
Wireless access has revolutionized the way we connect and access information, but it has also introduced new security risks. One such risk is the evil twin attack, where malicious individuals create an unauthorized access point (AP) to trick unsuspecting victims into connecting to a fraudulent network.
Evil twin attacks can leave you vulnerable to security breaches, as they allow hackers to intercept your data, steal your credentials, and even inject malware into your device. These attacks involve the manipulation of network authentication processes and often rely on spoofing techniques to deceive users.
To protect yourself from evil twin attacks, here are 5 essential tips:
- Always verify network names and credentials: Before connecting to any wireless network, double-check the network name and make sure it matches the legitimate network. Additionally, verify the credentials required to connect, such as passwords or security keys.
- Avoid connecting to open networks: Open networks, especially those without any password or security measures, are more susceptible to evil twin attacks. Whenever possible, connect to networks that require some form of authentication.
- Use a reliable virtual private network (VPN): A VPN encrypts your internet traffic and protects your data from being intercepted by hackers. By using a VPN, you create a secure tunnel between your device and the network, making it difficult for attackers to access your information.
- Keep your devices updated: Regularly update your devices’ software and security patches to ensure you have the latest protections against known vulnerabilities. These updates often include fixes for security flaws that could be exploited during an evil twin attack.
- Be cautious of unfamiliar networks: When in public spaces, be careful when connecting to unfamiliar networks. Rogue networks set up by attackers may mimic legitimate networks, so it’s best to avoid connecting to any network that seems suspicious.
By following these essential tips, you can significantly reduce the risk of falling victim to evil twin attacks and ensure the security of your wireless connections. Stay vigilant and prioritize your online security to stay one step ahead of potential hackers.
Contents
- 1 What is an Evil Twin Attack?
- 2 Tip #1: Always Verify the Network
- 3 Tip #2: Avoid Connecting to Public Wi-Fi Automatically
- 4 Tip #3: Don’t Share Sensitive Information on Unsecured Networks
- 5 Tip #4: Keep Your Devices Updated and Secure
- 6 Tip #5: Use a Firewall and Antivirus Software
- 7 FAQ about topic “Protect Yourself from Evil Twin Attacks: 5 Essential Tips”
- 8 What is an evil twin attack?
- 9 How can I identify an evil twin network?
- 10 What are some ways to protect myself from evil twin attacks?
- 11 Can I use public Wi-Fi safely?
- 12 What should I do if I suspect I’ve connected to an evil twin network?
What is an Evil Twin Attack?
An Evil Twin Attack is a type of wireless hacking attack where a cybercriminal creates a fraudulent wireless access point (AP) to mimic a legitimate one. This rogue AP is designed to manipulate victims into connecting to it, believing it to be a trusted network.
The main goal of an Evil Twin Attack is to deceive users into unknowingly disclosing sensitive information such as login credentials and personal data. Once connected to the malicious AP, users become vulnerable to various types of attacks, including malware infection, phishing attempts, and unauthorized access to their devices.
Evil Twin Attacks often take advantage of the trust users place in familiar networks. Cybercriminals use spoofing techniques to make their rogue APs appear similar to legitimate networks, often using the same network name (SSID) and security settings. This makes it difficult for users to distinguish between the real network and the fake one.
To protect yourself from Evil Twin Attacks, it is important to be cautious and skeptical when connecting to wireless networks. Always verify the legitimacy of the network before entering any sensitive information. Look for signs of security, such as a padlock symbol or HTTPS in the URL, and consider using a virtual private network (VPN) for added security.
In conclusion, an Evil Twin Attack is a malicious hacking attack that targets wireless networks. By creating a replica of a legitimate network, cybercriminals deceive users into connecting to their rogue APs, often leading to the disclosure of sensitive information and the compromise of their devices. Implementing strong authentication measures and being vigilant when connecting to wireless networks can help protect against these attacks.
Understanding the Threat
Evil twin attacks are a type of hacking attack that targets the authentication process of wireless networks. In this type of attack, a malicious actor creates a rogue access point (AP) with the same name and credentials as a legitimate network. The goal of the attacker is to lure victims into connecting to the evil twin network, allowing the attacker to intercept their data and potentially gain unauthorized access to their devices.
Evil twin attacks often rely on phishing techniques to trick users into connecting to the fraudulent network. The attacker may use social engineering tactics, such as sending out phishing emails or setting up fake websites, to convince victims to join the malicious network. Once connected, the attacker can eavesdrop on the victim’s internet traffic, inject malware, or even spoof websites to collect sensitive information like login credentials.
This type of attack is particularly effective against individuals who are unaware of the risks associated with using public wireless networks and do not take proper precautions to secure their connections. The convenience of wireless networks often leads users to prioritize convenience over security, making them vulnerable to evil twin attacks.
To protect yourself from evil twin attacks, it is essential to be cautious when connecting to wireless networks. Always verify the legitimacy of a network before connecting, especially in public places where malicious actors are more likely to be present. Additionally, use strong, unique passwords for your devices and accounts to minimize the risk of unauthorized access.
Furthermore, consider using a virtual private network (VPN) when connecting to wireless networks. A VPN encrypts your internet traffic, preventing anyone on the same network from intercepting your data. This can greatly enhance your security and protect your sensitive information from falling into the wrong hands.
Overall, understanding the threat posed by evil twin attacks and taking appropriate precautions is crucial for maintaining the security of your network and personal information. By staying vigilant and implementing security measures, you can significantly reduce the risk of falling victim to these malicious attacks.
How Evil Twin Attacks Work
An evil twin attack is a type of cyber attack that involves the manipulation of Wi-Fi networks to deceive victims and gain unauthorized access to their personal information or sensitive data. In this attack, the attacker sets up a rogue access point (AP) that mimics a legitimate network, making it difficult for victims to distinguish between the two.
The purpose of an evil twin attack is to trick victims into connecting to the malicious network, thinking it is a secure and trusted network. Once connected, the attacker can eavesdrop on the victim’s online activities, steal their login credentials, and even inject malware or other malicious software into their devices.
The attack usually starts with the attacker setting up a fraudulent Wi-Fi network with a name similar to that of a legitimate network in the vicinity. This network, known as the evil twin, appears to be a trusted network and often has a strong signal to attract potential victims. The attacker may also employ techniques like spoofing or phishing to trick victims into connecting to their network.
When victims unknowingly connect to the evil twin network, they become vulnerable to various security risks. The attacker can intercept their internet traffic, capture their login credentials, and even manipulate the data they send and receive. This allows the attacker to carry out various malicious activities, including hacking into their devices and stealing sensitive information.
To protect themselves from evil twin attacks, users should always verify the authenticity of a Wi-Fi network before connecting to it. This can be done by checking the network name with the legitimate network owner or comparing the network’s MAC address. Additionally, enabling strong security measures like two-factor authentication and using a virtual private network (VPN) can add an extra layer of protection against such attacks.
Tip #1: Always Verify the Network
When connecting to a wireless network, it is important to always verify its legitimacy, especially in public places such as airports, cafes, or hotels. This is because evil twin attacks, also known as rogue access point attacks, occur when a fraudulent network is set up to mimic a legitimate one, making unsuspecting users vulnerable to hacking and data theft.
Evil twin attacks can be carried out by hackers who create a network with a similar name to a legitimate network, tricking victims into connecting to it. Once connected, the attacker can gain access to sensitive information, such as login credentials or personal data.
To protect yourself from evil twin attacks, always verify the legitimacy of a network before connecting. Look for signs of manipulation, such as a suspiciously strong or weak signal, or a network name that closely resembles a popular network. Additionally, pay attention to any warnings or notifications that may indicate a potential security threat.
To further protect yourself, enable strong authentication methods, such as two-factor authentication or using a Virtual Private Network (VPN) when connecting to public Wi-Fi networks. These additional layers of security can help prevent unauthorized access and protect your data from being intercepted by malicious actors.
It is also important to keep your devices and software up to date and protected against malware. Malicious software can be used by attackers to exploit vulnerabilities in your system and gain unauthorized access to your network or personal information.
In summary, always take the necessary precautions when connecting to a wireless network. Verify its legitimacy, enable strong authentication methods, and keep your devices protected against malware. By following these tips, you can greatly reduce the risk of falling victim to evil twin attacks and ensure the security of your personal information.
Check the Network Name and Password
One of the most important steps in protecting yourself from evil twin attacks is to carefully check the network name and password before connecting to any wireless network. Evil twin attacks involve creating a fraudulent access point (AP) that appears to be a legitimate network. The attackers often set up a rogue AP with a name and password that closely resemble a legitimate network, making it difficult for victims to distinguish between the two.
To protect yourself, always double-check the network name (also known as the SSID) and password before connecting to any wireless network. Be wary of networks that have the same name as a known network but are located in a different area. Attackers can use this tactic to trick users into connecting to their malicious network.
In addition, avoid connecting to networks that do not require passwords or have weak security credentials. Such networks are often vulnerable to hacking and can be easily compromised by attackers. Always choose networks that use strong encryption and authentication protocols to ensure the security of your data.
Another way attackers exploit vulnerable networks is by injecting malware or using malicious software on the evil twin AP. When connecting to a network, it is crucial to have up-to-date security software on your device to detect and prevent any malicious activity. Regularly update your antivirus and firewall software to protect against potential threats.
Remember, attackers rely on the manipulation of network names and credentials to gain unauthorized access to sensitive information. By carefully checking the network name and password before connecting, you can significantly reduce the risk of falling victim to an evil twin attack.
Use a VPN for Secure Connection
A VPN, or Virtual Private Network, is an essential tool for protecting yourself from evil twin attacks. When you connect to the internet through a VPN, it creates a secure and encrypted connection between your device and the VPN server. This means that any data transmitted between you and the server is protected from malware, manipulation, and fraudulent activities.
By using a VPN, you can prevent malicious actors from intercepting your data and carrying out phishing attacks. An evil twin attack involves an attacker setting up a rogue wireless access point that appears to be legitimate, tricking unsuspecting victims into connecting to it. Once connected, the attacker can gain access to the victim’s network and potentially steal sensitive information or carry out hacking attempts.
With a VPN, your connection to the internet is encrypted, making it virtually impossible for attackers to intercept your data or gain access to your network. This added layer of security ensures that your credentials and personal information remain safe and secure.
In addition to protecting against evil twin attacks, a VPN also offers other security benefits. It hides your IP address, making it difficult for anyone to track your online activities. It also helps bypass geo-restrictions and censorship, allowing you to access content that may be blocked in your location.
When choosing a VPN, make sure to select one that uses strong encryption protocols and has a strict no-logs policy. This ensures that your data is protected and that your online activities remain private. It’s also important to regularly update your VPN software to stay protected against any vulnerabilities that may arise.
In summary, using a VPN is an essential step in protecting yourself from evil twin attacks and ensuring the security of your online activities. It adds a layer of encryption that keeps your data safe from malicious actors and provides you with a secure and anonymous browsing experience.
Tip #2: Avoid Connecting to Public Wi-Fi Automatically
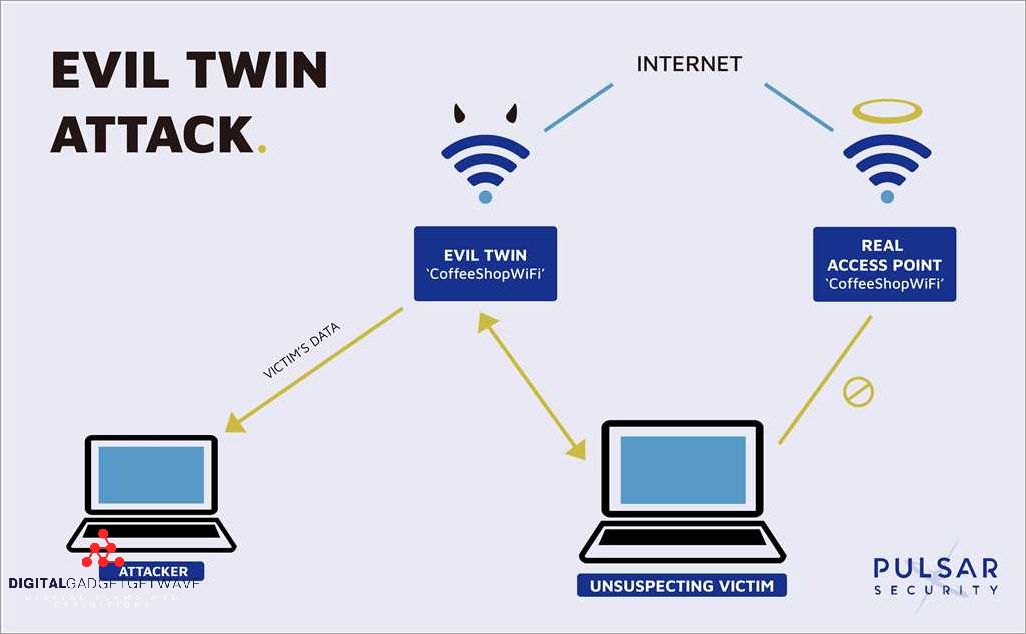
Connecting to public Wi-Fi networks can expose you to fraudulent activities and malicious attacks. Hackers often take advantage of unsecured Wi-Fi networks to conduct various types of attacks such as evil twin, spoofing, and phishing.
An evil twin attack is a type of wireless network attack where hackers create a fraudulent Wi-Fi access point (AP) that mimics a legitimate network. When users unknowingly connect to this malicious network, their sensitive information, such as login credentials or credit card details, can be intercepted by the attacker.
Automatic connection to public Wi-Fi can make you vulnerable to such attacks. It is important to disable the automatic connection feature on your devices to ensure that you have control over which networks you connect to.
Before connecting to a public Wi-Fi network, always verify its authenticity. Check with the staff of the establishment or use a reputable Wi-Fi network provider if available. Avoid connecting to networks with generic or suspicious names, as these could be set up by attackers to lure victims into their fraudulent schemes.
Remember to always use a virtual private network (VPN) when connecting to public Wi-Fi networks. A VPN encrypts your internet traffic, making it much harder for hackers to intercept or manipulate your data.
By following these tips, you can enhance your authentication security and reduce the risk of falling victim to wireless attacks or having your personal information compromised by malware or malicious individuals.
Disable Auto-Connect Feature on Devices
One of the essential steps to protect yourself from evil twin attacks is to disable the auto-connect feature on your devices. By default, many devices are configured to automatically connect to any available wireless network without any user intervention. This feature is convenient but also makes you vulnerable to hacking and security breaches.
An evil twin attack occurs when a hacker sets up a rogue access point that resembles a legitimate wireless network. The hacker can then intercept your device’s communication and gain access to your sensitive information. This could lead to identity theft, unauthorized access to your accounts, or the installation of malware on your device.
Disabling the auto-connect feature on your devices helps prevent malicious actors from easily gaining access to your wireless network. By manually selecting a network to connect to, you can ensure that you are connecting to a trusted and secure network instead of falling victim to an evil twin attack.
Furthermore, disabling the auto-connect feature can also protect against phishing attempts. Attackers may create fake networks with names similar to popular ones to trick victims into connecting to them. Once connected, they can launch phishing attacks to steal your login credentials or manipulate your online activities.
To disable auto-connect on your devices, go to your device’s settings and look for the Wi-Fi options. In this menu, you should find a list of available networks and an option to disable auto-connect. Make sure to also remove any saved networks that you no longer use or trust to avoid accidentally connecting to them.
Manually Select Trusted Wi-Fi Networks
When connecting to a wireless network, it is important to manually select trusted networks to ensure your security. Evil twin attacks, also known as rogue AP attacks, are fraudulent attempts to access your sensitive information by creating a malicious replica of a legitimate network.
Phishing and malware distribution are common techniques used in evil twin attacks. Attackers set up a rogue wireless network with a name similar to a trusted network, tricking unsuspecting victims into connecting to it. Once connected, hackers can intercept and manipulate your wireless traffic, stealing your personal data and authentication credentials.
To protect yourself from such attacks, it is crucial to manually select trusted Wi-Fi networks. Avoid connecting to unfamiliar networks, especially those with generic or suspicious names. It is recommended to use networks that require authentication, such as those provided by reputable establishments or secured with passwords.
Always exercise caution when connecting to public Wi-Fi networks, such as those found in coffee shops, airports, or hotels. These networks are often vulnerable to evil twin attacks due to the lack of robust security measures. Before connecting, verify with the staff or the establishment’s official website for the correct network name.
In addition to manually selecting trusted networks, it is advisable to enable encryption protocols, such as WPA2, for added security. Encryption ensures that your data transmitted over the network is protected and less susceptible to hacking or spoofing attempts.
By taking these precautions and being vigilant, you can minimize the risk of falling victim to evil twin attacks and protect your personal information from unauthorized access.
In order to protect yourself from evil twin attacks, it is crucial to avoid sharing any sensitive information while connected to unsecured networks. Evil twin attacks occur when a rogue access point, disguised as a legitimate network, manipulates and intercepts the communication between a victim’s device and the network. These attacks can leave your personal data and credentials vulnerable to unauthorized access, leading to identity theft, financial fraud, and other malicious activities.
When you connect to an unsecured network, such as a public Wi-Fi hotspot, your data is transmitted over the airwaves without encryption, making it easy for hackers to intercept and manipulate. One common technique used in evil twin attacks is called spoofing, where the attacker creates a fake network that looks identical to the legitimate one. Unsuspecting users then unknowingly connect to the rogue network, giving the attacker full access to their sensitive information.
To avoid falling victim to such attacks, it is essential to be cautious while using unsecured networks and refrain from sharing any sensitive information. This includes, but is not limited to, financial details, login credentials, personal identification information, and authentication codes. Even if a network appears trustworthy, it’s important to remember that hackers can easily set up malicious networks to trick unsuspecting users.
Instead, it is recommended to use a virtual private network (VPN) when connecting to public Wi-Fi hotspots. A VPN encrypts your internet traffic and masks your IP address, making it significantly harder for attackers to intercept and decrypt your data. Additionally, always ensure that the websites you visit are secured with HTTPS, as this provides an additional layer of encryption between your device and the web server.
By following these precautions and being aware of the potential risks, you can protect yourself from evil twin attacks and ensure the security of your sensitive information. Remember, it’s always better to be safe than sorry when it comes to online security.
Avoid Online Banking and Shopping
If you want to protect yourself from evil twin attacks, it is advisable to avoid conducting online banking and shopping transactions while connected to vulnerable wireless networks. These networks can be easily manipulated by hackers who can intercept your personal information and use it for malicious purposes.
One of the main ways that hackers exploit these networks is through the use of malware. They can infiltrate your device with malware that can capture your keystrokes and steal your login credentials. This allows them to spoof your identity and gain unauthorized access to your online banking and shopping accounts.
In addition to malware attacks, evil twin attacks can also involve fraudulent authentication methods. Hackers can set up rogue access points (APs) that mimic legitimate networks, tricking unsuspecting victims into connecting to them. Once connected, they can intercept your sensitive information, such as your credit card details and login credentials.
To protect yourself from these types of attacks, it is important to be vigilant when connecting to wireless networks. Always ensure that you are connecting to a trusted network and avoid connecting to any networks with suspicious or unfamiliar names. Additionally, consider using a virtual private network (VPN) when accessing sensitive information online. A VPN encrypts your data and provides an extra layer of security, making it harder for hackers to intercept your information.
Furthermore, it is crucial to be cautious when entering your personal and financial information online. Beware of phishing attacks, where hackers create fraudulent websites that mimic legitimate banking and shopping sites. These websites often use convincing graphics and logos to trick you into entering your information, which can then be used for malicious purposes. Always double-check the URL of the website before entering any sensitive information and look for secure indicators such as the padlock symbol.
In summary, to protect yourself from evil twin attacks, it is important to avoid conducting online banking and shopping transactions while connected to vulnerable wireless networks. Be vigilant when connecting to networks, use a VPN for added security, and stay cautious of phishing attacks. By taking these precautions, you can significantly reduce your chances of falling victim to an evil twin attack.
Avoid Logging into Personal Accounts
When using a wireless network, especially in public places, it is crucial to avoid logging into your personal accounts. This is because evil twin attacks can make your personal information vulnerable to theft. An evil twin attack is a type of Wi-Fi attack where a rogue access point is set up to mimic a legitimate network, tricking victims into connecting to it.
Once connected to the evil twin network, the attacker can intercept all of your internet traffic, including usernames and passwords. This fraudulent network can then be used for various malicious purposes, such as identity theft, manipulation of your personal information, or even hacking your device with malware.
To protect yourself from such attacks, it is important to always practice safe authentication habits. Avoid entering your personal credentials, such as passwords or credit card information, when using public or unknown networks. Instead, use secure and trusted networks or consider using a virtual private network (VPN) to encrypt your connection and ensure your data remains secure.
Additionally, be cautious of any network that seems suspicious, has a weak signal, or asks for personal information before allowing access. Always double-check the network name and compare it with the official network name, especially when connecting to public Wi-Fi hotspots. It is crucial to stay vigilant and aware of potential evil twin attacks to protect yourself and your personal information from falling into the wrong hands.
In summary, logging into personal accounts on public or untrusted networks can put your data and privacy at risk. By being cautious, using secure networks, and avoiding suspicious networks, you can protect yourself from evil twin attacks and ensure the security of your personal information.
Tip #4: Keep Your Devices Updated and Secure
One of the most important steps you can take to protect yourself from evil twin attacks is to keep your devices updated and secure. By regularly updating your operating system, apps, and security software, you can ensure that you have the latest security patches and protection against known vulnerabilities.
Attackers often target victims using fraudulent wireless access points (APs) that mimic legitimate networks. These evil twin APs are set up to trick users into connecting to them, allowing the attacker to intercept their data and potentially steal sensitive information, such as login credentials or financial details.
Keeping your devices updated helps protect against these types of attacks by patching vulnerabilities that could be exploited by malicious actors. It is also important to enable strong authentication methods, such as two-factor authentication, to add an extra layer of security to your devices.
Additionally, you should be cautious when connecting to public or unfamiliar wireless networks. Avoid connecting to rogue or unsecured APs, as these are more susceptible to spoofing and manipulation by attackers. Always verify the legitimacy of the wireless network before connecting, and consider using a virtual private network (VPN) for added security.
Another important aspect of device security is the installation of reliable and up-to-date security software. Antivirus and anti-malware programs can help detect and remove malicious software that could potentially be used in an evil twin attack. Regularly scanning your devices for malware is essential for ensuring their security.
By following these tips and keeping your devices updated and secure, you can significantly reduce the risk of falling victim to evil twin attacks. Prioritizing your device’s security and staying vigilant when connecting to wireless networks will help ensure your personal and sensitive information remains protected.
Update Software and Applications Regularly
In order to protect yourself from hacking attempts and evil twin attacks, it is crucial to regularly update your software and applications. Hackers often exploit vulnerabilities in outdated software to gain unauthorized access to your devices.
By keeping your operating system, antivirus software, and applications up to date, you can ensure that you are protected against the latest threats. Regular updates often include patches and fixes that address security vulnerabilities that hackers might exploit.
Updating your software and applications is particularly important when it comes to wireless network security. Evil twin attacks, where hackers create rogue wireless access points to intercept victims’ data, can be prevented by ensuring that your wireless network authentication protocols are up to date.
Outdated software also increases the risk of falling victim to fraudulent activities such as phishing attacks and malware manipulation. Hackers may use malicious applications to gain access to your devices or steal your personal information. Regularly updating your software helps to defend against these types of attacks.
In addition to software updates, it is also essential to regularly change your passwords and avoid using the same credentials for multiple accounts. This helps protect against spoofing attacks where hackers may try to gain unauthorized access to your network or online accounts.
In conclusion, regularly updating your software and applications is a crucial step in protecting yourself from evil twin attacks and other forms of hacking. By staying proactive and ensuring that your devices are running the latest software versions, you can enhance the security of your network and prevent unauthorized access to your sensitive information.
Use Strong and Unique Passwords
One of the most important steps you can take to protect yourself from evil twin attacks is to use strong and unique passwords. A strong password is one that is difficult for others to guess or crack. It should include a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using common words or easy-to-guess sequences, such as “password123” or your birthdate. Instead, come up with a unique passphrase that is at least 12 characters long.
Using the same password for multiple accounts makes you even more vulnerable to attacks. If one account is compromised, hackers can potentially gain access to all your other accounts. Therefore, it is crucial to use unique passwords for each of your online accounts, including your Wi-Fi network. This way, even if one account is breached, the rest of your accounts and devices remain secure.
When it comes to authentication, consider enabling two-factor authentication (2FA) whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a fingerprint scan or a unique code sent to your mobile device, in addition to your password. Even if a hacker manages to steal your password through malware or a fraudulent Wi-Fi network, they would still need the second factor to gain access to your accounts.
Beware of phishing attempts and malicious websites that try to trick you into revealing your login credentials. Attackers can use evil twin attacks to create rogue wireless networks that mimic legitimate networks, fooling victims into connecting to them. Once connected, the attackers can capture your sensitive information, such as usernames and passwords, through strategies like spoofing and man-in-the-middle attacks. Always verify the legitimacy of a Wi-Fi network before connecting, especially when accessing sensitive information or making online transactions.
Regularly updating your passwords is also essential for maintaining security. Change your passwords every few months, or immediately if you suspect a breach or compromise. Additionally, consider using a password manager to securely store and generate strong passwords for all your accounts. This eliminates the need to remember multiple passwords and ensures that each password is unique and securely encrypted.
Enable Two-Factor Authentication
One of the most effective ways to protect yourself from evil twin attacks is to enable two-factor authentication. Two-factor authentication adds an extra layer of security to your online accounts, making it much harder for malicious hackers to gain access to your sensitive information.
When you enable two-factor authentication, you will typically be required to provide an additional piece of information, in addition to your password, in order to log in to your account. This could be a unique code sent to your mobile phone, a fingerprint scan, or even a facial recognition scan.
By requiring this additional step, two-factor authentication ensures that even if an attacker manages to obtain your login credentials through an evil twin attack or other means of manipulation, they won’t be able to access your account without also having physical access to your second factor of authentication.
Two-factor authentication is especially crucial when using public Wi-Fi networks, as these are often vulnerable to evil twin attacks. By enabling two-factor authentication, you can significantly reduce the risk of falling victim to fraudulent access attempts on these networks.
In addition to enabling two-factor authentication on your online accounts, it’s also important to remain vigilant for other signs of malicious activity, such as phishing scams, spoofing emails, or malware-infected devices. By staying informed and taking proactive steps to protect your security, you can greatly reduce your risk of falling victim to evil twin attacks and other forms of cybercrime.
Tip #5: Use a Firewall and Antivirus Software
One of the most important steps you can take to protect yourself from evil twin attacks is to use a firewall and antivirus software. A firewall acts as a barrier between your network and the outside world, monitoring incoming and outgoing traffic to block any unauthorized or malicious activities. By installing a firewall on your device, you can prevent hackers from gaining access to your network and manipulating or damaging your data.
In addition to a firewall, it is crucial to have reliable antivirus software installed on your device. Antivirus software helps detect and remove malware, which is often spread through evil twin attacks. Malware can infect your device and compromise your security by stealing your personal information, such as login credentials, credit card details, and other sensitive data.
When using a wireless network, especially in public places, it is essential to have both a firewall and antivirus software enabled. Evil twin attacks rely on network spoofing, where attackers create a fraudulent network that looks legitimate. Without proper security measures in place, you can easily fall victim to such an attack, unknowingly connecting to the rogue network and exposing your device to malicious activities.
Firewalls and antivirus software provide an additional layer of protection by detecting and blocking malicious activities, such as phishing attempts and other forms of hacking. They can also help protect your authentication credentials, ensuring that your online accounts remain secure.
Remember, evil twin attacks can be highly sophisticated and difficult to detect. By using a firewall and antivirus software, you can significantly reduce your vulnerability to such attacks and enhance the overall security of your device and network.
Install and Update Firewall Software
Protecting your network from evil twin attacks and other malicious activities is essential for the security of your personal and confidential information. One of the most effective ways to safeguard your network is by installing and regularly updating firewall software.
A firewall acts as a barrier between your network and the outside world, monitoring and filtering all incoming and outgoing traffic. It blocks unauthorized access attempts and prevents malicious software from infiltrating your network. By regularly updating the firewall software, you ensure that it is equipped with the latest security features and can effectively defend against new attack techniques.
Evil twin attacks often rely on network authentication spoofing, where attackers create fake wireless access points (APs) that mimic legitimate ones. These rogue APs are designed to trick victims into connecting to them, providing them with fraudulent credentials or facilitating hacking attempts.
By having a firewall installed, you can detect and block these rogue APs from accessing your network. The firewall can also detect and prevent malicious manipulation or phishing attempts that may be used to deceive users and gain unauthorized access to their devices or sensitive information.
Additionally, a firewall can protect your network from other vulnerabilities, such as malware infections. It actively scans and filters incoming data packets, identifying and blocking any potentially harmful content. This helps to prevent the spread of malware within your network and minimizes the risk of data breaches or unauthorized access.
Overall, installing and regularly updating firewall software is crucial for safeguarding your network against evil twin attacks and other malicious activities. It adds an extra layer of security by effectively monitoring, filtering, and blocking unauthorized access attempts, phishing attempts, and malicious content. By investing in a reliable firewall solution, you can significantly enhance the security of your network and protect your personal and confidential information from potential threats.
Regularly Scan for Malware and Viruses
One of the essential tips to protect yourself from evil twin attacks is to regularly scan your devices for malware and viruses. Malware refers to any malicious software designed to gain unauthorized access or cause harm to your devices or data. By scanning your devices regularly, you can detect any signs of malware or viruses that may make you vulnerable to an evil twin attack.
Evil twin attacks often involve spoofing a legitimate wireless access point (AP) to trick victims into connecting to a fraudulent network. These malicious networks are set up by hackers and can be used for various purposes, such as stealing sensitive information, manipulating data, or launching phishing attacks.
Scanning for malware and viruses can help identify any malicious software that may be present on your devices, including keyloggers, trojans, ransomware, or other types of malware that can be used in an evil twin attack.
In addition to regularly scanning your devices, it is also important to ensure that your security software is up to date. Security software helps protect against known threats and vulnerabilities, and updating it regularly can provide an additional layer of protection against evil twin attacks.
By regularly scanning for malware and viruses and keeping your security software up to date, you can reduce the risk of falling victim to an evil twin attack and better protect your sensitive information and personal data.
FAQ about topic “Protect Yourself from Evil Twin Attacks: 5 Essential Tips”
What is an evil twin attack?
An evil twin attack is a type of cyber attack where a hacker creates a fake Wi-Fi network that looks identical to a legitimate one, tricking users into connecting to it. Once connected, the attacker can intercept and steal sensitive information, such as login credentials or credit card details.
How can I identify an evil twin network?
There are several signs that can help you identify an evil twin network. Firstly, check if there are multiple networks with the same name in your vicinity. Secondly, beware of networks that have a significantly stronger signal than others in the area. Additionally, be cautious if the network requires you to re-enter your credentials even though you have previously connected to it.
What are some ways to protect myself from evil twin attacks?
There are several essential tips to protect yourself from evil twin attacks. Firstly, always verify the name and credentials of a Wi-Fi network before connecting to it. It’s best to ask an authorized person or check with the venue you’re in. Secondly, use a VPN (Virtual Private Network) to encrypt your internet traffic and protect your data from being intercepted. Lastly, keep your Wi-Fi turned off when you’re not using it to minimize the risk of connecting to a fake network.
Can I use public Wi-Fi safely?
While it’s generally not recommended to use public Wi-Fi networks due to the risk of evil twin attacks, there are measures you can take to increase your safety. Firstly, use a VPN to encrypt your traffic and protect your data from interception. Secondly, avoid accessing sensitive information, such as online banking or entering credit card details, while connected to a public Wi-Fi network. Lastly, ensure that any websites you visit are secured with HTTPS encryption.
What should I do if I suspect I’ve connected to an evil twin network?
If you suspect you’ve connected to an evil twin network, it’s important to take immediate action to protect your information. Firstly, disconnect from the suspicious network as soon as possible. Secondly, change the passwords for any accounts you accessed while connected to the network. Finally, monitor your accounts and bank statements for any unusual activity, and consider reporting the incident to the appropriate authorities or your internet service provider.


