeping drivers up to date, users can reduce the potential risk of exploitation, strengthen the defense against cyber threats, and ensure the optimized execution and protection of their valuable data.
Configuring Exception Settings
The hardware-level control system known as Data Execution Prevention (DEP) is a crucial technology in the defense against security threats such as malware attacks. However, it is essential to configure the exception settings to ensure the optimal protection of the system.
DEP works by preventing the execution of code in specific memory regions that are reserved for data storage. By doing so, it mitigates the risk of buffer overflow vulnerabilities and the exploitation of software weaknesses. However, there may be instances where certain legitimate applications require the execution of code from data memory. In such cases, configuring exception settings is necessary to ensure the proper functioning of these applications.
Configuring exception settings involves identifying the specific executable files or processes that require exceptions to DEP. This can be done by either adding individual files or specifying entire programs to the exception list. It is crucial to exercise caution when adding exceptions, as this can potentially introduce security vulnerabilities. Therefore, it is recommended to only add exceptions for trusted and verified applications.
To configure exception settings effectively, it is advisable to consult the system documentation or seek guidance from cybersecurity professionals. They can provide insight into the specific requirements of the system and help identify potential risks or threats associated with the exception settings. Regularly reviewing and updating these settings is also essential to keep up with the evolving nature of cybersecurity.
In summary, configuring exception settings for DEP is a vital aspect of system security. It allows for the execution of code from data memory when necessary while still providing protection against malicious attacks. By following best practices and seeking professional guidance, the system can benefit from the enhanced defense offered by DEP while minimizing the risk of exploitation.
FAQ about topic “Data Execution Prevention: What You Need to Know”
What is Data Execution Prevention (DEP)?
Data Execution Prevention (DEP) is a security feature in operating systems that helps prevent malicious code from running in memory spaces where it should not be executed.
How does Data Execution Prevention work?
Data Execution Prevention works by marking certain memory locations as non-executable, preventing them from being used to execute malicious code. It can also detect and prevent certain types of code injection attacks.
Is Data Execution Prevention enabled by default?
Yes, Data Execution Prevention is typically enabled by default in modern operating systems. However, it can be disabled or configured on a per-program basis.
What are the benefits of using Data Execution Prevention?
Data Execution Prevention can help protect against a wide range of security vulnerabilities, including buffer overflows and certain types of code injection attacks. It can also help improve the stability and reliability of the operating system by preventing the execution of malicious or poorly written code.
Can Data Execution Prevention interfere with legitimate software?
While Data Execution Prevention is designed to prevent the execution of malicious code, it can sometimes interfere with legitimate software. In such cases, it may be necessary to configure DEP exceptions for specific programs to prevent compatibility issues.


