
Buffer overflow (BOF) is a memory vulnerability that can be exploited in software systems. It occurs when a program tries to store more data in a buffer than it can handle, causing the excess data to overflow into adjacent memory locations. This can lead to unpredictable behavior, including crashes, system instability, or even the execution of malicious code.
The buffer overflow flaw primarily affects software systems that do not have proper memory protection mechanisms in place. When a buffer overflow occurs, an attacker can gain control over the system by overwriting important data stored in memory, such as return addresses or function pointers. This allows them to redirect the program’s execution to code of their choice, potentially enabling them to carry out unauthorized actions or gain unauthorized access.
The underlying cause of buffer overflow vulnerabilities is often poor coding practices, such as not properly validating input or not checking the size of data being copied into a buffer. Attackers can exploit these vulnerabilities by crafting input that exceeds the size of the buffer, leading to an overflow. This can be done through various means, such as user input, network traffic, or specially crafted files.
It is important for software developers to understand and mitigate the buffer overflow flaw to ensure the security of their systems. This can be achieved through secure coding practices, such as input validation and proper use of buffer size checks. Additionally, implementing memory protection mechanisms, like address space layout randomization (ASLR) or stack canaries, can help prevent attackers from successfully exploiting buffer overflow vulnerabilities.
Contents
- 1 Understanding Buffer Overflow:
- 2 Exploiting Buffer Overflow:
- 3 Preventing Buffer Overflow:
- 4 Buffer Overflow in Recent Attacks:
- 5 FAQ about topic “Understanding BOF: An Introduction to the Buffer Overflow Vulnerability”
- 6 What is a buffer overflow flaw?
- 7 How does a buffer overflow attack work?
- 8 What are the potential consequences of a buffer overflow vulnerability?
- 9 How can software developers prevent buffer overflow vulnerabilities?
- 10 Why is it important for system administrators to stay updated on buffer overflow vulnerabilities?
Understanding Buffer Overflow:
Buffer overflow is a common software vulnerability that can be exploited by hackers to gain control over a system. It occurs when a program or software fails to properly limit the amount of data that can be written into a buffer, allowing an overflow of data to overwrite adjacent memory.
This vulnerability can be maliciously exploited to inject and execute arbitrary code, also known as a shellcode, with the privileges of the affected software. By overwriting adjacent memory areas, hackers can gain control of the execution flow and redirect it to their malicious code.
The buffer overflow vulnerability poses a significant threat to system security, as it can be used to bypass security measures and gain unauthorized access. It is commonly found in software that handles input from external sources, such as network protocols or file formats.
To protect against buffer overflow attacks, developers can implement various security measures. These include input validation and sanitization techniques that ensure only valid and expected data is accepted by the system. Additionally, the use of secure coding practices and regular software updates can help mitigate the risk of buffer overflow vulnerabilities.
Understanding buffer overflow is essential for both software developers and security professionals. By identifying and addressing potential buffer overflow flaws, organizations can enhance the security of their systems and protect against malicious attacks.
Overall, buffer overflow is a serious vulnerability that can allow hackers to gain control over a system and execute arbitrary code. It is crucial to understand the basics of buffer overflow and take appropriate measures to protect against this type of attack.
Definition and Explanation
The buffer overflow (BOF) is a vulnerability in computer systems that occur when a buffer, a temporary storage area used to store data, exceeds its allocated size and overflows into adjacent memory spaces. This flaw can be exploited by attackers to inject and execute malicious code, potentially compromising the security of the system.
In a binary software, the memory is organized into various sections, including the stack. The stack is a region of memory used to store local variables and function call information. When a buffer overflow occurs, it can overwrite critical data in the stack, such as return addresses, which can be hijacked to redirect the control flow of the program.
Attackers use buffer overflow as a means to inject and execute their own code, known as shellcode, which grants them unauthorized access and control over the compromised system. This allows them to perform various malicious activities, including stealing sensitive data, corrupting files, or launching further attacks.
Buffer overflow vulnerabilities can be found in software due to coding errors or poor memory management practices. To mitigate such vulnerabilities, developers have to implement proper input validation and bounds checking to ensure that input data will not overflow the buffer. Additionally, operating systems and security software can employ techniques like address space layout randomization (ASLR) and stack canaries to provide further protection against buffer overflow exploits.
How Buffer Overflow Works
A buffer overflow is a type of vulnerability that occurs when a program writes more data to a buffer than it can hold. In computer programming, a buffer is a temporary storage area used to hold data. When the buffer is overflowed, the excess data can overwrite adjacent memory areas, including the stack, where the return address of a function is stored.
Exploiting a buffer overflow vulnerability typically involves injecting malicious code into the program’s memory. This can be accomplished by overwriting the return address of a function with the address of the injected code. When the function returns, instead of going back to the original execution point, the program jumps to the injected code, allowing the attacker to gain control of the system.
Buffer overflow attacks are a major concern in computer security, as they can lead to arbitrary code execution. If an attacker is able to control the execution of a program, they can potentially gain unauthorized access to sensitive information, modify data, or execute malicious commands.
To protect against buffer overflow attacks, software developers can implement various security measures. These include input validation, which ensures that user-supplied data does not exceed the available buffer size. Additionally, stack canaries can be used to detect buffer overflows by placing a random value before the return address on the stack. If this value is modified, it indicates a buffer overflow has occurred.
It’s important for software developers and security professionals to be aware of the risks associated with buffer overflow vulnerabilities and take appropriate measures to mitigate them. Regular security audits and code reviews can help identify and fix potential buffer overflow flaws before they can be exploited by hackers.
Common Vulnerable Applications
Buffer overflow (BOF) is a common vulnerability in which an application does not properly check the size of the data it receives, allowing an attacker to overflow the allocated memory buffer. This can lead to a stack corruption, giving the attacker control over the execution of the program.
There are various types of common vulnerable applications that can be targeted through buffer overflow attacks. These applications include web servers, email clients, operating systems, and even mobile applications. Any program that reads input from a user or external source without sufficient bounds checking is potentially vulnerable.
One common way to exploit this vulnerability is by injecting malicious code into the program’s stack. The attacker carefully crafts a payload that will overwrite the return address of a function with the address of the injected code. This allows the attacker to gain control over the program’s execution and potentially execute arbitrary commands on the host system.
It is important to note that buffer overflow attacks can be prevented by implementing proper input validation and memory protections. Applications should always validate the length of input data and ensure that it does not exceed the allocated buffer size. Additionally, developers should use secure coding practices, such as using safe string functions and disabling certain risky language features.
In conclusion, understanding the basics of buffer overflow vulnerabilities and common vulnerable applications is crucial for system administrators and developers alike. By being aware of these security risks, organizations can take necessary measures to protect their systems from potential exploits and maintain the integrity of their data.
Exploiting Buffer Overflow:
A buffer overflow is a vulnerability in software where the buffer, a designated area of memory, is overflowed with more data than it can hold. This can lead to the execution of malicious code or the hijacking of a system. To exploit a buffer overflow, an attacker typically crafts input data that is larger than the buffer’s capacity, causing the excess data to overflow into adjacent memory regions.
One common way to exploit buffer overflow is by injecting shellcode into the buffer. Shellcode is a small piece of malicious code that an attacker wants to execute on the compromised system. By carefully crafting the input data to trigger a buffer overflow and redirecting the control flow, the attacker can execute their shellcode and gain control over the system.
Exploiting a buffer overflow can be particularly dangerous because it allows an attacker to bypass the protection mechanisms implemented in the software. These protections are designed to prevent buffer overflows and malicious code execution. However, if the vulnerability is successfully exploited, the attacker can override these protections and gain control over the execution flow of the program.
It is important for software developers to be aware of buffer overflow vulnerabilities and to implement proper security measures to prevent such attacks. This can include properly validating input data, limiting the size of buffers, and implementing techniques such as address space layout randomization (ASLR) and stack canaries to make exploitation more difficult.
In summary, buffer overflow is a serious vulnerability in software that can be exploited to execute malicious code. It bypasses the protection mechanisms in place, giving an attacker control over the system. It is crucial for software developers to understand and mitigate these vulnerabilities to ensure the security of their applications and protect against potential hacks and attacks.
Exploitation Techniques

In the context of buffer overflow (BOF) vulnerabilities, exploitation techniques refer to the methods used by malicious individuals to take advantage of software flaws and gain unauthorized control over a system.
One common exploitation technique involves manipulating the buffer overflow vulnerability to overwrite the return address of a function call. By carefully crafting a malicious string that exceeds the bounds of a buffer, an attacker can overwrite the return address on the stack with the address of their own code, typically referred to as shellcode.
Shellcode is a small piece of code that is injected into the targeted system’s memory by the attacker. This code enables the attacker to execute arbitrary commands and gain control over the compromised system.
Another exploitation technique involves exploiting the stack-based buffer overflow vulnerability to execute arbitrary code. By modifying the contents of the stack frame, an attacker can redirect the program’s control flow and execute their own malicious code.
Exploitation techniques may also involve leveraging other vulnerabilities in the software or the underlying system to achieve the desired control or privilege escalation. This can include exploiting memory corruption vulnerabilities, such as heap overflows or integer overflows, to gain control over the execution flow of the program.
To protect against exploitation, various mitigation techniques have been developed, such as stack canaries, address space layout randomization (ASLR), and data execution prevention (DEP). These techniques aim to detect or prevent the successful execution of malicious code by detecting buffer overflows or making it more difficult for attackers to predict memory addresses and execute arbitrary code.
Overall, understanding exploitation techniques is crucial for both software developers and security professionals in order to effectively protect systems from buffer overflow vulnerabilities and potential attacks.
Remote Code Execution
Remote Code Execution (RCE) is a software vulnerability that allows an attacker to execute malicious code or commands on a target system remotely. This type of attack is often achieved by exploiting a buffer overflow (BOF) vulnerability.
In a buffer overflow attack, the attacker takes advantage of a flaw in the system’s memory protection to overwrite a buffer, usually in stack, with excessive data. This excessive data can include a shellcode, which is a piece of code that the attacker wants to execute on the target system.
Once the buffer overflow occurs and the attacker successfully injects the malicious code into the system’s memory, they gain control over the execution flow. With this control, they can execute their own commands, potentially compromising the entire system.
Security measures such as stack canaries and ASLR (Address Space Layout Randomization) are often implemented to protect against buffer overflow attacks and prevent buffer overflow vulnerabilities. However, if these protections are not properly implemented or if a new vulnerability is discovered, remote code execution attacks can still occur.
Remote code execution vulnerabilities are a serious threat to the security of software systems. Therefore, it is important for developers and system administrators to regularly update and patch their systems to protect against these types of attacks. It is also crucial for organizations to have robust security measures in place to detect and mitigate any potential vulnerabilities before they are exploited by malicious attackers.
Potential Consequences

The buffer overflow flaw, also known as BOF, is a serious security vulnerability that can have severe consequences if exploited by malicious actors. By taking advantage of the buffer overflow, an attacker can gain control over a system and execute arbitrary code.
This can lead to a variety of potential consequences, including unauthorized access to sensitive data, manipulation of system files, disruption of system operations, and even complete compromise of the affected system’s security.
When a buffer overflow occurs, it allows an attacker to overwrite crucial parts of the memory, such as return addresses or function pointers, leading to a loss of control over the system’s execution flow. This loss of control can enable the execution of malicious code or the injection of shellcode, which can further exploit the system’s vulnerabilities.
Without proper protection mechanisms in place, buffer overflow attacks can bypass security measures and gain access to the privileged areas of the system. This puts sensitive information, like passwords or financial data, at risk of being compromised.
Furthermore, buffer overflows can be used to exploit software vulnerabilities and weaknesses, allowing attackers to take advantage of flaws in the code and gain unauthorized access to the system. This can lead to the escalation of privileges, where attackers can execute arbitrary commands with elevated permissions.
To mitigate the potential consequences of buffer overflow attacks, developers and software vendors need to implement strong security practices and regularly update their software to address any discovered vulnerabilities. Additionally, organizations should employ intrusion detection systems and regular security audits to identify and prevent buffer overflow attacks before they can cause damage.
Preventing Buffer Overflow:
Buffer overflow is a serious security vulnerability that can be exploited by malicious hackers to gain unauthorized access or execute arbitrary code on a system. To prevent buffer overflow attacks, various software protection mechanisms can be implemented.
One of the key approaches to prevent buffer overflow is to incorporate strong input validation and bounds checking in the code. By ensuring that the input data is properly validated and that buffer sizes are checked before copying data, developers can significantly reduce the risk of buffer overflow vulnerabilities.
Another important prevention technique is the use of code memory protection mechanisms such as Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP). ASLR randomizes the memory layout of a process, making it difficult for an attacker to predict the location of the stack or any injected malicious code. DEP prevents the execution of code stored in data memory, effectively blocking the execution of shellcode injected through a buffer overflow.
Furthermore, developers can use secure coding practices and follow coding guidelines such as the CERT C Coding Standard, which provide specific recommendations for avoiding buffer overflow vulnerabilities. These guidelines include recommendations for proper use of library functions, avoiding unsafe string manipulation functions, and using safer alternatives like snprintf instead of sprintf.
It is also essential to regularly update and patch software to ensure that any known buffer overflow vulnerabilities are fixed. Keeping software up to date helps to mitigate the risk of buffer overflow attacks by applying security patches that address specific vulnerabilities.
Overall, preventing buffer overflow requires a multi-layered approach that includes secure coding practices, input validation, memory protection mechanisms, and regular software updates. By implementing these measures, developers and system administrators can strengthen the security of their systems and protect against buffer overflow attacks.
Code Review and Input Validation
In the realm of software security, code review and input validation are crucial measures for protecting against vulnerabilities such as buffer overflow (bof) exploits. A buffer overflow occurs when a program tries to store more data in a buffer than it can handle, resulting in memory corruption and potential security breaches.
To identify and mitigate the risk of buffer overflow vulnerabilities, a thorough code review must be conducted. This involves scrutinizing the codebase for potential weak points and security flaws that could be exploited. By carefully examining the code, developers can identify areas where input validation is lacking and introduce appropriate safeguards.
Input validation plays a pivotal role in preventing buffer overflow vulnerabilities. It involves verifying the data provided by users or external sources before processing or storing it. By enforcing strict limits on the size and type of input accepted by the software, developers can ensure that the system remains secure and resistant to bof attacks.
One common technique to handle buffer overflow vulnerabilities is to implement proper boundary checking. This involves analyzing the maximum memory allocated for a buffer and ensuring that the input data does not exceed this limit. Additionally, developers can employ techniques such as input sanitization and validation routines to detect and filter out malicious content, preventing the execution of malicious shellcode.
Another layer of protection against buffer overflow attacks is the implementation of stack cookies or canaries. These security mechanisms add an extra check to the system’s stack to detect and prevent buffer overflows. The stack cookie is a random value inserted between the buffer and the return address, and it is checked before a function returns. If the value has been modified, indicating a potential overflow, the execution is terminated.
In summary, code review and input validation are critical steps in preventing buffer overflow vulnerabilities in software systems. By conducting rigorous code reviews and implementing robust input validation mechanisms, developers can minimize the risk of bof attacks and ensure the security and stability of their systems.
Stack Canaries and Address Space Layout Randomization
The stack canaries and address space layout randomization (ASLR) are two important techniques used in software systems to protect against buffer overflow vulnerabilities and prevent malicious attacks.
Buffer overflow is a common vulnerability in software systems that can be exploited by attackers. This occurs when the amount of data written to a buffer exceeds its fixed size, causing the excess data to overflow into adjacent memory locations. By carefully crafting input data, attackers can manipulate the overflow to execute arbitrary code, such as shellcode, and gain unauthorized control of the system.
To mitigate these buffer overflow attacks, stack canaries are introduced as a protection mechanism. A stack canary is a randomly generated value that is placed between the local variables and the return address on the stack. This value is checked before the function returns to ensure that it has not been modified by an attacker. If the stack canary has been modified, indicating a buffer overflow attack, the program terminates before any malicious code can be executed.
In addition to stack canaries, address space layout randomization (ASLR) is another technique used to enhance the security of software systems. ASLR randomizes the memory layout of a program, including the locations of the stack, heap, and libraries, making it more difficult for attackers to exploit buffer overflow vulnerabilities. By randomizing the memory layout, the addresses of critical functions and data are different every time the program is executed, making it harder for attackers to predict and exploit them.
By combining stack canaries and ASLR, software systems can significantly improve their protection against buffer overflow attacks. The introduction of stack canaries adds an additional layer of defense by detecting and terminating any malicious attempts to modify the stack, while ASLR adds variability to the memory layout, making it more difficult for attackers to locate and exploit vulnerable code. These protection mechanisms contribute to the overall security and integrity of software systems, helping to reduce the risk of unauthorized access and compromise.
Best Practices for Software Development
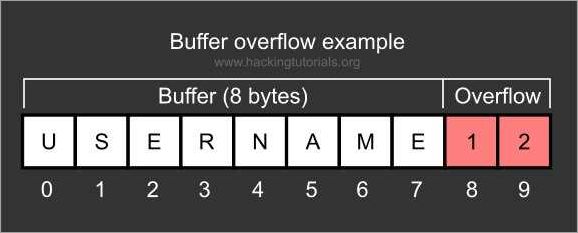
Buffer overflow vulnerability: One of the major security risks in software development is the buffer overflow vulnerability. This occurs when a buffer, which is a temporary storage area for data, is filled with more data than it can hold. As a result, the excess data can overflow into adjacent memory locations, potentially leading to the execution of malicious code.
Control execution: To protect against buffer overflow attacks, it is crucial to implement proper control over the execution of code. This includes validating and sanitizing user input, ensuring that buffers are appropriately sized, and using secure coding practices to prevent any unintended memory manipulation.
Shellcode: A common vector for buffer overflow attacks is the injection of shellcode, which is a small piece of malicious code designed to exploit vulnerabilities in the target system. Developers should carefully review and test their code to identify and fix any potential areas where shellcode injection could occur.
Memory protection: Implementing memory protection mechanisms is essential for preventing buffer overflow exploits. Techniques such as address space layout randomization (ASLR) and data execution prevention (DEP) can make it more challenging for attackers to exploit vulnerabilities in the software.
Binary code review: Regular code reviews, including reviewing the binary code, can help identify potential security vulnerabilities. Developers should pay particular attention to any function calls that involve the manipulation of buffers and ensure that proper boundary checks are in place.
Security patches and updates: Keeping software up to date with the latest security patches is crucial in maintaining a secure system. Developers should actively monitor for any reported vulnerabilities or exploits and promptly release updates to address these issues.
Secure development frameworks and libraries: Utilizing secure development frameworks and libraries can help mitigate the risk of buffer overflow vulnerabilities. These frameworks often provide built-in security features and follow best practices, making it easier for developers to create secure software.
Hacker mindset: Developers should adopt a hacker mindset, thinking of ways to exploit their own code to identify potential vulnerabilities. This proactive approach can help uncover weaknesses and strengthen the overall security of the software during the development process.
Training and education: Providing developers with regular training and education on secure coding practices and the latest security threats is essential. This enables them to stay up to date with emerging attack techniques and implement the necessary protections in their software.
Defense in depth: Finally, applying a defense-in-depth strategy is crucial for securing software against buffer overflow attacks. This involves implementing multiple layers of security controls, including network-level protections, host-based firewalls, and intrusion detection systems, in addition to secure software development practices.
Buffer Overflow in Recent Attacks:
The buffer overflow flaw is a serious security vulnerability that can be exploited to gain control over a computer system. In recent years, this vulnerability has been extensively used in various attacks, highlighting the importance of understanding and mitigating this issue.
In a buffer overflow attack, a malicious individual takes advantage of a software flaw that allows them to overwrite a buffer in the computer’s memory. By inserting more data than the buffer can handle, they can overflow it and overwrite adjacent memory areas, potentially altering the flow of execution and gaining control over the system.
These attacks often involve the use of shellcode, a small piece of malicious code that is injected into the system’s memory. Once the buffer overflow occurs, the attacker can redirect the execution flow to the shellcode, which then executes arbitrary commands or launches a more substantial attack.
Buffer overflow attacks can target various software components, including operating systems, network protocols, and applications. Recent attacks have shown that even widely-used software can be vulnerable, highlighting the need for robust protection mechanisms and regular security updates.
Mitigating buffer overflow vulnerabilities involves implementing various security measures. These can include using code analysis tools to identify potential buffer overflow flaws, implementing stack protection mechanisms, and regularly patching software to address known vulnerabilities. Additionally, developers should adopt secure coding practices to minimize the potential for such vulnerabilities in the first place.
Overall, the prevalence of buffer overflow attacks in recent years has emphasized the importance of understanding and addressing this security flaw. By implementing appropriate protection measures and staying vigilant against new vulnerabilities, system administrators and developers can help minimize the risk of being hacked through buffer overflow attacks.
Notable Attacks and Breaches
Buffer overflow flaws have been exploited in several notable attacks and breaches, highlighting the serious security implications of this vulnerability. One such attack is the Code Red worm that targeted Microsoft IIS web servers in 2001. By exploiting a buffer overflow vulnerability in the Indexing Service DLL, the worm was able to spread rapidly and deface websites.
Another notorious incident involving a buffer overflow exploit is the 2014 Heartbleed bug. This vulnerability affected the OpenSSL cryptographic software library, allowing malicious actors to steal sensitive information, such as passwords and private keys, from servers. The widespread impact of Heartbleed highlighted the need for robust security measures and regular software updates.
In 2003, the SQL Slammer worm exploited a buffer overflow vulnerability in Microsoft SQL Server, causing a denial-of-service on internet hosts worldwide. This fast-spreading worm overloaded networks and disrupted critical services, demonstrating the potential havoc that can be wreaked through a simple software vulnerability.
One of the most famous breaches involving a buffer overflow exploit was the 1988 internet worm created by Robert Tappan Morris. By exploiting a buffer overflow flaw in the fingerd service, the worm infected thousands of computers connected to the ARPANET, slowing down the internet and raising awareness about the importance of computer security.
Buffer overflow vulnerabilities continue to be a significant concern in software security. Whether it’s a small-scale hack or a large-scale attack, the potential for unauthorized code execution or control of a system through a bof flaw makes it crucial for software developers and system administrators to prioritize protections against such exploits. Regular security audits, software updates, and secure coding practices are essential to mitigate the risks associated with buffer overflow flaws.
Lessons Learned and Countermeasures
Buffer overflow attacks have proven to be a significant security flaw in software systems. Through the exploitation of this vulnerability, attackers can gain unauthorized access to a system or execute malicious code, compromising the integrity and confidentiality of the system. Understanding the lessons learned from past exploits is crucial in developing effective countermeasures to mitigate the risk of buffer overflow attacks.
Lesson 1: Sanitization of input data. One of the key steps in preventing buffer overflow attacks is to properly sanitize the input data. This involves validating and filtering user input to ensure it does not contain any malicious code or unexpected characters that can lead to buffer overflow. Employing input validation techniques such as length and format checks can greatly enhance the security of software systems.
Lesson 2: Implement stack protection mechanisms. The stack is a critical component involved in the execution of software code. By implementing protection mechanisms, such as stack canaries or stack smashing protection (SSP), the system can detect and prevent buffer overflows by monitoring the integrity of the stack variables. This adds an additional layer of defense against buffer overflow attacks.
Lesson 3: Use secure coding practices. Developing software with security in mind is essential in preventing buffer overflow vulnerabilities. By following secure coding practices, such as checking array boundaries, avoiding unsafe functions, and regularly updating software libraries, programmers can significantly reduce the risk of buffer overflow exploits.
Lesson 4: Regularly apply software patches and updates. The discovery of new vulnerabilities and exploits is an ongoing process. To stay ahead of attackers, it is crucial to regularly apply software patches and updates provided by software vendors. These updates often include security fixes that address known vulnerabilities, including those related to buffer overflows.
Lesson 5: Use advanced memory management techniques. Modern software development practices incorporate advanced memory management techniques, such as Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP). These techniques make it harder for attackers to predict memory addresses and execute arbitrary code, which can help mitigate the risk of buffer overflow attacks.
By implementing these countermeasures and lessons learned, software developers and system administrators can greatly enhance the security of their systems and protect against the devastating effects of buffer overflow attacks.
The Future of Buffer Overflow Flaws

In the ever-evolving field of computer security, buffer overflow vulnerabilities continue to be a significant concern. A buffer overflow occurs when a program writes data to a buffer and exceeds its allocated size, resulting in the overflow of data into adjacent memory locations. This can lead to the corruption of data, the execution of malicious code, and even the compromise of a system’s control flow.
As software systems become more complex and intricate, the likelihood of buffer overflow vulnerabilities increases. The reliance on dynamic memory allocation and the lack of proper input validation make these flaws more prevalent and exploitable. Hackers are constantly searching for ways to exploit these vulnerabilities, using techniques such as stack smashing and return-oriented programming to gain unauthorized access and bypass security measures.
To mitigate the risk posed by buffer overflow flaws, it is essential to focus on proactive measures. Software developers should prioritize building robust code that incorporates input validation and boundary checks to prevent buffer overflows from occurring. Additionally, implementing security mechanisms such as Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP) can make it more challenging for attackers to execute shellcode or inject malicious code.
The future of buffer overflow flaws also lies in the advancement of vulnerability exploitation techniques. With the rapid growth of machine learning and artificial intelligence, hackers may develop more sophisticated and automated tools to identify and exploit buffer overflow vulnerabilities. This highlights the need for constant research and innovation in the field of cybersecurity to stay one step ahead of attackers.
As technology evolves, so do the methods employed by malicious actors. The increasing adoption of Internet of Things (IoT) devices and the proliferation of embedded systems in various industries present new challenges and potential vulnerabilities for buffer overflow attacks. It is crucial to incorporate strong security practices during the development and deployment of these devices and systems to protect against buffer overflow flaws.
In conclusion, buffer overflow vulnerabilities remain a significant concern in the realm of computer security. As software systems become more complex, it is imperative to adopt proactive measures to prevent and mitigate these flaws. By prioritizing secure coding practices, implementing robust security mechanisms, and staying up-to-date with the latest research, we can enhance the protection against buffer overflow attacks and ensure the security and integrity of our systems and data.
FAQ about topic “Understanding BOF: An Introduction to the Buffer Overflow Vulnerability”
What is a buffer overflow flaw?
A buffer overflow flaw is a vulnerability in software where an attacker can overwrite a buffer’s boundary and overwrite adjacent memory, leading to unpredictable behavior, crashes, and potential security breaches.
How does a buffer overflow attack work?
In a buffer overflow attack, an attacker intentionally inputs more data into a buffer than it can handle, causing the excess data to overwrite adjacent memory locations. By carefully constructing the input, an attacker can overwrite important data, such as return addresses, and execute malicious code.
What are the potential consequences of a buffer overflow vulnerability?
A buffer overflow vulnerability can have serious consequences. It can lead to crashes, denial of service attacks, privilege escalation, remote code execution, and unauthorized access to sensitive information. These vulnerabilities are highly sought after by hackers and can be exploited to gain control over a system.
How can software developers prevent buffer overflow vulnerabilities?
Software developers can prevent buffer overflow vulnerabilities by following secure coding practices. Some measures include input validation, bounds checking, using secure functions, enforcing strong memory management, and conducting regular code reviews and security audits.
Why is it important for system administrators to stay updated on buffer overflow vulnerabilities?
System administrators should stay updated on buffer overflow vulnerabilities because they are serious security risks. By keeping up with the latest vulnerabilities, administrators can quickly apply patches and updates to mitigate the risks and ensure the security of their systems. Failure to stay updated may leave systems vulnerable to attacks.


