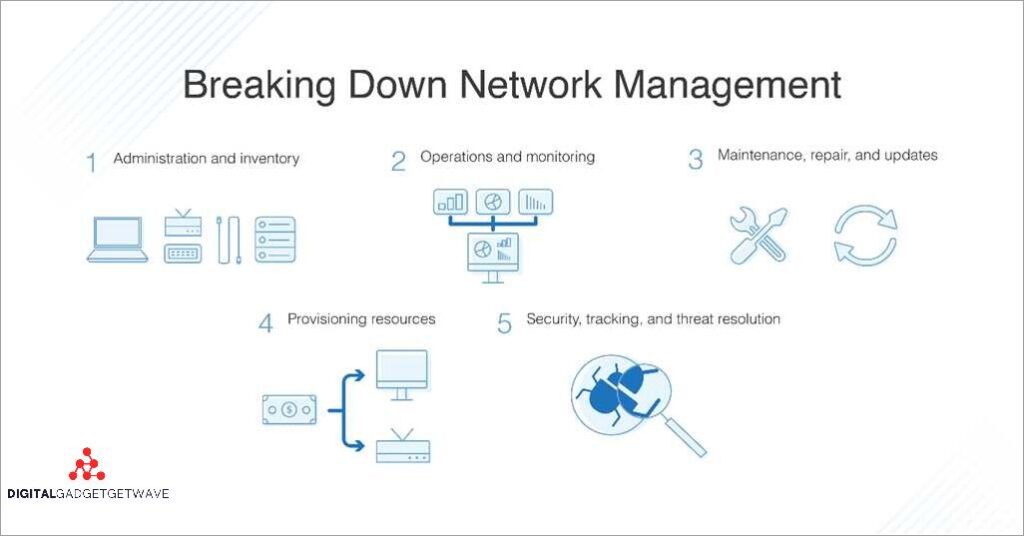
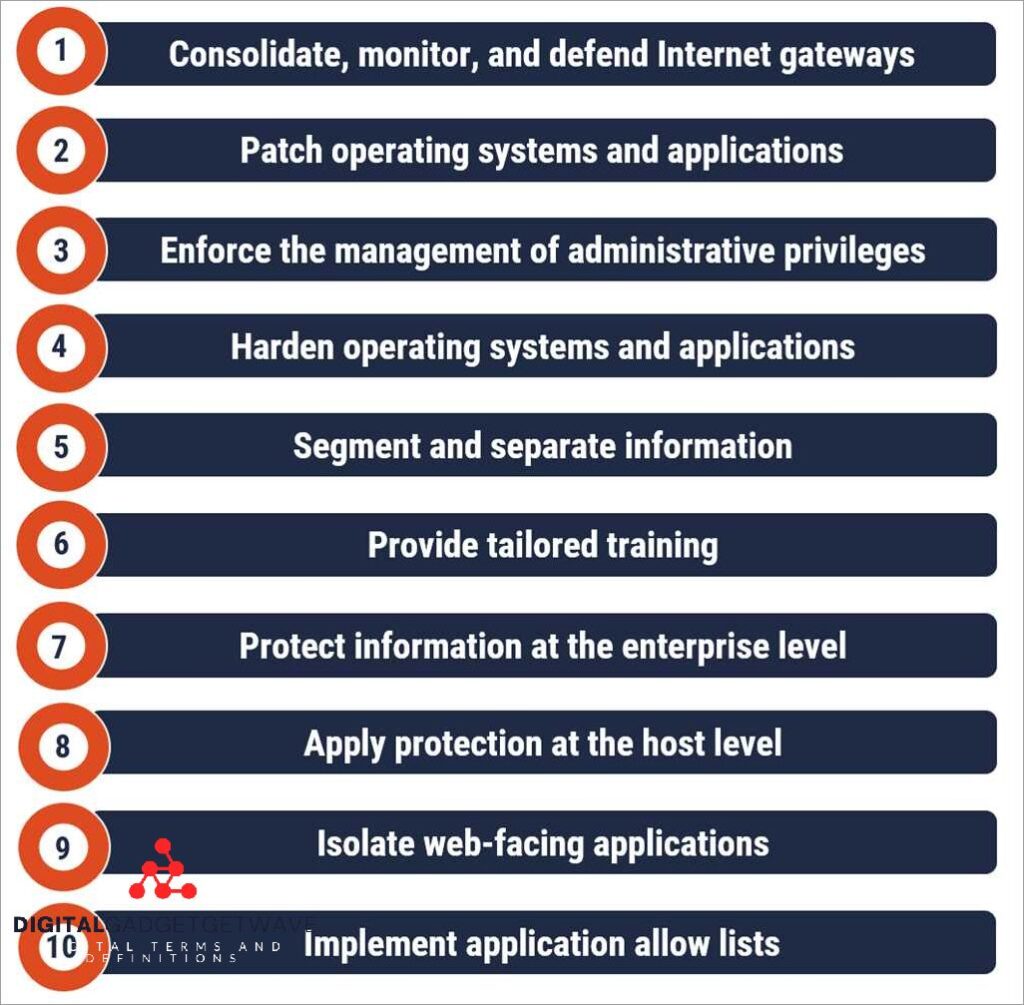
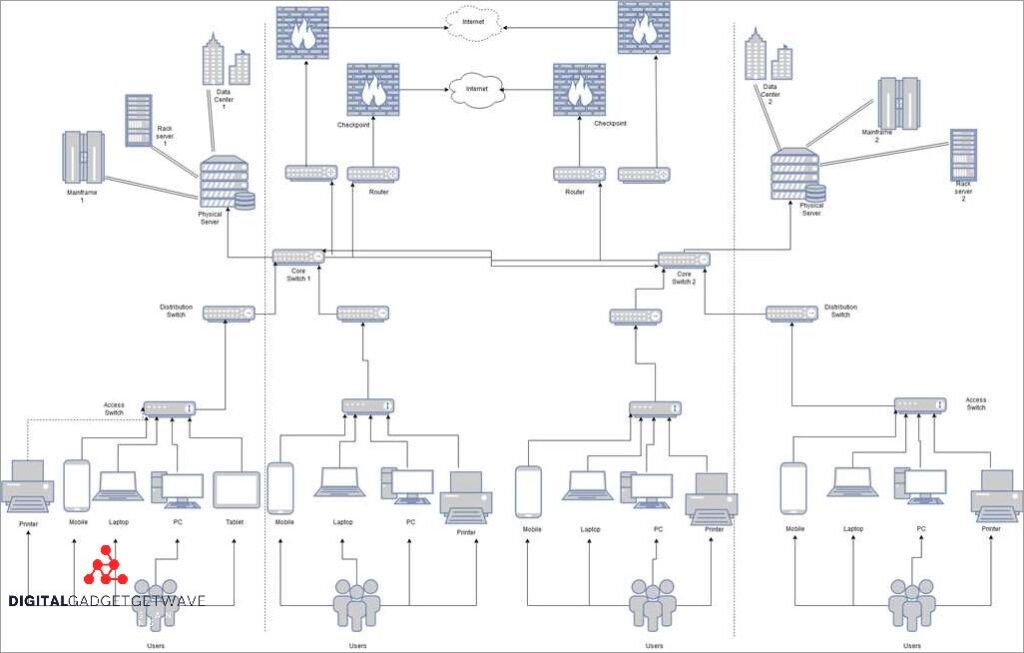
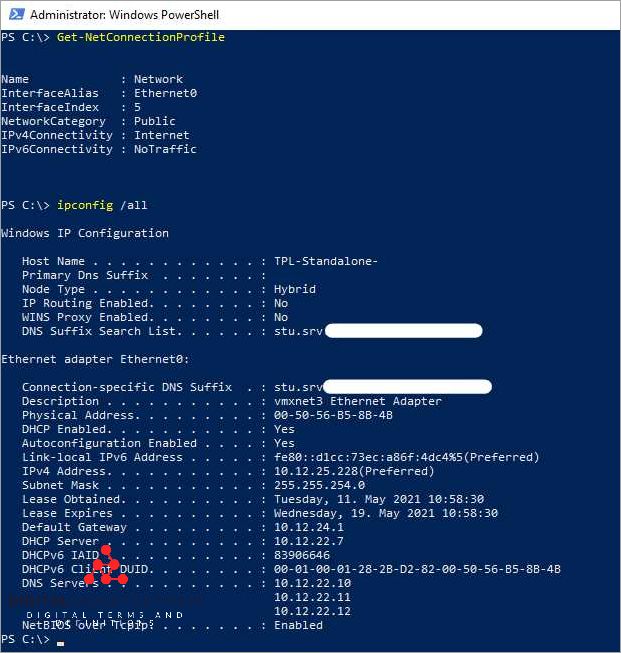
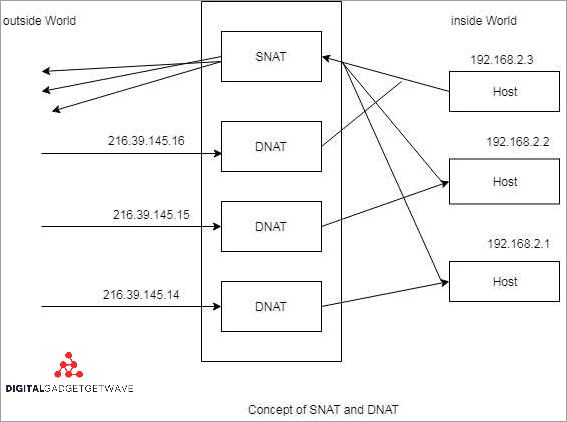
Enhance Your Network Security with Effective Network Administration Practices
Network security is a critical aspect of any organization’s IT infrastructure. With the increasing prevalence of cyber threats, it is essential for businesses to adopt effective network administration practices to protect their sensitive data from unauthorized access and prevent potential security breaches. Implementing these practices can help organizations ensure compliance with industry regulations and protect ...