The 4 Way Handshake is a critical component of secure networking, especially when it comes to ensuring the privacy and integrity of the communication between a server and a client. This process involves a series of steps that allow for the exchange of authentication keys and the establishment of a secure connection. However, it also presents various challenges in terms of security and encryption protocols.
One of the primary purposes of the 4 Way Handshake is to authenticate both the server and the client, ensuring that they are legitimate entities and not potential threats. This authentication is achieved through the exchange of encryption keys, which are used to encrypt and decrypt the data being transmitted. Without this authentication process, the communication between the server and the client would be vulnerable to interception and unauthorized access.
Another challenge in the 4 Way Handshake is ensuring the confidentiality and integrity of the communication. This is achieved through the use of encryption ciphers, which scramble the data in a way that can only be unscrambled with the correct encryption key. The encryption also ensures that the data remains intact and unaltered during transmission, providing a way to confirm the integrity of the communication.
Overall, the 4 Way Handshake plays a crucial role in establishing a secure and reliable connection between a server and a client. By authenticating both entities and enabling the secure exchange of encryption keys, it ensures the privacy and integrity of the communication. However, it also presents several challenges in terms of security, encryption protocols, and maintaining the confidentiality of the data being transmitted.
Contents
- 1 What is a 4 Way Handshake?
- 2 Importance of the 4 Way Handshake
- 3 Understanding the Process
- 4 Common Issues and Troubleshooting
- 5 Security Considerations
- 6 FAQ about topic “Understanding the 4 Way Handshake in Networking: A Comprehensive Guide”
- 7 What is a 4-way handshake in networking?
- 8 Why is a 4-way handshake important in networking?
- 9
- 10
- 11 How does a 4-way handshake differ from a 3-way handshake?
What is a 4 Way Handshake?
A 4 Way Handshake is an exchange that takes place between a client and a server in computer networking. It is a process of establishing a secure communication session by ensuring the integrity and privacy of the data being transmitted.
The 4 Way Handshake involves a series of challenges and responses that use encryption ciphers and keys to confirm the identity of both the client and the server. This ensures that no unauthorized entities can intercept or modify the communication.
The purpose of the 4 Way Handshake is to establish a secure connection between the client and the server, allowing them to exchange data in a protected environment. It is a crucial step in ensuring the security and integrity of network communication.
The 4 Way Handshake protocol works by using cryptographic algorithms to generate session keys that are unique to each communication session. These session keys are used to encrypt and decrypt the data being transmitted, providing an additional layer of security.
During the 4 Way Handshake, the client and the server exchange messages to negotiate the encryption ciphers and keys to be used for the communication. They also verify each other’s identity through the use of digital certificates or other authentication mechanisms.
Once the 4 Way Handshake is successfully completed, the client and the server have established a secure and encrypted communication channel. This allows them to exchange data with confidence, knowing that their privacy and the integrity of their data are protected.
Importance of the 4 Way Handshake
The 4 Way Handshake is a critical component of secure communication in networking. It is a process that allows two parties to exchange information in a secure and authenticated manner. This handshake establishes trust and ensures the integrity of the communication.
Authentication is an essential aspect of any security protocol, and the 4 Way Handshake plays a crucial role in this process. By exchanging specific messages, both the client and server can confirm their identities and establish a secure connection. This authentication step helps prevent unauthorized access and protects sensitive information from falling into the wrong hands.
The handshake also enables the establishment of encryption keys, which are necessary for securing the communication session. During the exchange, the client and server negotiate suitable encryption algorithms and other parameters, ensuring that all data transmitted between them remains confidential. The use of encryption ciphers further enhances the security and privacy of the communication.
Moreover, the 4 Way Handshake tackles the challenges that might arise during the networking session. It allows for the verification of data integrity, ensuring that information sent between the client and server has not been tampered with during transmission. This step adds an extra layer of security and guarantees the reliability of the communication.
In summary, the 4 Way Handshake is a vital protocol in networking that enables secure and authenticated communication. By establishing trust, confirming identities, and exchanging encryption keys, it ensures the confidentiality, integrity, and privacy of the data transmitted between the client and server. This handshake also addresses communication challenges and verifies the integrity of the exchanged information. Without the 4 Way Handshake, network communication would be vulnerable to unauthorized access and data breaches.
Understanding the Process
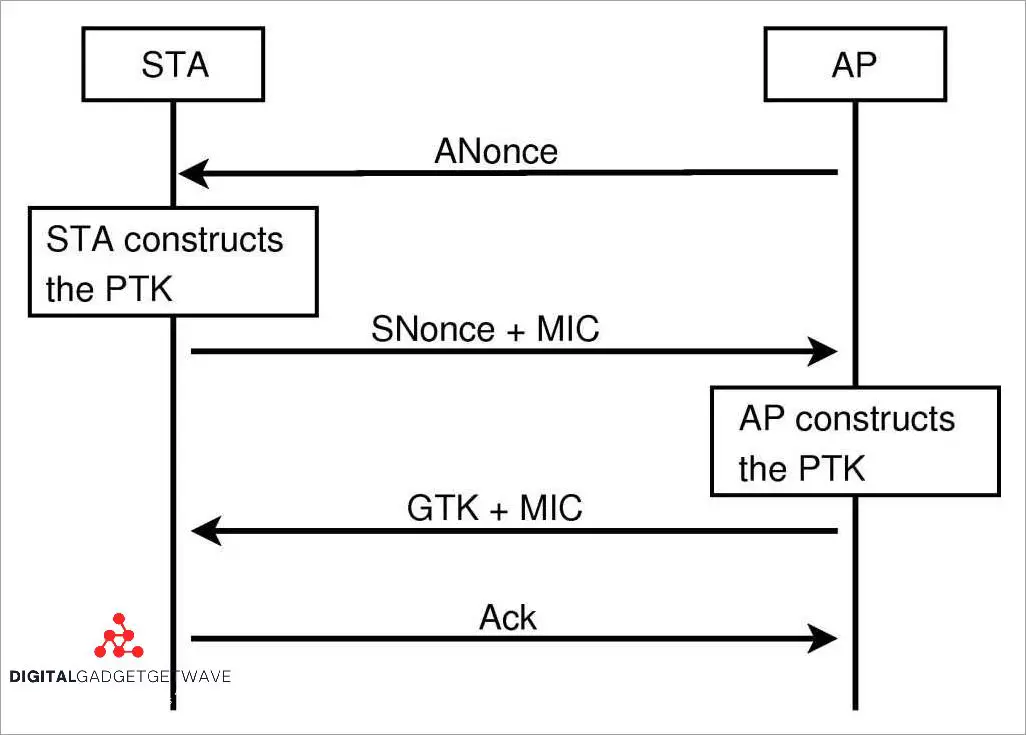
In networking, the 4-way handshake is a secure protocol used to establish a secure channel between a client and a server. It is an essential part of ensuring the security and integrity of the communication session.
The handshake process involves a series of exchanges between the client and the server. During this exchange, both parties confirm their identities and establish a shared secret key that will be used for encryption and decryption.
One of the key challenges in the handshake process is ensuring the privacy and authentication of the communication. To address this, the handshake uses encryption ciphers to protect the exchanged data from unauthorized access.
During the handshake, the client and the server exchange messages to confirm each other’s identities and establish a secure connection. The messages exchanged include information about the supported encryption algorithms and cryptographic suites, ensuring that both parties are capable of communicating securely.
The handshake process also includes the generation and exchange of session keys. These keys are used for encrypting and decrypting the data transmitted between the client and the server. The session keys are unique to each communication session and are generated based on the agreed encryption algorithm and the shared secret key.
By completing the 4-way handshake, the client and the server establish a secure and trusted connection, ensuring the confidentiality, integrity, and privacy of the data exchanged during the communication session. This process helps to prevent unauthorized access and maintain the security of the network.
Step 1: Client Request for Connection
In the first step of the 4-way handshake protocol, the client initiates the communication by sending a request for connection to the server. This request is essential for establishing a secure and encrypted channel between the client and the server.
During this step, the client sends a message to the server, indicating its intention to establish a connection. The message includes various parameters, such as the client’s identity, the desired communication parameters, and any additional information required for the server to process the request.
To ensure the integrity and privacy of the communication, the request message is typically encrypted using secure cryptographic algorithms and ciphers. This encryption helps prevent unauthorized access or tampering of the client’s request, ensuring the confidentiality of the exchanged information.
The client may also include authentication tokens or certificates to establish its identity and prove its authenticity to the server. This authentication step enhances the security of the communication by allowing the server to confirm the client’s legitimacy before proceeding with the handshake.
Additionally, the client request may include challenges or unique identifiers that are used by the server to generate session keys or perform further security checks. These challenges provide an additional layer of security and help prevent replay attacks or unauthorized access.
Step 2: Server Response and Authentication
After the initial request from the client, the server responds with a message that includes its authentication and establishes the encrypted communication. This step is crucial for ensuring the security and integrity of the data exchange between the client and server.
The server’s response includes the chosen encryption cipher and other parameters necessary for the client and server to establish a secure session. The authentication process confirms the identity of the server, providing assurance to the client that it is communicating with the intended server and not an imposter.
During the authentication process, the server may request the client to provide its digital certificate, which contains keys that are used for encryption and decryption. The server then verifies the client’s certificate to ensure it is valid and matches the expected credentials.
Once the server’s response and authentication are completed, the client and server proceed with the key exchange, where they exchange cryptographic keys that will be used for encrypting and decrypting the data during the session. This exchange of keys contributes to the establishment of a secure communication channel, ensuring the privacy and integrity of the transmitted data.
The server response and authentication phase is a critical part of the handshake protocol, as it establishes the foundation for secure communication between the client and server. It ensures that both parties are who they claim to be, encrypts the data transmission, and establishes the parameters and keys necessary for the session.
Step 3: Encryption and Key Exchange
Once the client and server have successfully completed the authentication process in the 4-way handshake, they move on to the next crucial step: encryption and key exchange. This step aims to establish a secure session for the communication between the client and server, ensuring privacy, integrity, and authenticity of the data transmitted.
One of the challenges in this step is to select appropriate encryption algorithms and ciphers that provide strong security while also being efficient enough for the networking environment. The client and server need to agree on a common set of encryption protocols and ciphers to ensure compatibility.
The encryption and key exchange process typically involves the client and server exchanging encryption keys, which are used to encode and decode the data being transmitted. These keys are generated using encryption algorithms that provide secure random numbers. The client and server may also use a protocol like the Diffie-Hellman key exchange to securely exchange the keys.
During the encryption and key exchange phase, both the client and server confirm each other’s identities and establish a shared secret key. This shared key is used for encryption and decryption of the data sent between them. Additionally, the integrity of the data is ensured by using methods like message authentication codes (MACs) to detect any tampering or unauthorized modifications.
The encryption and key exchange step is critical in establishing a secure and reliable communication session between the client and server. Without proper encryption and key exchange, the data transmitted over the network would be vulnerable to eavesdropping and unauthorized access. By securing this step in the handshake, the client and server can ensure the privacy and integrity of their communication.
Step 4: Connection Established
Once the client and server successfully complete the three-way handshake and exchange the necessary information, the fourth and final step of the handshake process begins – establishing a secure and encrypted communication session between the two parties. This step is crucial for ensuring the integrity, privacy, and security of the data being transmitted over the network.
During this phase, the client and server confirm their authentication and establish a shared set of secret keys for encryption and decryption of data. These keys are generated using cryptographic algorithms and are unique to the current session. They are used to encrypt the data before sending it over the network and decrypt it upon receipt, ensuring that only the intended recipient can access the information.
The establishment of a secure and encrypted connection also ensures that the communication between the client and server is protected from any unauthorized access or tampering. By encrypting the data, it becomes extremely difficult for hackers or eavesdroppers to intercept or decipher the information being transmitted, adding an additional layer of security to the communication protocol.
The fourth step of the handshake process not only establishes a connection between the client and server, but also sets up the necessary security measures to safeguard the data being exchanged. This ensures that both parties can communicate securely and reliably, without the fear of any potential threats to the privacy or integrity of their information.
Common Issues and Troubleshooting
When dealing with the 4-way handshake protocol, there are several common issues that may arise, requiring troubleshooting to maintain a secure and reliable communication session.
Authentication Challenges: One common issue involves authentication challenges between the client and server. This can occur when the client’s credentials are incorrect or when there is a mismatch in the authentication methods used by the client and server. Troubleshooting this issue may involve double-checking the credentials and ensuring that the client and server are using compatible authentication protocols.
Encryption Key Exchange: Another common issue is the failed exchange of encryption keys during the handshake process. Encryption is crucial for ensuring the privacy and integrity of the communication session. If the encryption keys are not properly established, the communication may be vulnerable to eavesdropping and tampering. Troubleshooting this issue may involve verifying that the encryption algorithms and ciphers used by the client and server are compatible and correctly configured.
Failure to Confirm Identity: Sometimes, the handshake may fail to confirm the identity of the server. This can happen when the server’s digital certificate is not trusted or when there is a mismatch in the server’s identity information. Troubleshooting this issue may involve checking the validity and authenticity of the server’s digital certificate and ensuring that the client trusts the certificate issuer.
Integrity and Security: One critical aspect of the handshake is maintaining the integrity and security of the communication session. Common issues in this regard include data corruption, unauthorized access, or interception of the communication. Troubleshooting may involve examining network logs, checking for any signs of unauthorized access or data manipulation, and implementing additional security measures such as implementing intrusion detection systems or using stronger encryption algorithms.
In conclusion, understanding the common issues and troubleshooting methods related to the 4-way handshake protocol is essential for establishing a secure and reliable communication session. By addressing these challenges and ensuring the proper configuration of authentication, encryption, and identity confirmation, network administrators can enhance the privacy and security of their network communications.
Connection Timeout
In networking, the process of establishing a connection between a client and a server involves a series of steps known as a handshake. One of the challenges that can arise during this handshake is a connection timeout.
During the handshake, the client and server exchange a series of messages to confirm their identities, establish the session keys, and ensure the security and integrity of the communication. This process involves the use of encryption ciphers and authentication protocols to secure the connection.
However, sometimes the handshake process can take longer than expected, and if it exceeds a certain time limit, a connection timeout occurs. This can happen due to various factors, such as network congestion, server overload, or a slow response from either the client or server.
When a connection timeout occurs, it means that the client and server were unable to establish a connection within the specified time frame. This can result in failed authentication, loss of privacy, and compromised security of the communication. In such cases, it is important to diagnose the issue and address any underlying problems to ensure a successful handshake and establish a secure connection.
To mitigate connection timeouts, network administrators can implement measures such as optimizing network performance, increasing server resources and capacity, or adjusting the handshake protocol parameters to allow for longer timeouts or more efficient exchanges of messages. By addressing these challenges, the handshake process can be completed successfully, ensuring a secure and reliable connection between the client and server.
Incorrect Credentials
When a client attempts to establish a secure communication session with a server, it is important for both parties to be able to authenticate each other. This authentication process is a crucial step in ensuring the privacy and integrity of the communication. However, there are cases when the client fails to provide the correct credentials during the initial handshake.
The handshake is a series of steps where the client and the server exchange information to confirm their identities and establish a secure connection. It involves the negotiation of encryption ciphers, the exchange of security keys, and the verification of data integrity. If the client provides incorrect credentials, the server will not be able to authenticate the client, and the handshake process will fail.
Incorrect credentials can be a result of various challenges. It could be due to typing errors, forgotten passwords, or expired user accounts. In any case, the server will reject the client’s attempt to establish a secure connection until the correct credentials are provided.
Security protocols like the 4-way handshake ensure that only authorized clients can access a server by requiring correct credentials. This level of authentication helps prevent unauthorized access to sensitive information and ensures that the communication between the client and the server is secure.
Interference and Signal Issues
When it comes to wireless networks, interference and signal issues can pose significant challenges to the proper functioning of the 4-way handshake protocol. These issues can impact the privacy, authentication, and overall security of the communication between a client and a server.
Interference can occur when there are multiple devices operating on the same frequency, causing overlapping signals that can disrupt the exchange of information during the handshake process. This interference can result in lost or corrupted packets, leading to delays or even a failed handshake.
Signal issues, such as weak or unstable signals, can also affect the successful establishment of a secure connection. If the signal strength is insufficient, the client and server may experience difficulties in exchanging the necessary encryption ciphers and confirming the authenticity of their respective keys. This can compromise the security and integrity of the session, making it vulnerable to unauthorized access or data manipulation.
To mitigate interference and signal issues, various techniques and technologies can be employed. For example, using advanced modulation schemes and error correction mechanisms can help overcome signal degradation caused by distance or physical obstructions. Additionally, implementing proper signal encryption can enhance security and minimize the risk of eavesdropping or interception.
In conclusion, interference and signal issues can greatly impact the effectiveness and security of the 4-way handshake protocol. It is crucial for network administrators and security professionals to address these challenges appropriately and implement measures to ensure the reliable and secure exchange of information between clients and servers.
Security Considerations
When it comes to the 4-way handshake in networking, security is of paramount importance. The handshake process is designed to establish a secure and authenticated communication session between a client and a server. It protects the integrity and privacy of the exchanged data by using encryption and authentication mechanisms.
One of the main security challenges is ensuring the confidentiality of the exchanged information. To achieve this, the handshake protocol utilizes cryptographic techniques to encrypt the data being transmitted. Secure keys are used to encrypt and decrypt the information, ensuring that only authorized parties can read and understand it.
Another crucial aspect of the handshake is the authentication process. Both the client and the server need to confirm their identities to establish trust. This is done by exchanging authentication credentials, such as certificates or passwords, and validating them using a trusted authority. The authentication process ensures that only authorized parties can participate in the communication session.
In addition to confidentiality and authentication, the handshake protocol also addresses the issue of data integrity. Through the use of cryptographic algorithms and ciphers, the exchanged data is protected against unauthorized modifications. This ensures that the information remains intact and unaltered during the transmission.
To enhance the security of the handshake, it is recommended to use strong and secure ciphers. These ciphers provide advanced encryption and authentication algorithms, making it more difficult for attackers to compromise the communication session. Regularly updating the ciphers and encryption protocols further strengthens the security of the handshake process.
In summary, the security considerations of the 4-way handshake in networking are crucial to establish a secure and trusted communication session. The integrity, confidentiality, and authentication of the exchanged data are ensured through encryption, authentication mechanisms, and strong ciphers. By taking into account these security considerations, the handshake protocol can effectively protect the privacy of the communication session and mitigate potential security risks.
Protecting Against Man-in-the-Middle Attacks
The 4-way handshake in networking is a crucial process that establishes a secure session between a client and a server. However, it is susceptible to a potential security threat known as a man-in-the-middle attack. This type of attack occurs when a malicious third party intercepts and alters the communication between the client and the server, compromising the privacy and integrity of the exchanged data.
To protect against man-in-the-middle attacks, various security measures can be implemented. One of the most important steps is the authentication of both the client and the server during the handshake. This is typically done using cryptographic protocols that validate the identity of each party involved in the communication. By confirming the authenticity of the client and server, the risk of an attacker infiltrating the connection is greatly reduced.
In addition to authentication, the use of encryption is vital in securing the session. The exchanged data can be encrypted using strong ciphers and keys, ensuring that it remains confidential and inaccessible to unauthorized individuals. Encryption also helps to prevent tampering or alteration of the data during transmission, maintaining its integrity.
Another important aspect of protecting against man-in-the-middle attacks is the careful selection of security protocols. It is crucial to choose protocols that have been thoroughly tested and proven to be secure. Additionally, regular updates and patches should be applied to eliminate any known vulnerabilities. By staying up to date with the latest security measures, the risk of falling victim to a man-in-the-middle attack can be significantly reduced.
Overall, protecting against man-in-the-middle attacks requires a combination of strong authentication, encryption, and adherence to secure protocols. By implementing these measures, the privacy, integrity, and security of the communication can be effectively safeguarded, ensuring a secure and reliable networking environment.
Choosing Strong Encryption Algorithms
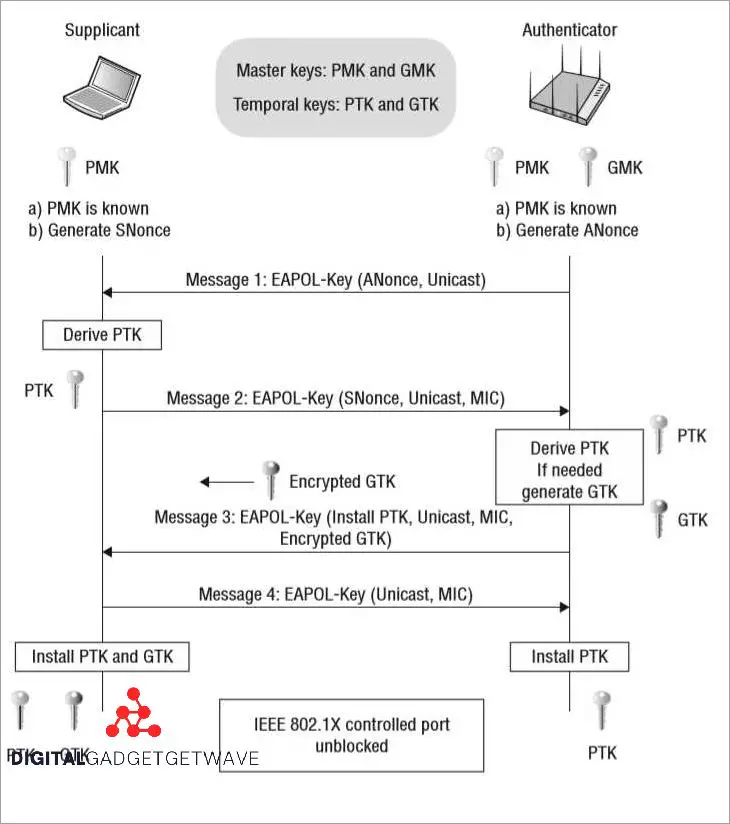
When it comes to securing the communication between a client and a server in networking, choosing strong encryption algorithms is crucial. Encryption is the process of converting plain text into cipher text to protect the privacy and integrity of the data transmitted over the network.
In the context of the 4-way handshake, encryption plays a vital role in establishing a secure session between the client and the server. Both parties need to select a suitable encryption algorithm to ensure secure and confidential communication.
One of the challenges in choosing a strong encryption algorithm is the balance between security and performance. While there are numerous ciphers available, not all of them provide the same level of security. It is essential to consider factors such as the encryption strength, computational overhead, and compatibility with the network protocol.
Authentication is another crucial aspect when choosing encryption algorithms. The selected algorithm should support authentication methods that confirm the identity of both the client and the server. This ensures that the entities involved in the communication are legitimate and can be trusted.
Furthermore, encryption algorithms should also consider key exchange mechanisms. The secure exchange of session keys between the client and the server is essential to establish encrypted communication. The chosen encryption algorithm should have a robust mechanism for generating and exchanging keys securely.
In summary, choosing strong encryption algorithms is vital for secure networking. It involves considering factors such as encryption strength, authentication, key exchange mechanisms, and compatibility with the network protocol. By selecting the right encryption algorithms, it ensures secure and confidential communication, protecting the privacy and integrity of the data exchanged between the client and the server.
FAQ about topic “Understanding the 4 Way Handshake in Networking: A Comprehensive Guide”
What is a 4-way handshake in networking?
A 4-way handshake is a process used in wireless networking to establish a secure connection between a client device and a wireless access point. It consists of a series of messages exchanged between the client and the access point to authenticate and negotiate security parameters.
Why is a 4-way handshake important in networking?
A 4-way handshake is important in networking because it ensures that only authorized devices can connect to a wireless network. It provides a secure method for the client and the access point to verify each other’s identities and establish a shared encryption key to protect the communication between them.
How does a 4-way handshake differ from a 3-way handshake?
A 4-way handshake is used in wireless networking to establish a secure connection, while a 3-way handshake is used in TCP/IP networking to establish a reliable connection. In a 3-way handshake, the client and the server exchange three messages to synchronize their sequence numbers and establish a TCP connection. In a 4-way handshake, the client and the access point exchange four messages to authenticate and negotiate security parameters.


