
A virtual private gateway (VPG) is a crucial component of a virtual private network (VPN) that enables secure access to a private network over the internet. It acts as a firewall and server, providing encryption and authentication protocols for secure data transmission.
With a VPG, users can connect their local networks to a cloud-based infrastructure, allowing them to access resources and services securely. It works by establishing a secure connection between the user’s network and the cloud provider’s network, creating a virtual private network tunnel for data transfer.
The primary purpose of a VPG is to ensure the privacy and security of the data being transmitted between the user and the cloud provider’s network. It creates a secure gateway between the two networks, routing all traffic through an encrypted connection.
When a user sends data over the internet, the VPG encrypts the data before transmitting it to the cloud provider’s network. This ensures that even if the data is intercepted, it remains unreadable and protected from unauthorized access.
Furthermore, a VPG provides network routing capabilities, allowing users to control the flow of traffic between their local network and the cloud provider’s network. It acts as a bridge between the two networks, directing data packets to the appropriate destinations based on routing rules.
In summary, a virtual private gateway plays a crucial role in ensuring secure access to a private network over the internet. It provides encryption, authentication, firewall, and routing capabilities, allowing users to establish a secure connection and protect their data from unauthorized access.
Contents
- 1 The Importance of Virtual Private Gateway
- 2 Benefits of Virtual Private Gateway
- 3 How Does a Virtual Private Gateway Work?
- 4 Establishing a connection
- 5 Transmitting data securely
- 6 Routing data to the destination
- 7 When Should You Use a Virtual Private Gateway?
- 8 Connecting multiple networks
- 9 Ensuring secure communication
- 10 FAQ about topic “Understanding the Virtual Private Gateway: A Comprehensive Guide to its Functionality and Operations”
- 11 What is a Virtual Private Gateway?
- 12 How does a Virtual Private Gateway work?
- 13 What are the benefits of using a Virtual Private Gateway?
- 14 Can a Virtual Private Gateway be used with multiple VPCs?
- 15 What are the alternatives to using a Virtual Private Gateway?
The Importance of Virtual Private Gateway
A Virtual Private Gateway plays a crucial role in maintaining the security and privacy of a virtual network. It acts as a connection point between a virtual private network (VPN) and other networks, facilitating the flow of traffic and ensuring that data is transferred securely.
One of the key benefits of a Virtual Private Gateway is its ability to authenticate and encrypt data. By using strong encryption protocols and establishing a secure tunnel, it protects sensitive information from unauthorized access or interception while in transit. This is particularly vital when accessing cloud resources or communicating over the internet, where data is vulnerable to attacks.
In addition to providing a secure and private connection, a Virtual Private Gateway also enables routing capabilities. It allows for the seamless transfer of data between the virtual network and other networks, such as an on-premises server or a cloud service provider. This enables efficient communication and data exchange, supporting the overall functionality and performance of the network.
Another important aspect of a Virtual Private Gateway is its firewall capabilities. It acts as a barrier between different networks, filtering and managing incoming and outgoing traffic. This ensures that only authorized data can enter or leave the virtual network, providing an additional layer of security against potential threats or malicious activities.
Overall, a Virtual Private Gateway plays a critical role in ensuring the security, privacy, and efficient functioning of a virtual network. By establishing a secure connection, encrypting data, and managing traffic, it enables organizations to securely access cloud resources, communicate over the internet, and protect their sensitive information from unauthorized access or interception.
Benefits of Virtual Private Gateway
A Virtual Private Gateway (VPG) offers a number of benefits for organizations looking to secure their network and data. Here are some of the key advantages:
- Enhanced Security: A VPG provides a secure protocol for connecting to a virtual private network (VPN). This ensures that all data sent between the user and the network is encrypted and protected from unauthorized access.
- Access Control: With a VPG, organizations can establish granular access controls, allowing them to restrict access to specific resources or services based on user roles and privileges. This helps ensure that only authorized individuals can access sensitive information.
- Virtual Networking: By using a VPG, organizations can create a virtual network that is isolated from the rest of the internet. This provides an added layer of security by preventing unauthorized access to the network.
- Secure Connection: The VPG establishes a secure connection between the user’s device and the network, creating a virtual tunnel through which all data traffic flows. This prevents hackers or other malicious entities from intercepting or tampering with the data.
- Firewall Protection: In addition to encryption, a VPG can also provide firewall protection, which helps block unauthorized access to the network. This ensures that only trusted connections are allowed and helps prevent attacks from malicious actors.
- Efficient Routing: A VPG can optimize network routing, ensuring that data packets are sent through the most efficient and reliable paths. This helps minimize latency and ensure optimal performance for users accessing resources on the network.
- Authentication: A VPG allows for strong user authentication, ensuring that only authorized individuals can access the network. This can be done through various authentication methods, such as username and password, two-factor authentication, or digital certificates.
- Cloud Integration: A VPG can be seamlessly integrated with cloud service providers, allowing organizations to securely access their cloud resources and services. This enables organizations to leverage the scalability and flexibility of the cloud while maintaining a high level of security for their data.
Overall, a Virtual Private Gateway offers organizations a secure and efficient way to connect to their private network, ensuring the confidentiality, integrity, and availability of their data. By implementing a VPG, organizations can protect their sensitive information and mitigate the risk of unauthorized access or data breaches.
Secure and private network connection
A Virtual Private Gateway (VPG) provides a secure and private network connection by establishing a virtual private network (VPN) tunnel over the internet. This tunnel ensures that the data transmitted between the VPG and the authorized users is encrypted and protected from unauthorized access.
Authentication is an important aspect of a secure network connection. The VPG utilizes various authentication mechanisms, such as certificates or pre-shared keys, to verify the identity of the users and ensure that only authorized individuals can access the private network.
Once the authentication process is complete, the VPG acts as a gateway, allowing the authorized users to securely access resources and services within the private network. It acts as a bridge between the user’s device and the cloud provider’s network.
One of the key components of a secure network connection is encryption. The VPG uses encryption protocols to encode the data transmitted between the user’s device and the private network. This ensures that even if the data is intercepted, it cannot be deciphered without the encryption key.
In addition to encryption, the VPG also provides firewall capabilities. It monitors the incoming and outgoing traffic and applies various rules and policies to protect the private network from unauthorized access or malicious activities.
The VPG also plays a crucial role in routing the traffic between the user’s device and the private network. It ensures that the data packets are properly directed to their intended destinations within the private network, ensuring efficient and secure communication.
By establishing a virtual private network connection, the VPG ensures that the user’s data remains private and secure, even when transmitted over the internet. It provides a secure and encrypted tunnel through which the user can access resources and services within the private network, without exposing sensitive information to potential threats.
Integration with multiple cloud services
A virtual private gateway provides a secure and reliable connection between a private network and multiple cloud services. With this integration, organizations can access and exchange data with cloud providers such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform.
Using a virtual private gateway, organizations can establish a private and encrypted connection over the internet to the cloud provider’s network. This connection is typically established using a VPN (Virtual Private Network) protocol, ensuring that the data transmitted between the private network and the cloud remains secure and protected.
Once the virtual private gateway is configured, it acts as a gateway for all traffic between the private network and the cloud services. It routes the data packets from the private network to the appropriate cloud services, allowing the organization to seamlessly access and use the cloud resources.
The virtual private gateway also helps in maintaining network security by acting as a firewall. It can inspect the incoming and outgoing data packets, ensuring that only authorized traffic is allowed through and blocking any potential threats. This adds an extra layer of protection to the organization’s network and data.
In addition to traffic routing and firewall capabilities, the virtual private gateway provides secure access to cloud resources. It uses encryption and tunneling techniques to create a secure and private network connection, preventing unauthorized access or interception of data. It also supports authentication mechanisms to ensure that only authorized users can access the cloud services.
The integration with multiple cloud services allows organizations to leverage the benefits of different cloud providers without the need for separate connectivity solutions. They can easily manage and control the flow of data between their private network and the cloud services, ensuring efficient utilization of resources and improved productivity.
In summary, a virtual private gateway acts as a secure and reliable gateway between a private network and multiple cloud services. It enables seamless integration and exchange of data, provides network security features, and allows organizations to efficiently access and utilize cloud resources.
How Does a Virtual Private Gateway Work?
A virtual private gateway (VPG) is a networking component in the cloud that provides access to a private network from a virtual private cloud (VPC). It acts as a gateway between the VPC and other networks, such as on-premises networks or the internet.
One of the key functions of a VPG is to establish an encrypted tunnel for secure communication between the VPC and other networks. This helps protect the privacy and integrity of data transmitted over the network. The VPG also acts as a firewall, filtering and inspecting incoming and outgoing traffic to enforce security policies.
When a data packet is sent from a virtual server within the VPC, it is encapsulated in an IPsec tunnel and forwarded to the VPG. The VPG then decrypts the packet, checks the routing information, and forwards it to the appropriate destination. Similarly, when a response is received, the VPG encrypts the packet and forwards it back to the virtual server.
The VPG can be configured to allow or deny certain types of traffic based on predefined rules. It can also handle network address translation (NAT) to translate between private IP addresses used within the VPC and public IP addresses used on the internet. This allows the VPC to communicate securely with external networks without exposing its internal addressing scheme.
Authentication and authorization mechanisms can be implemented within the VPG to control access to the private network. This ensures that only authorized users or devices can establish a connection and access resources within the VPC.
In summary, a virtual private gateway acts as a secure and private entry point to a virtual private cloud. It provides encryption, firewall capabilities, routing, and access control mechanisms to ensure the security and integrity of data transmitted between the VPC and other networks.
Establishing a connection
The process of establishing a connection through a Virtual Private Gateway involves several steps to ensure authentication, access, and security for data transmission.
Firstly, the virtual private gateway acts as an encryption point between the user’s internet connection and the cloud provider’s server. It establishes a secure tunnel through which the user’s data can pass. This tunnel is encrypted using various protocols to provide a high level of security.
The virtual private gateway also plays a crucial role in routing the traffic between the user’s network and the cloud provider’s network. It acts as a bridge between the two, allowing the user’s data to travel safely and efficiently.
During the connection establishment process, the virtual private gateway performs authentication to verify the identity of the user and determine the level of access they have to the cloud resources. This authentication can be done using various methods such as username and password, digital certificates, or multifactor authentication.
Once the user is authenticated, the virtual private gateway creates a private and secure connection, usually referred to as a tunnel, between the user’s network and the cloud provider’s network. This tunnel ensures that all data transmitted between the two networks is encrypted and protected from unauthorized access.
Furthermore, the virtual private gateway also acts as a firewall, filtering and monitoring the incoming and outgoing traffic between the user’s network and the cloud resources. It provides an added layer of security by inspecting the data packets and blocking any malicious or unauthorized traffic.
Connection authentication
Connection authentication is a crucial aspect of a virtual private gateway (VPN) setup. It ensures that only authorized users can access the private network and that the data transmitted between the user and the network remains secure.
In a VPN setup, connection authentication is typically achieved through the use of encryption and authentication protocols. These protocols, such as the popular IPsec (Internet Protocol Security), establish a secure tunnel between the user’s device and the VPN server.
When a user wants to access the private network, they must first establish a connection to the VPN server using the authentication protocol. This process verifies the user’s identity and ensures that they have the necessary permissions to access the network.
Once the connection is authenticated, all traffic between the user’s device and the VPN server is encrypted using encryption algorithms such as AES (Advanced Encryption Standard). This ensures that even if the data is intercepted, it cannot be read without the decryption key.
In addition to authentication and encryption, a virtual private gateway also provides other security measures. It may include a firewall to filter incoming and outgoing traffic, preventing unauthorized access to the network. The gateway may also include routing functionality to direct traffic within the network and ensure efficient data transfer.
By implementing connection authentication in a virtual private gateway, organizations can ensure that only authorized users can access their private network. This helps protect sensitive data and provides an additional layer of security against external threats. Whether it’s for remote employees accessing company resources or for secure cloud connections, a virtual private gateway with strong connection authentication is essential for network security and data protection.
Transmitting data securely
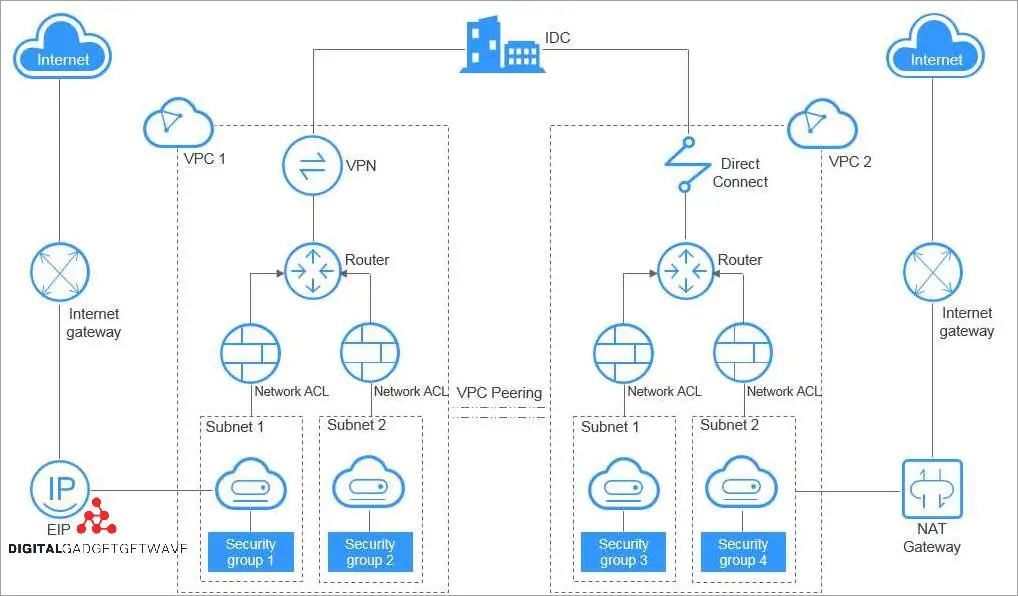
When transmitting data over a private network, security is of utmost importance. A virtual private gateway (VPG) helps ensure the secure transmission of data by establishing a private connection between a user’s local network and a cloud provider’s network.
Routing protocols, such as VPN (Virtual Private Network), allow for the encryption of data traffic and create a secure tunnel between the user’s network and the virtual private gateway. This ensures that all data transmitted between the user’s network and the cloud provider’s network is encrypted and protected from unauthorized access.
The virtual private gateway acts as a gateway or access point to the cloud provider’s network, allowing users to securely access resources and services hosted in the cloud. It authenticates users and provides a secure connection that extends the user’s network onto the internet, while keeping data secure.
By utilizing encryption protocols and authentication mechanisms, the virtual private gateway ensures that sensitive data remains confidential and protected from interception or tampering. This enhances the overall security of the user’s network and helps prevent unauthorized access to valuable data.
Additionally, the virtual private gateway offers a level of control and visibility over the data traffic flowing between the user’s network and the cloud provider’s network. It allows for the monitoring and management of network traffic, providing insights into the flow of data and ensuring that any potential security threats are promptly detected and addressed.
In summary, a virtual private gateway plays a critical role in securely transmitting data over a private network by establishing a secure connection, encrypting data traffic, providing authentication, and giving users control over their network traffic. It ensures the security and integrity of data, making it an essential component in building a secure and reliable network infrastructure.
Encryption protocols
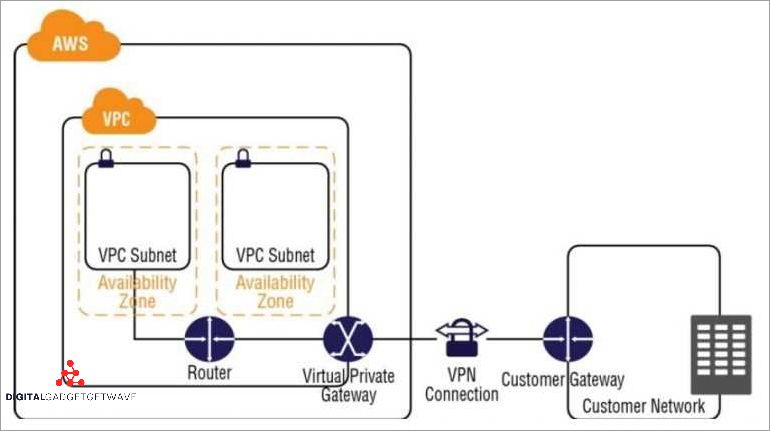
In the context of Virtual Private Gateway (VPG), encryption protocols play a crucial role in ensuring the security of data transmitted over a VPN connection. These protocols enable the establishment of a secure and encrypted tunnel between the client’s device and the VPG server in the cloud.
The most commonly used encryption protocols for VPN connections are IPsec (Internet Protocol Security) and SSL/TLS (Secure Sockets Layer/Transport Layer Security). These protocols provide a robust level of encryption and authentication to protect sensitive data from unauthorized access.
IPsec is a widely adopted protocol that operates at the network layer of the OSI model. It uses encryption algorithms, such as AES (Advanced Encryption Standard), to secure the data transmitted between the client’s device and the VPG gateway. IPsec also provides authentication through the use of digital certificates or pre-shared keys, ensuring that only authorized devices have access to the VPN.
SSL/TLS, on the other hand, operates at the application layer of the OSI model and is commonly used for securing web traffic. It uses cryptographic algorithms, such as RSA (Rivest-Shamir-Adleman) and AES, to encrypt data transmitted between the client’s device and the VPG server. SSL/TLS also provides authentication through the use of digital certificates, ensuring the identity of the server.
These encryption protocols not only protect data in transit but also address other security concerns. For example, they establish a secure connection that prevents unauthorized access or tampering with the data. They also provide secure routing by encrypting the traffic that passes through the VPG gateway, making it difficult for attackers to intercept or sniff the data.
By implementing strong encryption protocols, a Virtual Private Gateway ensures the confidentiality, integrity, and authenticity of the data transmitted over the VPN connection. It creates a private and secure network that allows authorized users to access cloud resources while keeping their data protected from potential security threats on the internet.
Data integrity checks
Data integrity checks are an essential part of ensuring the security and reliability of data transmitted through a Virtual Private Gateway (VPG). These checks help to verify that the data being transmitted has not been tampered with or corrupted during the routing process.
One of the most common methods used for data integrity checks is through the use of cryptographic algorithms. These algorithms generate unique hash values for each packet of data, which are then compared at the receiving end to ensure that the data has not been altered in transit. This ensures that the data being transmitted is authentic and has not been modified by unauthorized parties.
In addition to cryptographic algorithms, data integrity checks can also involve the use of checksums. Checksums are small pieces of data that are calculated based on the contents of a packet, and are used to provide a quick and simple way to verify the integrity of the data. They can be used to detect any errors or corruption that may have occurred during the transmission process.
Data integrity checks are particularly important when it comes to sensitive information, such as personal data or financial transactions. By using these checks, organizations can ensure that the data being transmitted through their VPG is secure and has not been tampered with.
- Data integrity checks are often performed at multiple points along the network, including at the VPG itself, as well as at the firewall and VPN server.
- The encryption protocols used in a VPG, such as IPSec or SSL/TLS, also play a role in ensuring data integrity. These protocols encrypt the data before it is transmitted, making it more difficult for unauthorized parties to access or modify.
- Cloud providers that offer VPG services often have robust security measures in place, including data encryption and regular audits, to ensure the integrity of their customers’ data.
In summary, data integrity checks are an important component of a VPG’s security measures. By using cryptographic algorithms, checksums, and other methods, organizations can ensure that the data being transmitted through their VPG is secure, authentic, and free from tampering or corruption.
Routing data to the destination
When it comes to routing data to the destination in a virtual private gateway, there are a few key components at play.
Firstly, the virtual private gateway acts as a server that connects the user’s secure network to the cloud provider’s network. This connection is established through a secure encrypted tunnel, ensuring that data is kept private and protected from unauthorized access.
The virtual private gateway also performs routing functions, using protocols such as BGP (Border Gateway Protocol), to direct traffic between the user’s private network and the internet or other networks. This allows for efficient and reliable communication between different parts of the network.
Additionally, the virtual private gateway provides a layer of security by acting as a firewall. It can inspect incoming and outgoing traffic, filtering out any malicious or unauthorized activity. This helps to maintain the integrity and confidentiality of the data being transmitted.
Authentication is another important aspect of routing data through a virtual private gateway. Users or devices attempting to access the network must provide valid credentials, ensuring that only authorized individuals or systems can establish a connection.
Overall, the virtual private gateway plays a crucial role in routing data securely and efficiently within a network. It provides a secure tunnel for data transmission, performs routing functions to direct traffic, acts as a firewall for security purposes, and ensures that only authorized users can access the network.
When Should You Use a Virtual Private Gateway?
A Virtual Private Gateway (VPG) is a network component that allows you to establish a secure and private connection between your on-premises network and the virtual private cloud on the provider’s infrastructure. It serves as the entry point for all your internet traffic and provides various benefits for your network infrastructure.
One of the main use cases for a Virtual Private Gateway is when you want to securely connect your on-premises server to the cloud. By creating a VPN tunnel between your server and the VPG, you can ensure that your data is transmitted securely over the internet. This is especially important when dealing with sensitive information or compliance requirements.
Additionally, a Virtual Private Gateway can enhance the security of your network by acting as a firewall. It allows you to set up routing rules to control the flow of traffic between your on-premises network and the virtual private cloud. You can also apply encryption and authentication protocols to further secure your data and prevent unauthorized access.
Another situation where a Virtual Private Gateway can be beneficial is when you have multiple virtual private clouds within your provider’s infrastructure. In this case, the VPG acts as a central hub, allowing you to establish connections between different virtual private clouds. This enables efficient communication and data transfer between the various components of your network.
In summary, you should consider using a Virtual Private Gateway when you need to establish a secure connection between your on-premises network and the provider’s virtual private cloud. It provides enhanced security, enables efficient communication between network components, and ensures the privacy and integrity of your data. Whether you are looking to connect a single server or multiple virtual private clouds, a VPG can be a valuable tool in your network infrastructure.
Connecting multiple networks
A Virtual Private Gateway (VPG) is a virtual networking component that allows you to connect multiple networks together. It acts as a tunnel between these networks, enabling secure and efficient communication.
In cloud computing, a VPG serves as a central point for connecting various networks, such as on-premises networks, virtual private clouds (VPCs), and other cloud service provider networks. It provides a secure connection between these networks, ensuring data privacy and facilitating effective data exchange.
One of the key advantages of using a VPG is enhanced security. By establishing a secure connection between networks, you can protect your data from unauthorized access, interception, and tampering. This is achieved through encryption, where data is encoded and can only be decoded by the recipient using a specific key.
Furthermore, a VPG enables efficient routing of network traffic. It acts as a gateway for routing traffic between networks, determining the most optimal path for data transmission. This helps to minimize latency and ensure fast and reliable connectivity between different components of the network.
A VPG also provides access control and firewall capabilities. It allows network administrators to define and enforce rules for network access, ensuring that only authorized users and devices can connect to the network. This helps to prevent unauthorized access and protect sensitive data from potential threats.
Additionally, a VPG supports various protocols, including Virtual Private Network (VPN) protocols, which are used for establishing secure connections over the internet. By utilizing VPN protocols, a VPG enables secure and encrypted communication between networks, even over public internet connections.
In summary, a Virtual Private Gateway plays a critical role in connecting multiple networks together. It provides secure access, efficient routing, and enhanced security measures such as encryption and access control. With its capabilities, organizations can establish and manage complex network architectures, ensuring seamless communication and protection of sensitive data.
Ensuring secure communication
In a virtual private gateway, security is a top priority. One of the main ways to ensure secure communication is through routing protocols. These protocols help direct traffic between different networks and ensure that data is sent and received securely.
Another important security measure is the use of firewalls. Firewalls act as a barrier between the virtual private gateway and the internet, filtering incoming and outgoing traffic to prevent unauthorized access to the private network. They can also monitor and block any suspicious activity.
A virtual private gateway also uses a secure tunnel to encrypt data as it travels between the private network and the user’s device. This tunnel, often referred to as a VPN (Virtual Private Network), ensures that data remains private and secure, even when transmitted over the internet.
Authentication is another crucial aspect of secure communication in a virtual private gateway. The gateway verifies the identity of users or devices before granting them access to the private network. This helps prevent unauthorized access and ensures that only authenticated users can connect.
In addition to these security measures, a virtual private gateway can also utilize other protocols and technologies, such as encryption algorithms and secure connections to the provider’s server. These measures help further protect the data and ensure that it remains secure throughout the communication process.
By prioritizing security and implementing these measures, a virtual private gateway enables users to securely access and transmit data within a private network, even when connected to the internet or the cloud.
FAQ about topic “Understanding the Virtual Private Gateway: A Comprehensive Guide to its Functionality and Operations”
What is a Virtual Private Gateway?
A Virtual Private Gateway is a virtual network appliance that provides a secure and private connection between a virtual private cloud (VPC) and an on-premises network. It serves as a gateway for traffic going in and out of the VPC, allowing users to access resources in the VPC securely from their on-premises network.
How does a Virtual Private Gateway work?
A Virtual Private Gateway works by establishing a secure IPsec VPN connection between the VPC and the on-premises network. This connection encrypts all traffic and allows for secure communication between the two networks. The Virtual Private Gateway also acts as a router, directing traffic to and from the VPC, and can be configured with various routing rules to control the flow of traffic.
What are the benefits of using a Virtual Private Gateway?
Using a Virtual Private Gateway provides several benefits. Firstly, it allows for secure communication between a VPC and an on-premises network, ensuring that data is encrypted and protected. Secondly, it allows users to access resources in the VPC from their on-premises network, making it easier to manage and access resources. Finally, it allows for more control over the flow of traffic, as the Virtual Private Gateway can be configured with routing rules to direct traffic.
Can a Virtual Private Gateway be used with multiple VPCs?
Yes, a Virtual Private Gateway can be used with multiple VPCs. By configuring the Virtual Private Gateway to connect to multiple VPCs, users can establish secure connections between the VPCs and the on-premises network. This allows for easy communication between the VPCs and simplifies network management.
What are the alternatives to using a Virtual Private Gateway?
There are several alternatives to using a Virtual Private Gateway. One alternative is to use a software-based VPN solution, which can provide similar functionality but without the need for a dedicated appliance. Another alternative is to use a Direct Connect service, which allows for a dedicated network connection between the on-premises network and the VPC. However, these alternatives may have different costs and configurations compared to a Virtual Private Gateway, so it is important to consider the specific requirements and constraints of the network.


