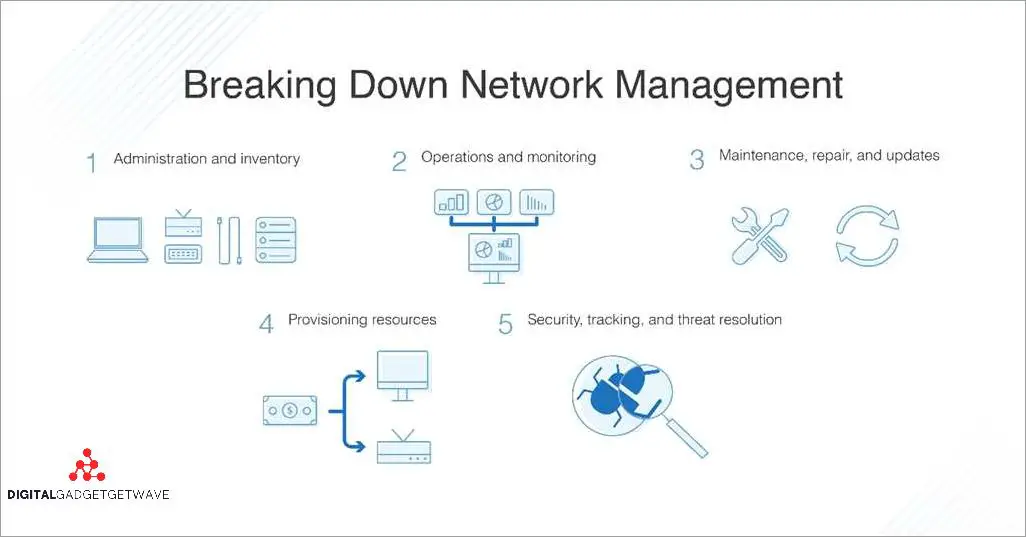
Network security is a critical aspect of any organization’s IT infrastructure. With the increasing prevalence of cyber threats, it is essential for businesses to adopt effective network administration practices to protect their sensitive data from unauthorized access and prevent potential security breaches. Implementing these practices can help organizations ensure compliance with industry regulations and protect their network from various vulnerabilities.
One of the key practices in network administration is regular patching and updating of software and systems. Patching helps to fix known vulnerabilities and secure the network against potential threats. By keeping the network up to date, organizations can address any security flaws and ensure that all their systems are running the latest, most secure versions.
In addition to patching, network administrators should also focus on proactive monitoring and incident response. Monitoring the network for any signs of intrusion or unauthorized access can help administrators detect and respond to security incidents in a timely manner. This includes implementing a firewall to control incoming and outgoing network traffic, as well as setting up strong user authentication and authorization protocols to prevent unauthorized access.
A crucial element of network administration is disaster recovery and backup. Organizations should regularly back up their data and have a plan in place to recover from any potential disasters or security breaches. Having a comprehensive backup strategy ensures that data can be restored quickly and effectively in the event of a system failure or data loss. Additionally, conducting regular audits can help identify any potential security risks and ensure that all security measures are in place.
Ensuring network security also involves encrypting sensitive data to protect it from unauthorized access. Encryption converts data into a code that can only be accessed with the correct encryption key, providing an additional layer of security against potential threats. Implementing effective password policies is also essential to prevent unauthorized access. Network administrators should enforce strong password requirements and regularly update passwords to minimize the risk of security breaches due to weak or compromising passwords.
In conclusion, effective network administration practices play a crucial role in enhancing network security. By implementing regular patching, proactive monitoring, incident response, strong authentication and authorization protocols, disaster recovery and backup strategies, and encryption, organizations can significantly reduce the risk of security breaches and protect their sensitive data from unauthorized access. Network administrators should also stay up to date with the latest security trends and industry best practices to ensure that their network security measures are robust and effective.
Contents
- 1 The importance of network security
- 2 Best Practices for Network Administration
- 3 Implementing robust firewalls
- 4 Keeping software and hardware up to date
- 5 Enforcing strong access control measures
- 6 Regular network security audits
- 7 Training and Educating Network Administrators
- 8 Building a culture of cybersecurity
- 9 Staying informed about the latest threats
- 10 The benefits of effective network administration practices
- 11 FAQ about topic “Enhance Your Network Security with Effective Network Administration Practices”
- 12 Why is network security important?
- 13 What are some common network security threats?
- 14 What are some effective network administration practices for enhancing network security?
- 15 How can network segmentation improve network security?
- 16 What is the role of employee training in network security?
The importance of network security
Network security plays a crucial role in protecting organizational data and systems from various security threats. Patching vulnerabilities and ensuring the intrusion prevention system is up to date are essential practices to minimize the risk of unauthorized access.
A well-defined network security policy is another critical component of an effective security framework. It outlines the rules and procedures that govern the use of the network, including user authentication, authorization, and data encryption.
Monitoring network activity and conducting regular audits are essential for detecting and mitigating potential vulnerabilities. These proactive measures help identify network weaknesses, unauthorized access attempts, and potential security incidents.
Firewalls are an essential component of network security. They act as a barrier between internal and external networks, monitoring and controlling network traffic to protect against unauthorized access and potential threats.
In addition to preventive measures, a comprehensive disaster recovery plan is crucial. Regular backups of critical data and systems ensure that in the event of an incident, data can be recovered and business operations can be restored quickly and effectively.
Compliance with industry regulations and standards is another important aspect of network security. Adhering to regulatory requirements helps organizations maintain a secure network environment and protects sensitive information.
Overall, network security is vital for organizations to safeguard their data, systems, and reputation. By implementing effective network administration practices such as vulnerability management, access control, and incident response planning, organizations can enhance their network security posture and minimize potential risks.
Best Practices for Network Administration
Effective network administration practices are crucial for enhancing your network security. By implementing the following best practices, you can protect your network from various security threats:
- Encryption: Implement encryption protocols to encrypt data transmission between devices on the network. This protects against unauthorized access and ensures the confidentiality of sensitive information.
- Firewall: Set up a firewall to monitor and control incoming and outgoing network traffic. This helps block unauthorized access and prevents network attacks.
- Audit: Regularly perform network audits to identify vulnerabilities and weaknesses in your network infrastructure. This allows you to take necessary actions to mitigate these risks and strengthen security.
- Authorization: Implement strong access control mechanisms to ensure that only authorized individuals have access to the network resources. This includes assigning specific user roles and permissions.
- Risk monitoring: Continuously monitor your network for potential security risks and threats. This can be done through intrusion detection systems, log monitoring, and real-time analysis of network traffic.
- Incident management: Have a well-defined incident response plan in place to handle security incidents effectively. This includes establishing clear procedures for reporting, investigating, and resolving security incidents.
- Backup and recovery: Regularly backup your network data and have a recovery plan in place in case of data loss or system failures. This ensures that your network can quickly recover from any adverse events.
- Disaster recovery: Develop a comprehensive disaster recovery plan that outlines procedures for restoring and recovering network operations in the event of a major disruption, such as a natural disaster.
- Security policy: Develop and enforce a robust security policy that outlines guidelines and rules for network access, password management, authentication, and other security-related practices.
- Patching: Regularly apply updates and patches to your network devices and software. This helps address known security vulnerabilities and ensures that your network is protected against the latest threats.
By following these best practices for network administration, you can significantly enhance the security of your network and protect against potential cyber threats. It is essential to regularly review and update your network security measures to stay ahead of evolving security risks and compliance requirements.
Implementing robust firewalls
One of the key practices in network administration for enhancing network security is implementing robust firewalls. A firewall acts as a barrier between an internal network and external networks, filtering incoming and outgoing network traffic based on a set of predetermined security rules.
To ensure the effectiveness of firewalls, continuous monitoring is essential. This involves regularly reviewing firewall logs, analyzing network traffic patterns, and identifying potential security threats or breaches. Compliance with firewall configuration standards and industry best practices is crucial for maintaining a secure network environment.
Regular firewall audits should be conducted to assess the effectiveness and compliance of firewall rules. These audits involve reviewing the configuration, rule sets, and policies to identify any vulnerabilities or weaknesses. Additionally, user authentication and authorization mechanisms should be implemented to ensure that only authorized individuals have access to the network resources.
Intrusion detection and prevention systems can be integrated with firewalls to provide an additional layer of security. These systems monitor network traffic and identify any suspicious activities or potential intrusions. Network administrators should have the necessary skills and knowledge to configure and manage these systems effectively.
Patching and updating firewalls regularly is essential for addressing any known vulnerabilities or weaknesses. Network administrators should stay informed about the latest security patches and updates released by the firewall vendors, and apply them in a timely manner to minimize the risk of exploitation.
Alongside firewalls, regular data backups and encryption should be implemented as part of a comprehensive disaster recovery plan. Network administrators should define and enforce security policies that dictate proper network usage, password management, and incident response procedures. This ensures that in the event of a network security incident or breach, the network can be restored quickly and effectively.
Choosing the right firewall solution
When it comes to network security, choosing the right firewall solution is crucial. A firewall acts as a barrier between your network and potential threats, protecting your sensitive data and preventing unauthorized access. There are several factors to consider when selecting a firewall solution, ensuring it meets your organization’s specific needs and requirements.
Authentication and Authorization: A good firewall solution should support strong authentication methods, such as two-factor authentication, to verify the identity of users attempting to access your network. It should also have robust authorization capabilities, allowing you to define access policies based on user roles and responsibilities.
Intrusion Detection and Prevention: An effective firewall solution should include intrusion detection and prevention features. This means it can detect and block any attempts to exploit vulnerabilities in your network, minimizing the risk of unauthorized access or data breaches.
Network Monitoring and Audit: It’s important to choose a firewall solution that offers comprehensive network monitoring and audit capabilities. This allows you to track network activity, identify any suspicious behavior, and investigate incidents effectively.
Encryption and Patching: Look for a firewall solution that supports encrypted connections, protecting your data as it travels across the network. Additionally, the firewall should provide regular patching and updates to ensure any security vulnerabilities are addressed promptly.
Disaster Recovery and Backup: A reliable firewall solution should have built-in disaster recovery and backup features. This means it can help you recover from any security incidents or network failures quickly and efficiently.
Compliance and Policy Enforcement: Consider a firewall solution that supports compliance with industry regulations and standards, such as GDPR or HIPAA. It should provide policy enforcement capabilities, allowing you to define and enforce security policies across your network.
Vulnerability Management: Look for a firewall solution that includes vulnerability management features. This means it can scan your network for security vulnerabilities and provide recommendations for remediation.
Incident Response and Recovery: A good firewall solution should have incident response and recovery capabilities. It should allow you to quickly identify and respond to security incidents, minimizing any potential damage and facilitating a swift recovery process.
By carefully considering these factors, you can choose the right firewall solution for your organization, enhancing your network security and protecting your sensitive data from potential threats.
Keeping software and hardware up to date
Regular updates to software and hardware are crucial for network security. By keeping all systems up to date, organizations can ensure that they are protected against the latest security threats and vulnerabilities. This includes updating operating systems, applications, and firmware.
Software updates often include patches and fixes that address security vulnerabilities and bugs. These updates can also introduce new security features and enhancements. It is important to have a comprehensive patch management policy in place to ensure that updates are tested and deployed promptly.
Hardware updates, such as firmware upgrades on routers and switches, are equally important. Firmware updates can address security vulnerabilities, improve performance, and add new features. It is important to regularly check for firmware updates from hardware vendors and apply them as needed.
A strong network administration practice includes establishing a change management policy to ensure that updates are properly authorized and documented. By following a formal change management process, organizations can mitigate the risk of unauthorized or unsupported changes that could compromise network security.
Additionally, backup and disaster recovery procedures should be in place to protect against potential data loss or network downtime during the update process. Regular backups can restore critical data in the event of an incident, and a solid disaster recovery plan can minimize the impact of any disruptions.
Regular monitoring and auditing of the network can help identify any potential security breaches or vulnerabilities. This includes monitoring for unauthorized access attempts, unusual network traffic patterns, and failed authentication attempts. Network administrators should also conduct regular security audits to assess compliance with security policies and procedures.
To enhance network security, organizations should implement robust security measures, such as firewalls, strong passwords, and encryption. Firewalls act as a barrier between a trusted internal network and external networks, preventing unauthorized access and filtering incoming and outgoing network traffic. Strong passwords and authentication mechanisms add an extra layer of security to prevent unauthorized access. Encryption helps protect sensitive data, making it unreadable to unauthorized individuals.
In conclusion, keeping software and hardware up to date is essential for network security. Regular patching, monitoring, and auditing practices, along with strong security measures, can help prevent intrusions, ensure compliance, and minimize the risk of incidents. By implementing effective network administration practices, organizations can enhance their network security and protect valuable information.
The role of software patches
Software patches are crucial for enhancing network security. A patch is a piece of code that is designed to fix or improve the functionality of a software application. When it comes to network security, patches play a significant role in protecting the network from various vulnerabilities and threats.
One important aspect of patching is keeping the network’s authentication and authorization mechanisms up to date. Patches help to address any weaknesses in these mechanisms, ensuring that only authorized users can access the network resources and preventing any unauthorized access.
Monitoring is another key area where patches can significantly improve network security. By regularly applying patches to monitoring tools, network administrators can ensure that potential security breaches are detected and responded to quickly. Patches can enhance the identification and prevention of intrusions and other malicious activities in the network.
Recovery is an essential aspect of network security, especially in the event of a security incident or disaster. Patches can help in restoring the network to its normal state quickly after such incidents by fixing any vulnerabilities or weaknesses that were exploited.
Password and encryption standards are crucial for maintaining network security. Patches for these components can strengthen the security of the network by addressing any known vulnerabilities in password policies, encryption algorithms, and key management practices.
Patching also plays a vital role in ensuring network compliance with industry standards and regulations. Through regular patching, network administrators can address any compliance gaps and ensure that the network meets the necessary security requirements.
Moreover, patches can help in conducting network audits by providing necessary updates and improvements to the auditing tools and systems. This ensures that network administrators can effectively assess the network’s security posture and identify any areas that need attention.
To summarize, software patches are essential for maintaining network security. They help in addressing vulnerabilities, improving authentication and authorization mechanisms, enhancing monitoring capabilities, enabling quick recovery, strengthening password and encryption standards, ensuring compliance, and facilitating network audits. By regularly applying patches, network administrators can significantly reduce the risk of security incidents and protect the network from malicious activities.
Regular hardware maintenance
Regular hardware maintenance is a critical component of network administration, as it ensures the smooth functioning of the entire network infrastructure. This includes conducting regular audits to identify any hardware vulnerabilities or weaknesses that may pose a risk to network security.
During the audit process, network administrators assess the compliance of hardware devices with established security policies and standards. They check for any unauthorized devices or connections, ensuring that all hardware meets the necessary security requirements. By identifying and addressing any non-compliance issues, administrators can mitigate the risk of network breaches.
Additionally, regular hardware maintenance involves disaster recovery planning and implementation. Network administrators ensure that proper backup systems are in place to protect against data loss in the event of a hardware failure or a natural disaster. This includes maintaining up-to-date backups and testing the recovery process to ensure its effectiveness.
Another important aspect of hardware maintenance is incident response. Administrators monitor the network for any unusual activity or signs of intrusion, promptly investigating and responding to any security incidents. They implement strong authentication and password policies to prevent unauthorized access to hardware devices, and regularly update and patch firmware and software to address any identified vulnerabilities.
Moreover, encryption is used to protect sensitive data transmitted over the network, ensuring that it cannot be intercepted or accessed by unauthorized individuals. Network administrators implement encryption protocols and regularly update encryption keys to maintain a high level of security.
In summary, regular hardware maintenance is crucial for network security. By conducting audits, ensuring compliance, implementing disaster recovery measures, monitoring for incidents, applying authentication and encryption, and regular patching, network administrators mitigate risks and enhance the security of the network infrastructure.
Enforcing strong access control measures
Access control is a critical component of network security. It involves the implementation of policies and technologies to restrict unauthorized access to network resources. One of the key measures in enforcing strong access control is the use of password authentication. It is essential to use strong and unique passwords for all accounts, regularly update them, and enforce password complexity requirements.
Administrative privileges should be strictly controlled and limited to authorized personnel. Only individuals with a legitimate need should have elevated access rights. Implementing a role-based access control system can help manage and assign permissions effectively.
Recovery mechanisms should be in place to ensure the secure retrieval of data in case of an incident. Regular backup of critical information is essential to mitigate the impact of a disaster. It is important to test the backups periodically to ensure their reliability.
Regular patching of operating systems and software applications is essential to prevent exploitation of known vulnerabilities. Network administrators should monitor vendor releases and security advisories to stay up-to-date with the latest patches and updates.
Monitoring the network is essential to detect and respond to any potential security threats. Intrusion detection systems, intrusion prevention systems, and firewall logs should be regularly reviewed to identify any suspicious activity.
An audit of network security controls should be conducted periodically to assess the effectiveness of implemented measures. This can help identify any weaknesses and vulnerabilities that need to be addressed.
Implementing encryption mechanisms, such as secure socket layer (SSL) or virtual private network (VPN), can help protect sensitive data transmitted over the network.
Network administrators should have an incident response plan in place to effectively handle any security breaches or incidents. The plan should include incident reporting, incident analysis and containment, remediation measures, andcommunication protocols.
Compliance withsecurity policies and regulatory requirements is essential. Network administrators should stay informed about relevant industry-specific compliance standards and ensure the network infrastructure meets the necessary security standards.
In conclusion, enforcing strong access control measures is crucial for network security. By implementing effective password authentication, limiting administrative privileges, implementing recovery mechanisms, regularly patching software, monitoring the network, conducting audits, implementing encryption, having an incident response plan, and ensuring compliance with security policies, network administrators can enhance the overall security of the network.
Implementing multi-factor authentication

Multi-factor authentication (MFA) is a crucial step in enhancing network security and protecting against unauthorized access. By requiring users to provide multiple forms of identification, such as a password, a fingerprint, or a security token, MFA adds an extra layer of protection to the network and significantly reduces the risk of unauthorized intrusion.
To implement MFA effectively, network administrators need to conduct a thorough audit of their network infrastructure and assess potential vulnerabilities. This audit should include a review of existing security policies, disaster recovery plans, and incident response procedures. By identifying weaknesses and addressing them, administrators can ensure that MFA is implemented in a way that aligns with organizational goals and compliance requirements.
Network monitoring is another critical aspect of MFA implementation. By continuously monitoring network traffic and user activity, administrators can quickly identify any suspicious behavior or potential security breaches. This monitoring should encompass aspects such as firewall logs, intrusion detection systems, and vulnerability scan results. By actively monitoring the network, administrators can respond promptly to any incidents and take appropriate action.
In addition to implementing MFA, regular data backup and recovery measures should be in place to ensure business continuity in the event of a security incident or system failure. By conducting regular backups and testing the recovery process, administrators can minimize the impact of a security breach and expedite the recovery process.
Furthermore, administrators should regularly update and patch their network devices and software to address any known vulnerabilities. By staying up-to-date with the latest security patches, administrators can proactively protect the network from potential exploits and reduce the risk of unauthorized access.
Lastly, network administrators should enforce strong password policies and promote the use of encryption for sensitive data. Passwords should be complex, unique, and regularly changed to prevent unauthorized access. Encryption should be used to secure data both in transit and at rest, ensuring that even if intercepted, the data remains protected. By combining MFA, password policies, and encryption, administrators can create a robust security framework that safeguards the network from evolving threats and unauthorized access attempts.
Monitoring access logs
Monitoring access logs is a critical step in ensuring the security of your network. It involves regularly reviewing and analyzing the logs that record information about network access and authentication attempts. By monitoring access logs, you can identify any unauthorized access attempts, detect intrusions, and mitigate potential risks to your network.
Access logs provide valuable information about the security of your network. They can help you identify suspicious activity, such as failed login attempts or repeated authentication requests, which may indicate an intrusion or an attempt to exploit a vulnerability. By monitoring access logs, you can promptly respond to these incidents and take necessary measures to enhance the security of your network.
Monitoring access logs also helps in incident recovery and forensic analysis. In the event of a security incident, access logs can provide valuable information that can assist in identifying the source of the incident and the extent of the damage. This information is crucial for taking appropriate actions to recover from the incident and prevent similar incidents in the future.
Moreover, monitoring access logs is essential for ensuring compliance with security policies and regulations. Many regulatory frameworks require organizations to maintain and regularly review access logs to demonstrate their adherence to security standards. By monitoring access logs, you can ensure that your network is in compliance with these requirements and take necessary actions to address any vulnerabilities or non-compliance issues.
To effectively monitor access logs, it is important to have a centralized log management system in place. This system should collect logs from various sources within your network, such as firewalls, intrusion detection systems, and authentication servers. Furthermore, implementing encryption and strong password policies for accessing and analyzing the logs can further enhance the security of your log management system.
In conclusion, monitoring access logs is a crucial aspect of network administration and security. It helps in detecting and responding to potential security incidents, aids in incident recovery and forensic analysis, ensures compliance with security policies, and enhances the overall security of your network. By implementing effective access log monitoring practices, you can proactively identify and mitigate any vulnerabilities or threats to your network.
Regular network security audits
Regular network security audits are an essential part of maintaining a secure network environment. These audits help organizations identify and address vulnerabilities in their network infrastructure, policies, and procedures. By conducting these audits on a regular basis, organizations can stay ahead of potential risks and ensure that their network remains secure.
During a network security audit, administrators review the organization’s network architecture, firewall configurations, and access controls to identify any potential weaknesses or areas of improvement. They may also check for proper authentication and authorization protocols, such as strong password requirements and user access levels.
In addition, network security audits involve checking for any unauthorized access or intrusion attempts. Administrators can monitor system logs and network traffic to identify any suspicious activity that may indicate a breach or attempted breach. By promptly detecting and responding to these incidents, organizations can minimize the potential damage and mitigate the risk of future attacks.
Network security audits also include reviewing the organization’s backup and disaster recovery procedures. Administrators ensure that regular data backups are performed, and that the organization has a comprehensive disaster recovery plan in place. This ensures that in the event of a security incident or system failure, the organization can quickly recover and resume normal operations.
Furthermore, network security audits involve reviewing the organization’s patching and updating processes. Administrators verify that all network devices and software are up to date with the latest security patches, reducing the risk of known vulnerabilities being exploited.
Finally, network security audits may also involve assessing the organization’s encryption and monitoring practices. Administrators ensure that sensitive data is appropriately encrypted, both in transit and at rest, to protect it from unauthorized access. They also check that monitoring mechanisms are in place to detect and respond to any security breaches in a timely manner.
In conclusion, regular network security audits are crucial for enhancing network security and reducing the risk of unauthorized access or data breaches. By conducting these audits, organizations can identify vulnerabilities, update policies and procedures, and ensure that their network is well-protected against potential threats.
Identifying vulnerabilities
Identifying vulnerabilities is a crucial aspect of network administration and plays a vital role in enhancing network security. By systematically assessing the network components, potential weaknesses can be identified and remedial measures can be implemented to safeguard against potential threats.
One effective practice for identifying vulnerabilities is the establishment of a comprehensive security policy. This policy outlines the rules and guidelines for network access, password management, and data encryption. Regularly reviewing and updating this policy ensures that potential vulnerabilities are identified and addressed in a timely manner.
Another important aspect is the implementation of intrusion detection and prevention systems. These systems monitor network traffic and identify any unauthorized access attempts or suspicious activities. By constantly monitoring network traffic, administrators can quickly identify and respond to potential vulnerabilities.
Incident response and recovery plans are also essential for identifying vulnerabilities. These plans outline the steps to be taken in the event of a security breach or incident and provide guidelines for timely recovery. Regular testing and updating of these plans is crucial to ensure preparedness and identify any potential vulnerabilities in the processes.
Furthermore, the implementation of strong authentication and authorization mechanisms is critical for identifying vulnerabilities. User access control should be based on the principle of least privilege, ensuring that users only have access to the resources necessary for their roles. This minimizes the risk of unauthorized access and reduces potential vulnerabilities.
Regular network monitoring and auditing are also effective practices for identifying vulnerabilities. By analyzing logs and conducting regular security assessments, administrators can identify any potential weaknesses or security gaps. This allows for proactive measures to be taken to address vulnerabilities and ensure compliance with security standards.
In conclusion, identifying vulnerabilities is a continuous process that requires a comprehensive approach encompassing policies, encryption, intrusion detection, incident response, authorization, authentication, monitoring, audits, and compliance. By implementing these practices, network administrators can proactively identify and address potential vulnerabilities, enhancing the overall security of the network.
Conducting penetration tests
Penetration testing, also known as ethical hacking, is a crucial practice in network administration to identify vulnerabilities in a system’s security infrastructure. It involves the simulation of an authorized cyber attack to evaluate the effectiveness of an organization’s security measures, including password policies and authorization protocols.
By conducting penetration tests, network administrators can proactively identify potential weaknesses that may lead to security incidents or unauthorized intrusions. These tests can also help assess the effectiveness of incident response and recovery procedures in case of a security breach.
During a penetration test, various security controls and configurations are thoroughly audited, such as firewall settings, encryption mechanisms, and authentication protocols. Network administrators can use the results of the test to identify and address any vulnerabilities and ensure compliance with industry standards and regulations.
Regular monitoring of the network infrastructure is essential to detect any potential vulnerabilities and promptly apply security patches. This helps reduce the risk of unauthorized access and data breaches. Network administrators should also implement backup and disaster recovery plans to minimize the impact of any security incidents.
Penetration tests can be conducted both internally and externally, emulating different potential attack scenarios. By testing the security from various angles, network administrators can gain a holistic understanding of the organization’s security posture and identify any weaknesses that are potentially exploitable.
Overall, conducting penetration tests is a vital practice in network administration as it helps identify vulnerabilities, strengthen security measures, and ensure the integrity and confidentiality of sensitive data.
Training and Educating Network Administrators
Effective network administration practices play a crucial role in enhancing network security. To ensure the success of these practices, it is imperative to provide proper training and education to network administrators. Through comprehensive training programs, network administrators can gain the knowledge and skills necessary to manage and safeguard networks efficiently.
One key area of training for network administrators is vulnerability management. Administrators should be trained on identifying and assessing vulnerabilities in the network infrastructure. This involves understanding the importance of regular patching and keeping systems up to date with the latest security measures to mitigate potential risks.
Encrypting sensitive data is another critical aspect of network security. Network administrators should receive education on encryption techniques and the importance of implementing encryption protocols to protect data in transit and at rest. This helps prevent unauthorized access and ensures the confidentiality and integrity of sensitive information.
Training should also focus on creating strong password policies. Network administrators should be educated about the significance of using complex and unique passwords, as well as the importance of regularly changing them. Additionally, they should learn about implementing multi-factor authentication methods to add an extra layer of security.
In order to proactively manage and mitigate risks, network administrators should be trained on conducting regular audits. They should understand how to monitor network traffic and detect any suspicious activities or unauthorized access attempts. By having proper auditing procedures in place, organizations can identify potential vulnerabilities and take appropriate actions to address them.
Network administrators should also be well-versed in disaster recovery and backup strategies. Training should cover the creation and maintenance of backup systems and data recovery protocols to ensure that critical information can be restored in the event of a network failure or attack. This helps minimize downtime and ensures the continuity of business operations.
Furthermore, network administrators need to be educated on incident response procedures. They should understand how to handle security incidents or breaches effectively, including communicating with relevant stakeholders, investigating the incident, and implementing necessary remediation measures. This enables organizations to respond promptly to security incidents and minimize the potential impact.
Finally, network administrators should receive training on the proper use and configuration of network security tools such as firewalls and intrusion detection/prevention systems. They should understand how to monitor network traffic and analyze logs to identify and respond to potential security threats. Additionally, they should be knowledgeable about compliance requirements and the importance of ensuring network security practices align with industry regulations.
In conclusion, training and education are vital for network administrators to effectively manage and secure networks. By providing comprehensive training programs that cover areas such as vulnerability management, encryption, password policies, auditing, disaster recovery, incident response, and network security tools, organizations can empower their administrators to enhance network security and mitigate potential risks effectively.
Building a culture of cybersecurity
In today’s digital landscape, building a culture of cybersecurity is vital for organizations to protect their network and data from potential threats. This involves implementing a comprehensive network administration strategy that focuses on various key elements such as audit, risk assessment, policy development, and effective monitoring.
One crucial aspect of building a culture of cybersecurity is conducting regular audits of the network infrastructure. This helps identify any vulnerabilities or weaknesses that may exist within the system, allowing administrators to take appropriate measures to rectify them. Additionally, conducting audits also ensures compliance with industry regulations and standards.
Developing robust policies is another essential step in building a culture of cybersecurity. These policies should cover areas such as access authorization, password management, and encryption protocols. By establishing clear policies, organizations can ensure that all employees are aware of their roles and responsibilities in maintaining network security.
Implementing intrusion detection and monitoring systems is crucial for proactively identifying and mitigating potential security breaches. By continuously tracking network traffic and analyzing patterns, administrators can promptly respond to any suspicious activities and prevent unauthorized access to sensitive data.
Backup and recovery procedures are also integral to a culture of cybersecurity. By regularly backing up critical data, organizations can ensure that in the event of a disaster or incident, they can quickly restore their network to its previous state. Additionally, organizations should have a clearly defined incident response plan in place to handle any security breaches efficiently.
Another important aspect of network administration for building a culture of cybersecurity is ensuring that all software and systems are up to date with the latest patches. This helps address any known vulnerabilities that attackers could exploit. Additionally, a robust firewall should be implemented to control and monitor incoming and outgoing network traffic.
In conclusion, building a culture of cybersecurity requires a comprehensive network administration approach that covers various elements such as audit, policy development, risk assessment, intrusion monitoring, compliance, backup and recovery, incident response, encryption, vulnerability patching, firewall implementation, and network security. By prioritizing these areas, organizations can enhance their network security and protect their valuable data from potential threats.
Providing ongoing training
One of the most important practices in network administration for enhancing network security is to provide ongoing training to network administrators and users. This helps ensure that they are aware of the latest security threats and best practices to protect the network.
Training programs should cover various aspects of network security, including encryption, backup and recovery, disaster risk management, monitoring and compliance. Administrators and users should be familiar with incident management procedures, password security, firewall settings, and vulnerability testing.
One key aspect of training is to emphasize the importance of strong authentication and authorization practices. Network administrators should be trained on how to implement and manage secure authentication mechanisms, such as two-factor authentication and secure password policies.
Regular training sessions should be conducted to keep administrators and users updated on the latest security threats and technologies. These sessions can include sharing real-life examples of security breaches and their consequences, as well as educating users on how to identify and respond to security incidents.
Furthermore, administrators should be trained on how to apply necessary security patches and updates to network devices and systems. Patching known vulnerabilities is crucial for preventing unauthorized access and attacks.
By providing ongoing training, organizations can create a culture of security awareness and ensure that network administrators and users are equipped with the knowledge and skills necessary to maintain a secure network environment.
Staying informed about the latest threats
Ensuring network security requires staying informed about the latest threats that could potentially compromise the network’s integrity and data. This can be achieved through continuous monitoring and analysis of emerging risks and vulnerabilities. Regularly checking reputable sources, such as security forums, blogs, and news sites, can provide valuable insights into new attack methodologies and strategies.
One crucial aspect of staying informed is keeping abreast of the latest software vulnerabilities and patches. Software vendors often release updates and patches to address known security vulnerabilities. By promptly applying these patches, network administrators can mitigate the risk of exploitation and unauthorized access.
Implementing a comprehensive password policy is another vital practice for staying informed about the latest threats. Network administrators should enforce strong password requirements, such as using a combination of uppercase and lowercase letters, numbers, and special characters. Regularly educating users about the importance of unique and complex passwords can help prevent unauthorized access and protect sensitive information from being compromised.
Authorization and authentication mechanisms are key components of network security. Network administrators should regularly review and update user access rights and privileges. By ensuring that only authorized users have access to sensitive information and resources, administrators can reduce the risk of potential intrusions or unauthorized activities.
Continuous network monitoring is essential for identifying potential security breaches and detecting any abnormal network activities. Network administrators should implement intrusion detection and prevention systems and regularly analyze logs and network traffic to identify any unauthorized access or suspicious behavior.
Encryption is another critical practice that can enhance network security. By encrypting sensitive data and communications, network administrators can protect confidential information from unauthorized interception or access. Implementing industry-standard encryption protocols and regularly reviewing and updating encryption practices can enhance network security.
To stay informed about the latest threats, network administrators should also conduct regular security audits and disaster recovery tests. These practices help ensure compliance with security policies and procedures, identify vulnerabilities, and test the effectiveness of security measures and response plans.
Engaging in professional development
As a network administrator, it is crucial to engage in professional development to stay updated with the latest trends and practices in network security. The constantly evolving nature of technology means that there are always new threats and vulnerabilities that need to be addressed. Staying informed about the latest incident and intrusion techniques is essential to protect the network from potential attacks.
In addition to staying informed about security incidents and intrusions, network administrators should also focus on enhancing their skills in network administration. This includes learning about encryption techniques, backup and recovery strategies, strong password policies, and risk management. Implementing encryption helps protect sensitive data from unauthorized access, while regular backups ensure that data can be restored in case of a disaster.
Furthermore, network administrators should also be familiar with security policies and procedures. Implementing and enforcing security policies is crucial in maintaining network security. This includes regularly patching systems to address known vulnerabilities, configuring firewalls to protect against unauthorized access, and ensuring network compliance with industry regulations.
Monitoring the network for any suspicious activity is another important aspect of network administration. Network administrators should regularly perform security audits to identify any potential vulnerabilities and take necessary actions to mitigate them. This includes monitoring network traffic, analyzing log files, and implementing strong authentication mechanisms.
Engaging in professional development allows network administrators to stay updated with the latest tools, techniques, and best practices in network security. By constantly enhancing their skills and knowledge, network administrators can effectively protect the network from potential threats and ensure the security and integrity of the network infrastructure.
Participating in industry forums
Participating in industry forums is a valuable practice for network administrators to enhance network security. Through discussions and knowledge sharing, administrators gain insights into the latest trends, techniques, and best practices for securing networks.
By actively engaging in industry forums, administrators can stay updated on the latest authorization and authentication methods, helping them implement stronger access controls and reduce the risk of unauthorized access to the network. Discussions may cover topics such as multi-factor authentication, role-based access control, and secure password policies.
Industry forums also provide a platform for administrators to learn about new vulnerability and security threats. By staying informed about the latest exploits and vulnerabilities, administrators can proactively apply patches and updates to mitigate risks. These discussions may focus on common vulnerabilities such as outdated software, misconfigured settings, or inadequate encryption protocols.
In addition, industry forums can help network administrators improve their incident response and recovery capabilities. Discussions on incident handling, disaster recovery, and backup strategies allow administrators to learn from others’ experiences and adopt best practices. Administrators can gain insights into effective intrusion detection and prevention techniques, enabling them to better protect their networks from cyber attacks.
Industry forums also play a crucial role in ensuring compliance with industry regulations and standards. Through discussions on security policies, audits, and monitoring, administrators can align their network security practices with legal requirements. They can learn about the latest compliance frameworks, share insights on policy implementation, and understand how to conduct effective security audits.
In summary, active participation in industry forums can greatly enhance network security administration practices. By leveraging the collective knowledge and experiences of industry professionals, administrators can strengthen their networks, implement robust security measures, and protect against emerging threats.
The benefits of effective network administration practices

Effective network administration practices provide numerous benefits for organizations, ensuring the security and integrity of their networks. By implementing proactive monitoring systems, administrators can detect and respond to potential threats in real-time, reducing the risk of unauthorized access or data breaches.
Encryption is another crucial practice that helps protect sensitive information. By encrypting data, administrators make it unreadable to unauthorized users, even if it is intercepted. This ensures that confidential information remains secure and private.
Regular patching is an essential practice to address known vulnerabilities in network systems. Administrators apply software updates and patches promptly to minimize the risk of exploitation by hackers. This practice helps maintain a higher level of network security.
Compliance with industry regulations is vital for organizations to avoid penalties and legal repercussions. Effective network administration practices include ensuring compliance with relevant regulations and standards, such as the General Data Protection Regulation (GDPR) or the Payment Card Industry Data Security Standard (PCI DSS).
Rapid recovery from network incidents is crucial to minimize downtime and maintain business continuity. Administrators implement robust backup and disaster recovery plans to ensure that critical data and systems can be restored quickly in the event of a network failure or security breach.
Effective network administration practices also involve vulnerability scanning and intrusion detection systems. Administrators regularly assess the network for vulnerabilities and potential security breaches. By promptly identifying and addressing these issues, administrators can mitigate risks and prevent unauthorized access.
Developing and enforcing network security policies is another key practice. Administrators establish security policies that define acceptable use, password requirements, and access controls. By enforcing these policies, organizations can reduce the risk of security incidents caused by human error or negligence.
Regular security audits help identify and address potential weaknesses in the network infrastructure. Administrators conduct comprehensive assessments to evaluate the effectiveness of security controls, identify areas for improvement, and ensure compliance with established policies and regulations.
Authentication and authorization practices play a crucial role in network security. Administrators implement strong authentication mechanisms, such as multi-factor authentication, to verify the identity of users accessing the network. Authorization ensures that users only have access to the resources and data they need to perform their duties.
In summary, effective network administration practices provide several benefits, including enhanced security, improved compliance, faster incident recovery, and reduced risks. By adopting these practices, organizations can safeguard their networks and protect their valuable data from unauthorized access or loss.
FAQ about topic “Enhance Your Network Security with Effective Network Administration Practices”
Why is network security important?
Network security is important because it helps protect sensitive data and information from unauthorized access, ensuring the confidentiality, integrity, and availability of the network and its resources. Without proper network security measures in place, organizations are at a higher risk of data breaches, malware attacks, and other security incidents that can lead to financial loss, reputational damage, and legal consequences.
What are some common network security threats?
Some common network security threats include malware infections, phishing attacks, denial-of-service (DoS) attacks, insider threats, and unauthorized access. Malware can compromise network security by infecting systems and stealing or damaging data, while phishing attacks trick users into revealing sensitive information. DoS attacks overload network resources, preventing legitimate users from accessing them, and insider threats involve employees or other authorized individuals abusing their privileges. Unauthorized access refers to unauthorized individuals gaining access to a network or its resources.
What are some effective network administration practices for enhancing network security?
Some effective network administration practices for enhancing network security include regularly updating and patching network devices and software to address known vulnerabilities, implementing strong and unique passwords, using multifactor authentication, regularly backing up data, monitoring network traffic and logs for suspicious activity, implementing firewalls and intrusion detection systems, conducting regular security audits and assessments, educating employees about security best practices, and restricting access to sensitive data and resources based on the principle of least privilege.
How can network segmentation improve network security?
Network segmentation involves dividing a network into smaller, isolated segments, which helps improve network security by containing potential security incidents and limiting their impact. By separating different areas of a network and controlling the flow of traffic between them, organizations can reduce the risk of lateral movement by attackers. If an attacker gains access to one segment, network segmentation makes it more difficult for them to move laterally to other segments and gain unauthorized access to sensitive data or resources.
What is the role of employee training in network security?
Employee training plays a crucial role in network security. It helps raise awareness among employees about the importance of network security and teaches them about security best practices to follow. Proper training can help employees identify and report phishing attempts, avoid clicking on suspicious links or opening suspicious attachments, use strong passwords, and follow protocols for accessing and handling sensitive data. By ensuring that employees understand their role in maintaining network security, organizations can significantly reduce the risk of security incidents caused by human error or negligence.


