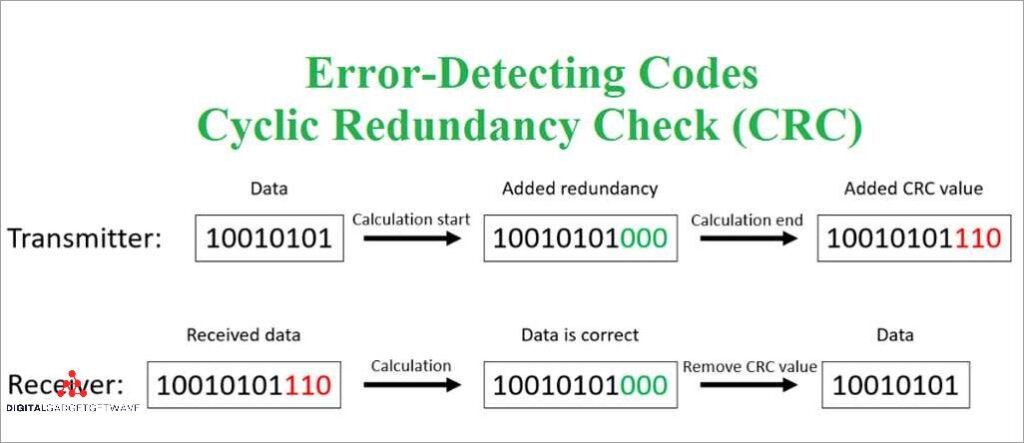
Understanding the Importance of the Cyclical Redundancy Check (CRC) Algorithm
The cyclical redundancy check (CRC) algorithm is a widely used method for error detection in digital data transmission. It is a type of checksum that detects errors by performing a calculation on the data and comparing the result to a predetermined value. The CRC algorithm is known for its simplicity and efficiency, making it a ...